Microsoft 365 Cloud Security correlation
If you ask me, Microsoft's biggest advance and unique selling point in terms of security is the diversity of their feature offerings tied to the non-security products and the correlation between them. Always backed by the ability to retrieve all kinds of data from the past or in real time, it is clearly a state-of-the-art security system.
The real challenge is that all events in information technology happen on and between different, most of them independent systems. This makes it pretty hard to understand lateral, multi-staged actions that involves interfaces between product categories.
SIEM (security information and event management) products would fulfill this requirement, although it can be hard to connect all data-generating systems. Another aspect is to correlate these events and obtain effective and useful information output from them, which SecOps would use.
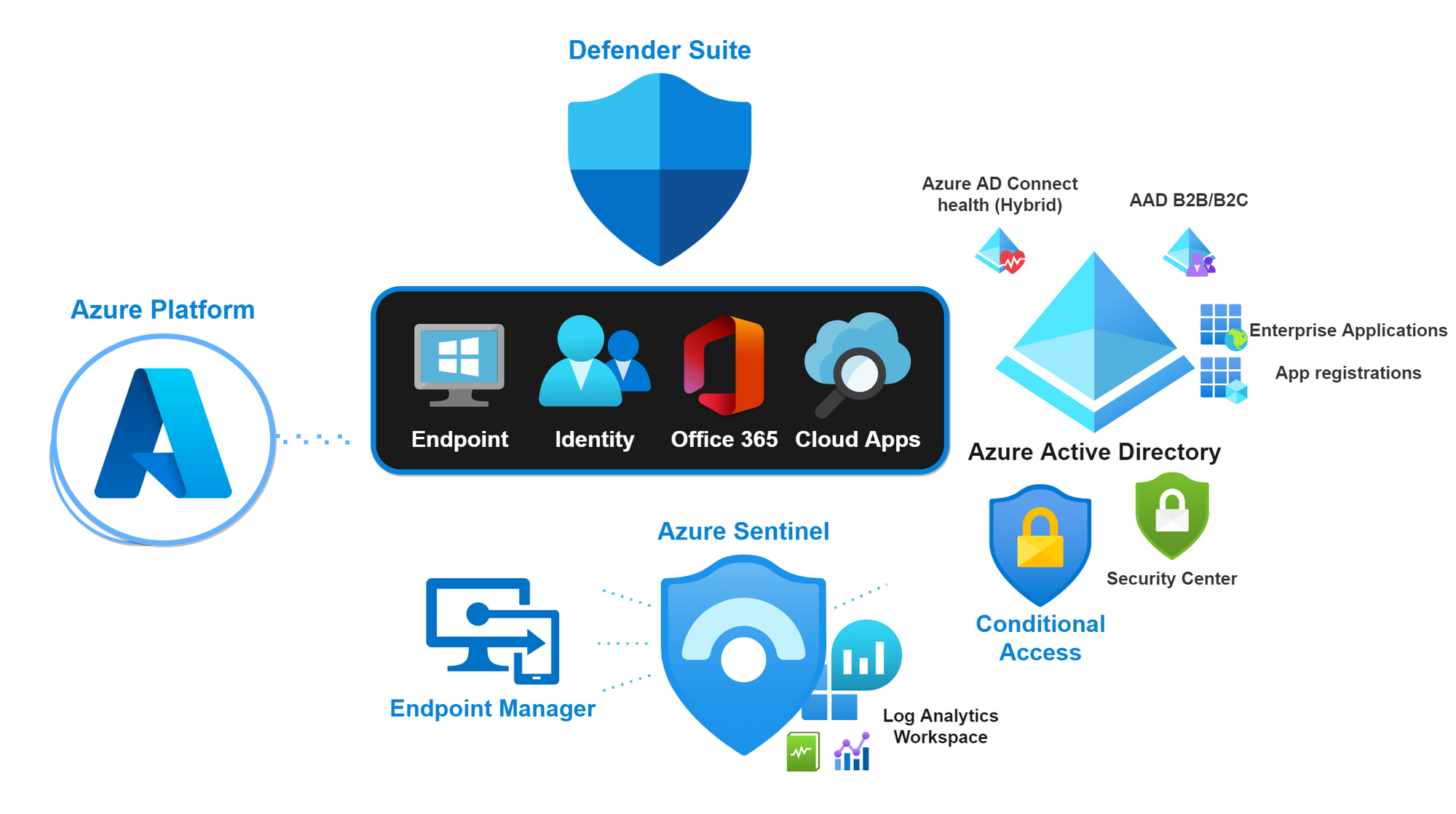
Microsoft is aware of these challenges and therefore presents a cloud that acts as a huge orchestration system that is homogeneous. Since all services are on the same platform, it is easier to link (security related) workloads. This landscape looks like this:
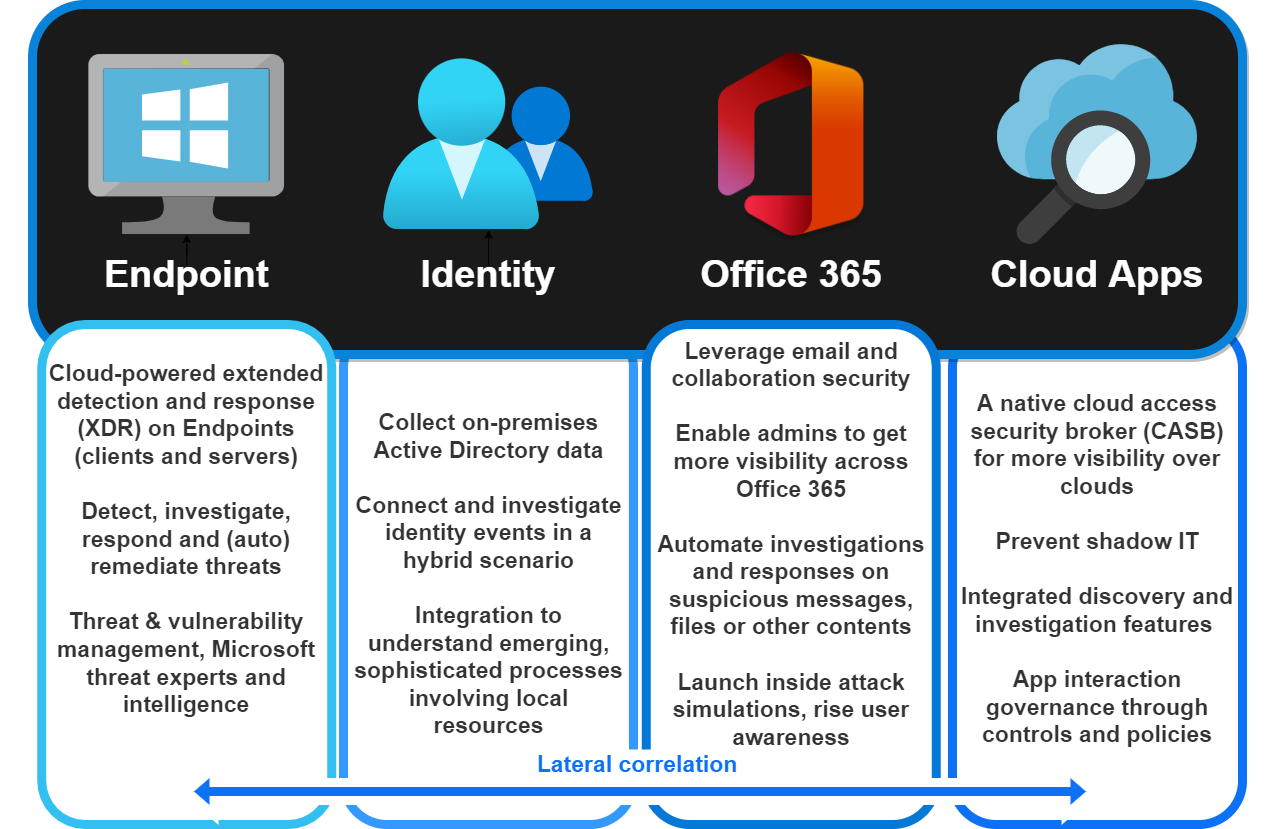
Defender Suite
The heart of every Microsoft 365 orientated organization is the Microsoft Defender Suite to fight against cyberthreats. Resulting in a Defender product for:
| Product name | Use | Reference on Oceanleaf.ch |
|---|---|---|
| Endpoint | Extended detection and response on Endpoints (XDR) | Microsoft Defender: a review |
| Identity | Connect on-premises identity events | Defender for Identity fundamentals |
| Office 365 | Leverage email & collaboration security | Defender for Office 365 fundamentals |
| Cloud Apps | Cloud access security broker (CASB) | A tour through Defender for Cloud Apps |
Azure Active Directory
Azure Active Directory as a cloud-based identity and access service is the first security perimeter to Microsoft 365 apps and resources.
| Product name | Use | Reference on Oceanleaf.ch |
|---|---|---|
| Azure Active Directory | Cloud-based identity provider (IdP) | Into Azure Active Directory |
| Conditional Access | Access control through signals | Important aspects to conditional access |
| Enterprise Application and App registrations | Collaboration to other cloud SaaS | Understanding identity federation and application management in Azure AD |
| AAD Identity Protection | Evaluate user and sign-in risk based on different criteria | - |
Microsoft Endpoint Manager
Managing Endpoints is crucial to every organization. Mobile device management (MDM) and mobile application management (MAM) covers protecting corporate resources on any device or application.
Dangers and remediations
Endpoints are highly likely to be involved in lateral movements, as they often are affected by vulnerabilities or exposures in the operating system or installed applications. Antivirus/Disk encryption/Firewall/Endpoint Detection & Response/Attack Surface Reduction/Account Protection with additional Defender for Endpoint is the remediation approach to this concerns.
View all resources to Microsoft Endpoint Management with Intune
The benefits of Microsoft
- Hybrid capabilities - on-premises based organizations profit of the hybrid constellation and can combine both resource providers
- Service jungle - all the offered services range from compute, networking, storage, web to analytics, AI, ML, IoT, Identity and Security - there is a service for every need or requirement - and these communicate among themselves
- Globalization & unification - when a large number of users feed data into a given system, it is only natural that it can get better by providing more information and responding to events in a compliant and effective way
All contents from Microsoft Defender
More about M365 security
Microsoft 365 Defender
Microsoft 365 Defender portal is the place where all Defender products come together and form a single pane of glass experience. The site includes the following feature set/navigation (April 2022):
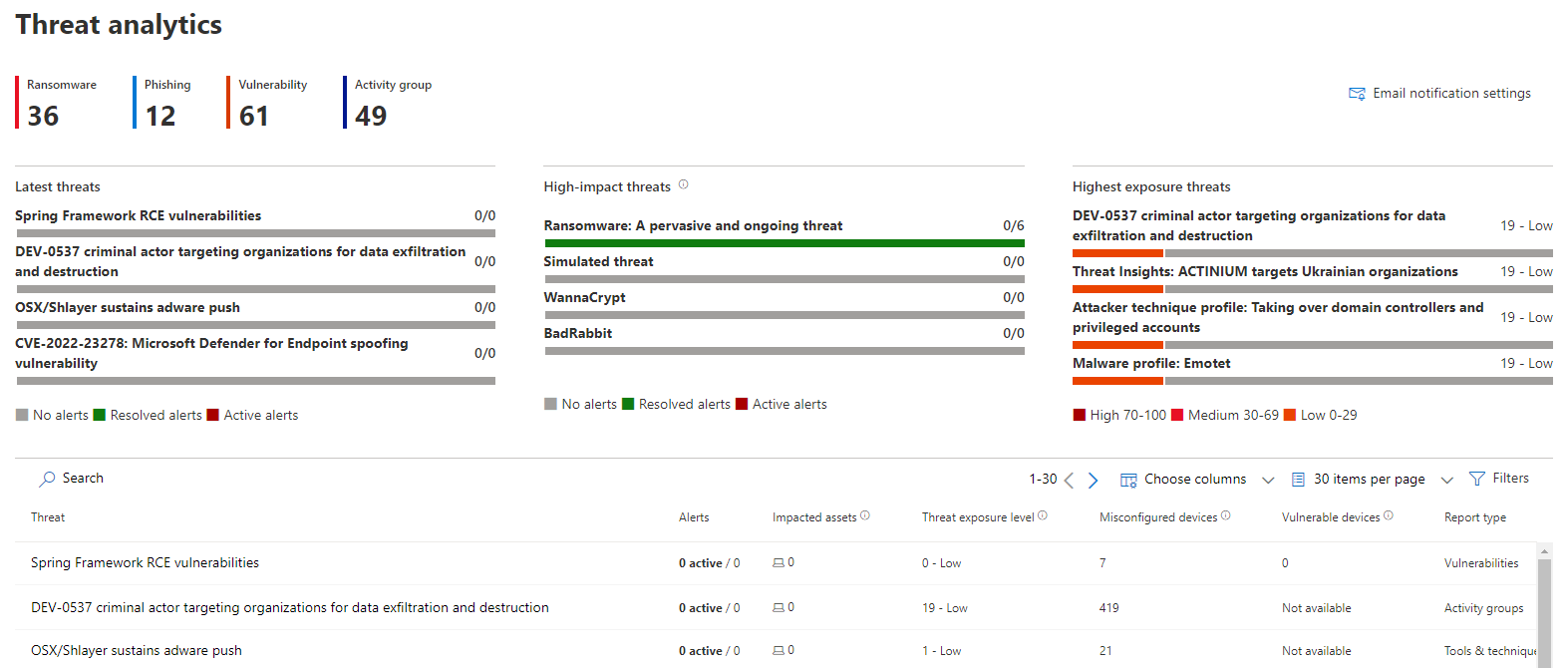
Threat analytics
Microsoft Advanced Threat Analytics (ATA) an integrated listing of current or past
security threats that have been identified around the world and in other organizations. You can see enhanced data from Microsoft security intelligence - all the information about IT security that is collected by Microsoft, its partners and data.
The core competence of this product is that all incidents, security holes or vulnerabilities in organization are resolved according to these threat analytics. Now, if evidence is found that an enterprise device has been compromised, the information can be correlated and Microsoft will provide information on how to remediate or prevent such threats.
Threat insight
For each of these threat types (usually also CVE), a whole range of information is provided. From an overview, to a detailed analysis report, to the assets sourced and impacted, as well as prevention measures and vulnerability mitigations, everything is everything is available in the same portal.

Incident
Incidents & alerts are then created by Microsoft 365 Defender and include:
| Information type | Application |
|---|---|
| Incident name | Name of a security event |
| Incident Id | Unique identifier |
| Tags | User/device/app tag (custom) |
| Severity | Low/Medium/High classification |
| Investigation state | Amount of investigation processes/current state |
| Categories | Threat category (attack pattern) |
| Impacted assets | User/device/app, resources that are involved |
| Active alerts | Related (active) alerts to this incident |
| Service Sources | Related Microsoft Security product where the source of attention was |
| Detection Sources | Related detection within Microsoft Security product/detection method |
| First activity | Time, date on which the first event related to the incident occurred |
| Last activity | Time, date on which the last event related to the incident occurred |
| Data sensitivity | Information protection/compliance |
| Status | New/In Progress/Resolved |
| Assigned to | Assigned security employee |
| Classification | True alert/false positive |
| Determination | Classification of event |
| Device groups | Related Defender for Endpoint device group |
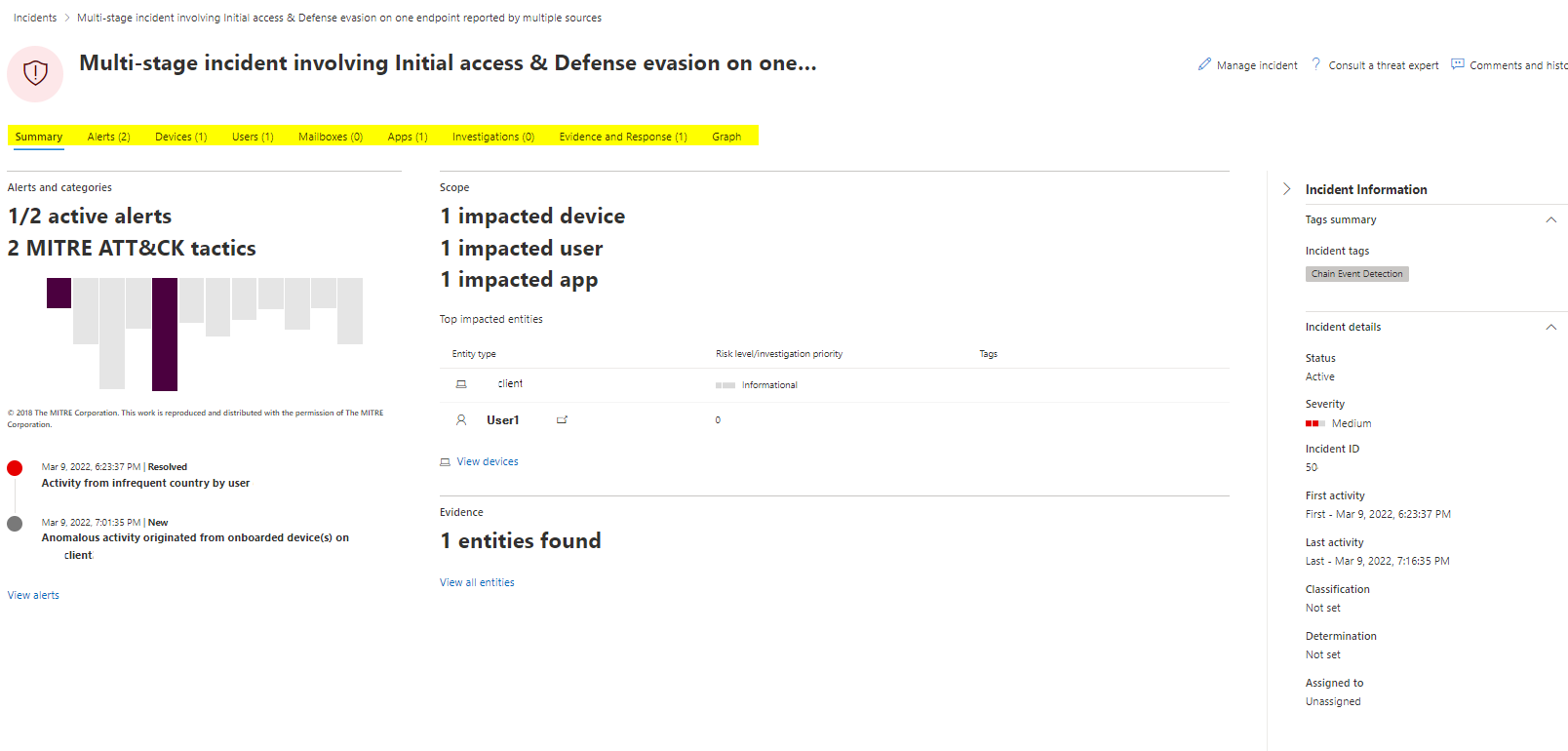
Incident overview
Let's take a look at an Incident sample. The overview shows the MITRE ATT&ACK tactics and corresponding alerts. Next to it we can see the scope (impacted assets) and the evidence for the incident. At the right pane there is general information displayed. At the top bar we can navigate between different aspects of this case including:
- Summary
- Alerts
- Devices
- Users
- Mailboxes
- Apps
- Investigations
- Evidence and Response
- Graph
Alerts
The alerts pane allocates all alerts and key information from Microsoft 365 Defender, that was involved by the incident. Notice the "Open alert page" button, where you can follow this alert and see more detailed information to it.
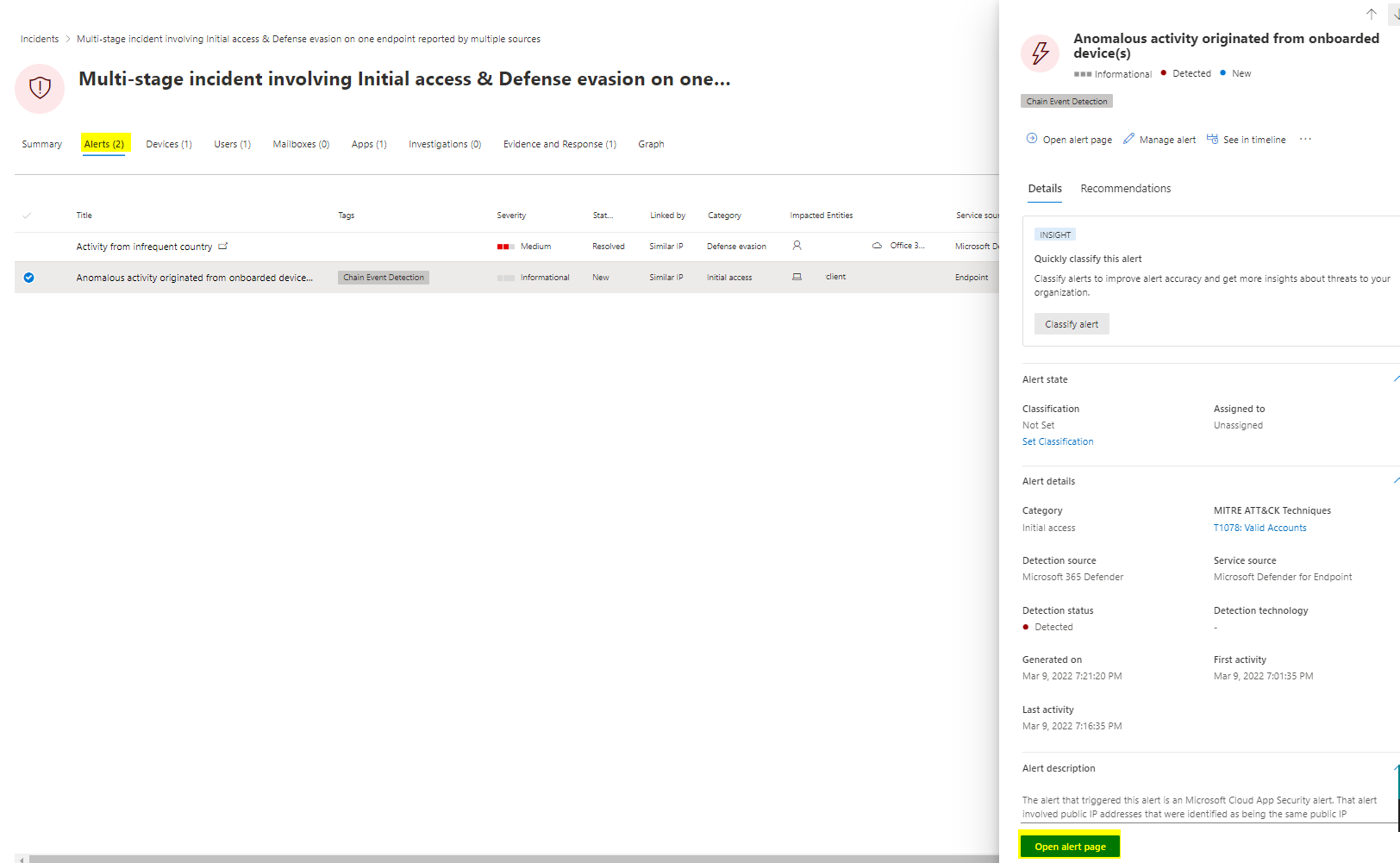
Devices
In the devices pane, all devices linked to the incident from Defender for Endpoint show up.
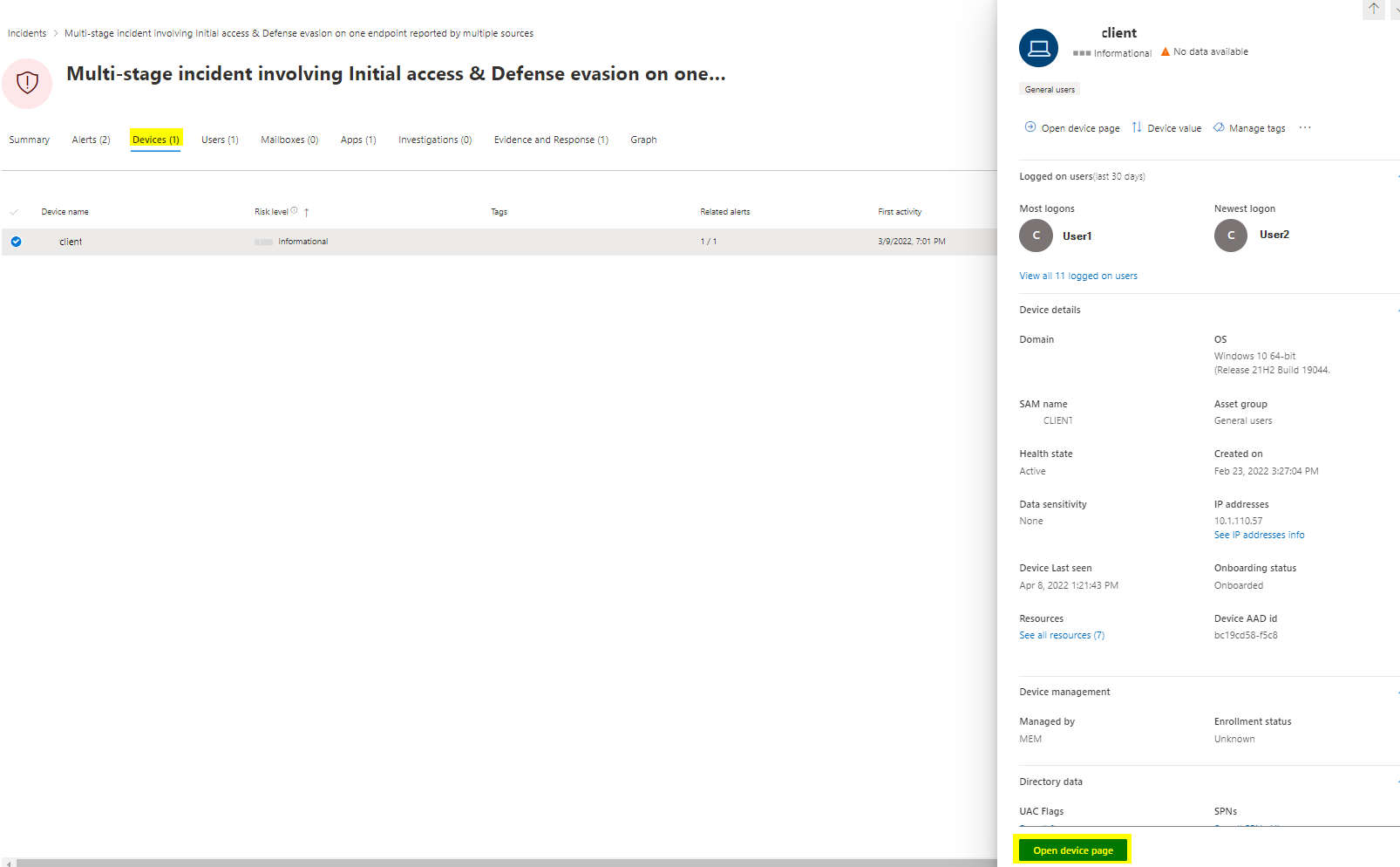
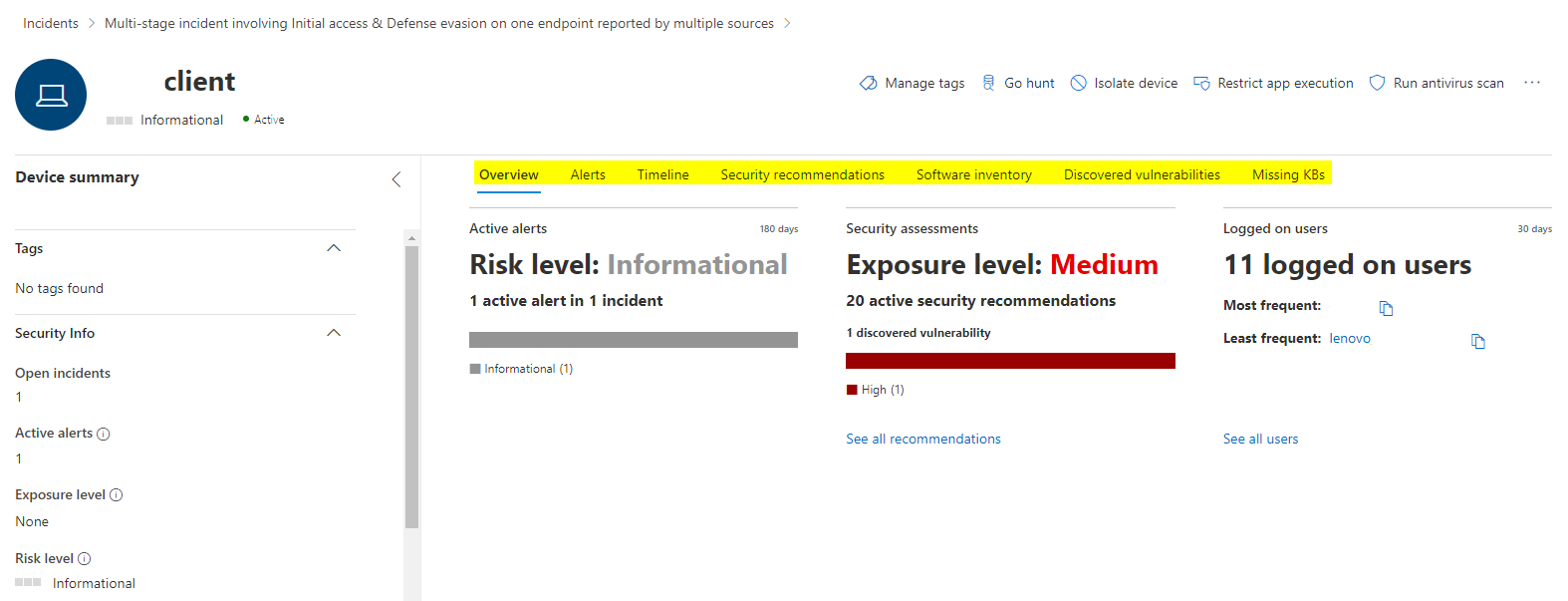
Also here we can open the device page and will get forwarded to the device from Defender for Endpoint and more sources.
Users
Users mainly focuses on Azure AD identity events and uses data from other services such as Defender for Identity or AAD Identity Protection.
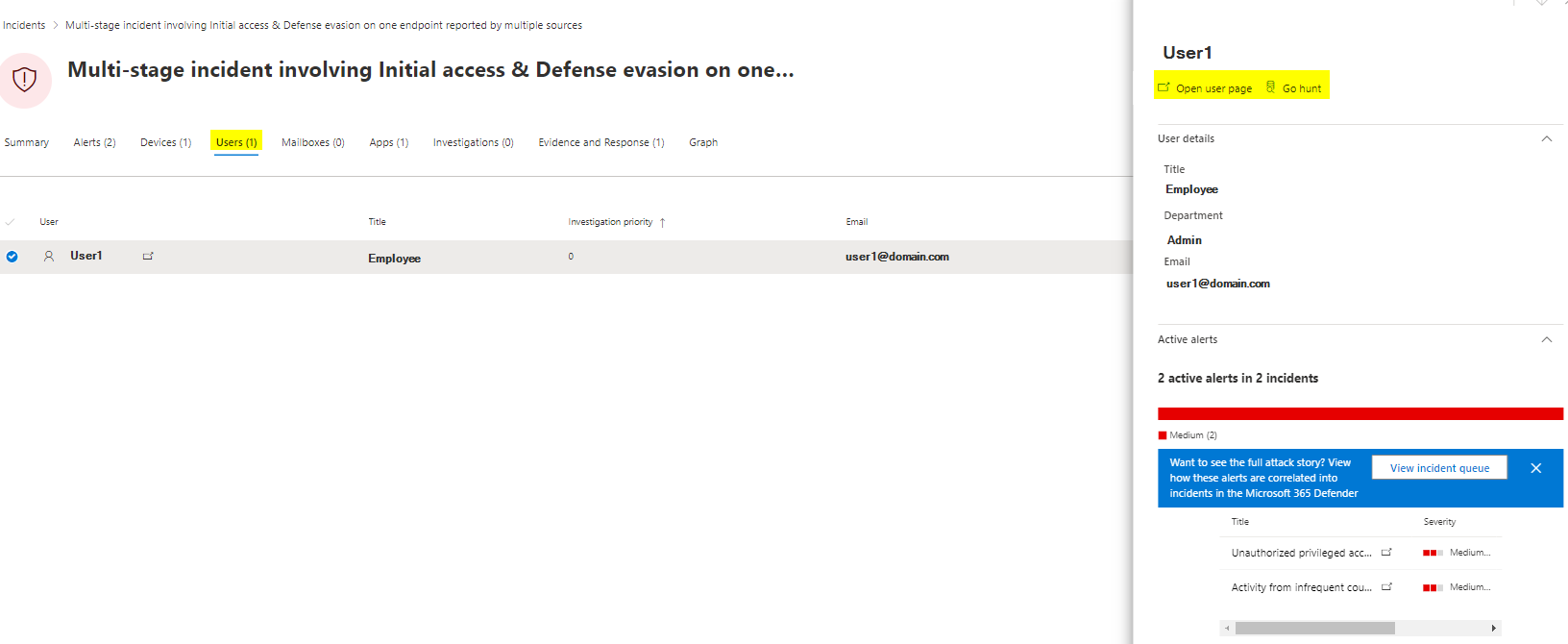
If you click on "Go hunt" then, Advanced hunting with the predefined querry will be opened up.
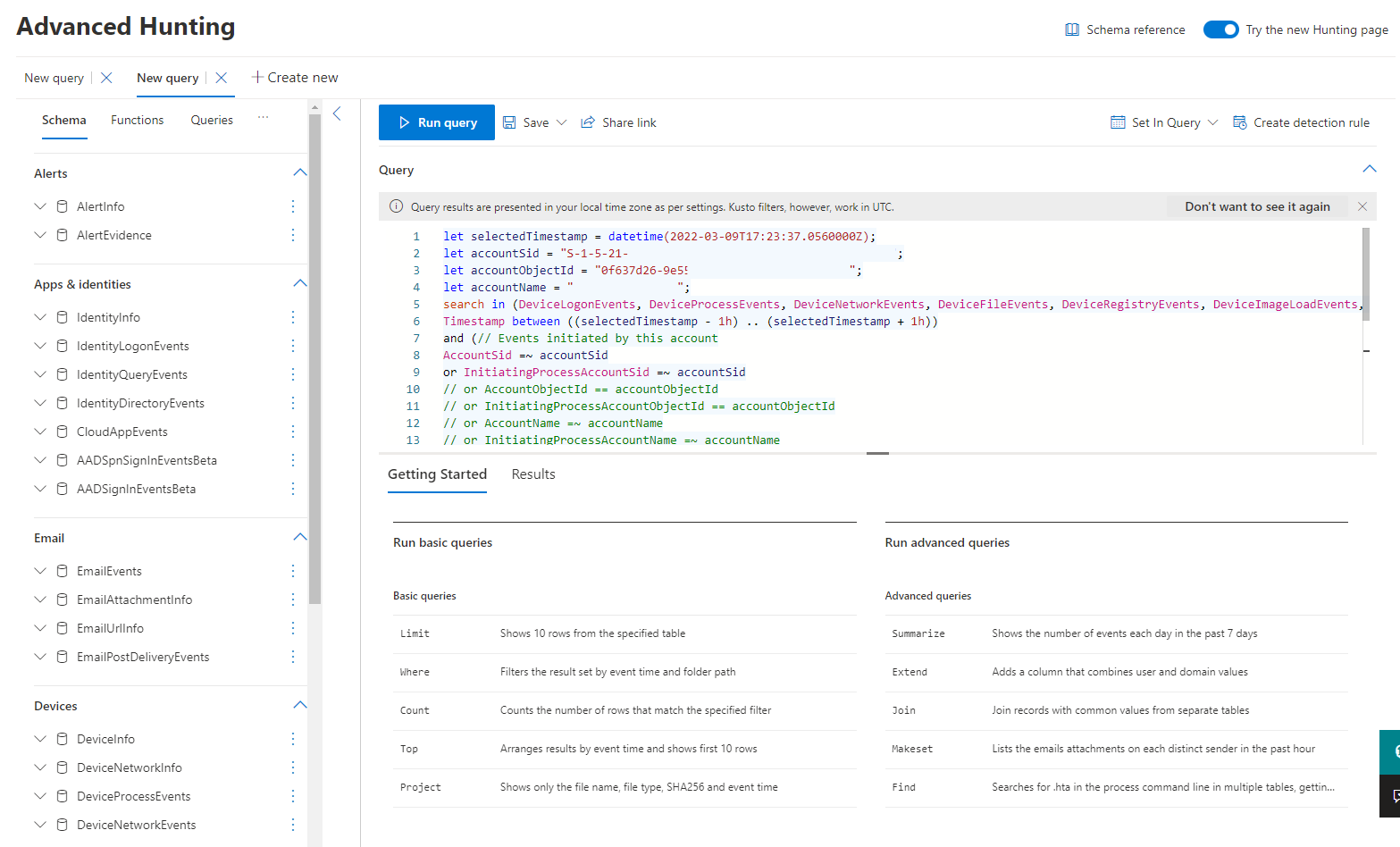
Apps
Defender for Cloud Apps is the component where the (cloud) app is correlated with.
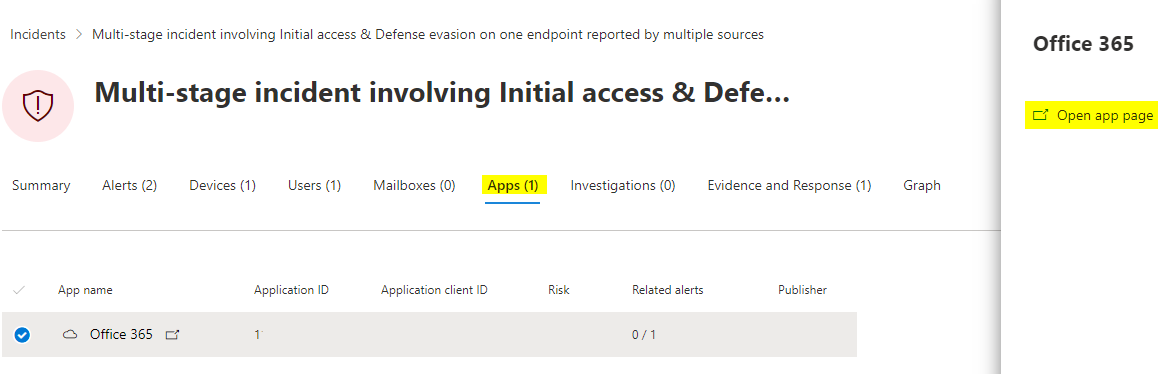
The app page will then be opened and further investigation or governance operations are available.
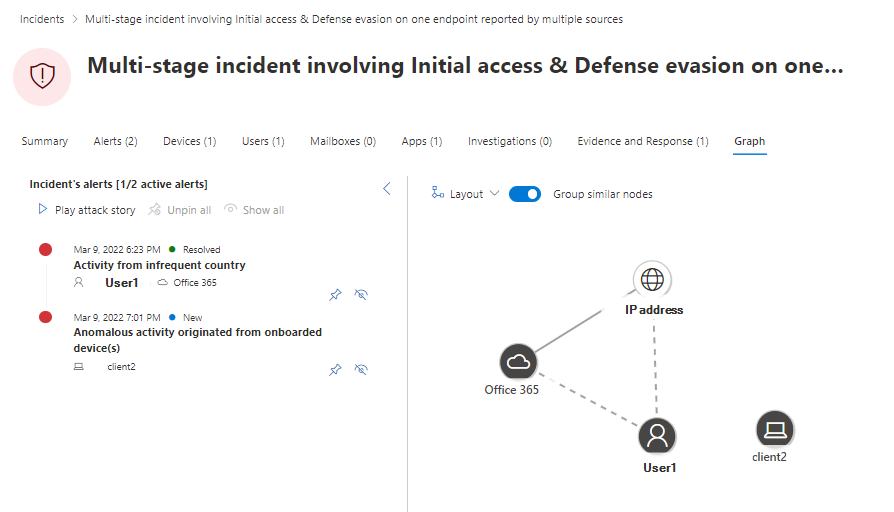
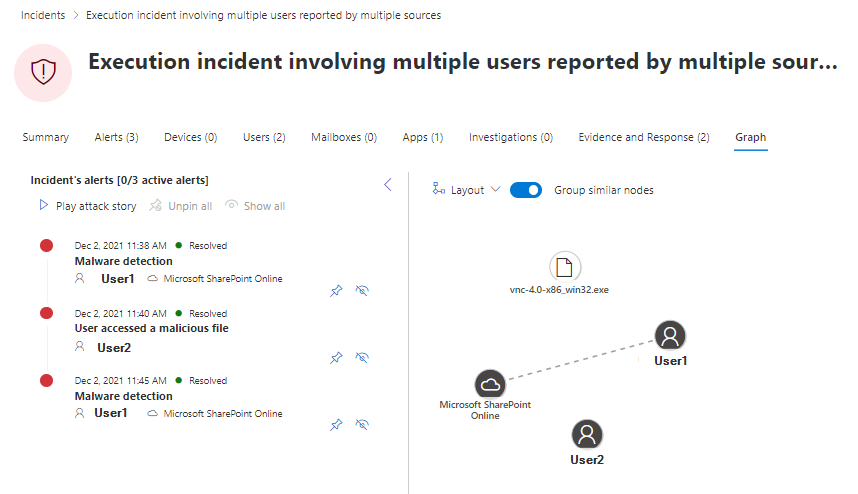
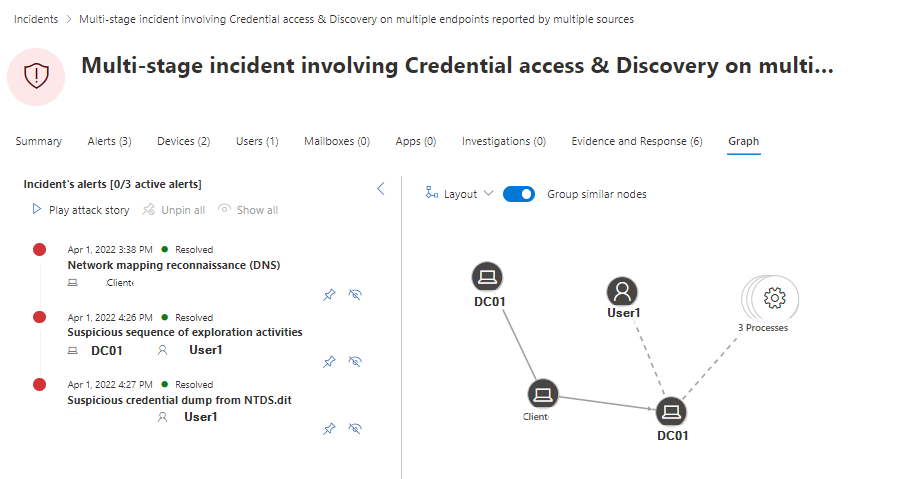
Graph samples
I would like to present some various Graph's as I think they are one of the most powerful tools for understanding the incident. The assets are listed and connected and could be a lateral type of identity, device, app or data.