Defender for Cloud Apps: some concepts and how to get started
Beside Defender for Cloud Apps as a product, which is featured in this post, my intention is to give more operational insight and a guide to successfully understand, plan and run Microsoft Defender for Cloud Apps. Before reading this, I would highly suggest to read the first post.
Solution overview
So what is Defender for Cloud Apps? It is here as:
- A native Cloud access security broker (CASB)
- Cloud app discovery platform that fetches data from Defender for Endpoint or Firewall logs
- Granular control interface of collaboration and access to SaaS (Software as a service) apps in the web (security and compliance enablement)
- Decentralized / cloud-based solution where the security perimeter is built-in the Defender Suite
Architecture
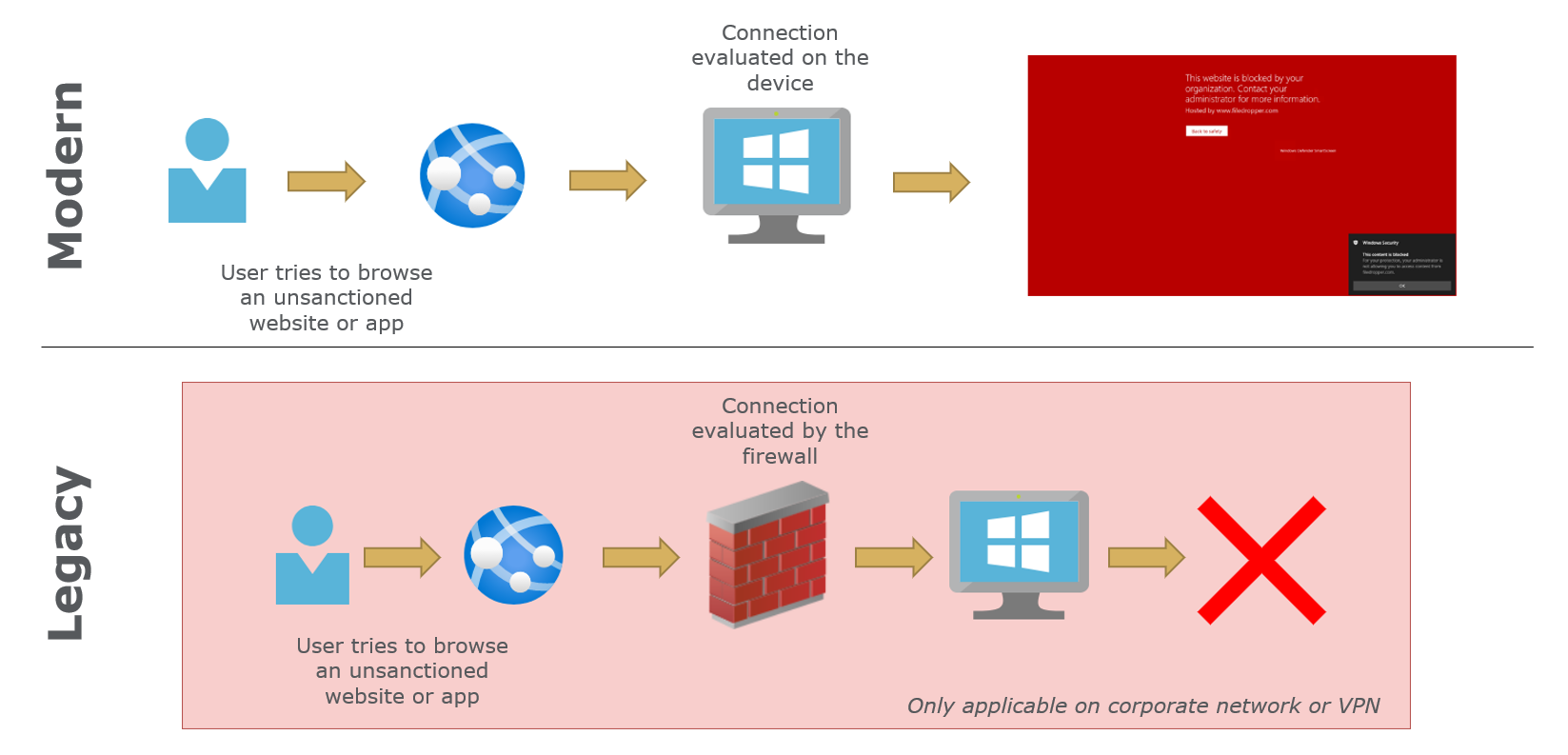
The modern vs. legacy approach on network controls differentiate through a central component, the firewall, which in the legacy flow was needed to control connections from a client. The modern approach is that connections are evaluated on the device and thus independently of the network.
(https://oceanleaf-1.ghost.io/content/images/2022/03/dfca-architecture-legacy-modern.png)
What are Cloud Apps?
The challenge consists of thousands of Cloud applications and websites that users need for collaboration. Shadow IT describes non IT-personnel, that interacts with separate accounts (no SSO or central IdP) on cloud infrastructure/apps that the organization utilizes. The problem is, that the IT department has no governance over these actions and lacks of security and compliance.
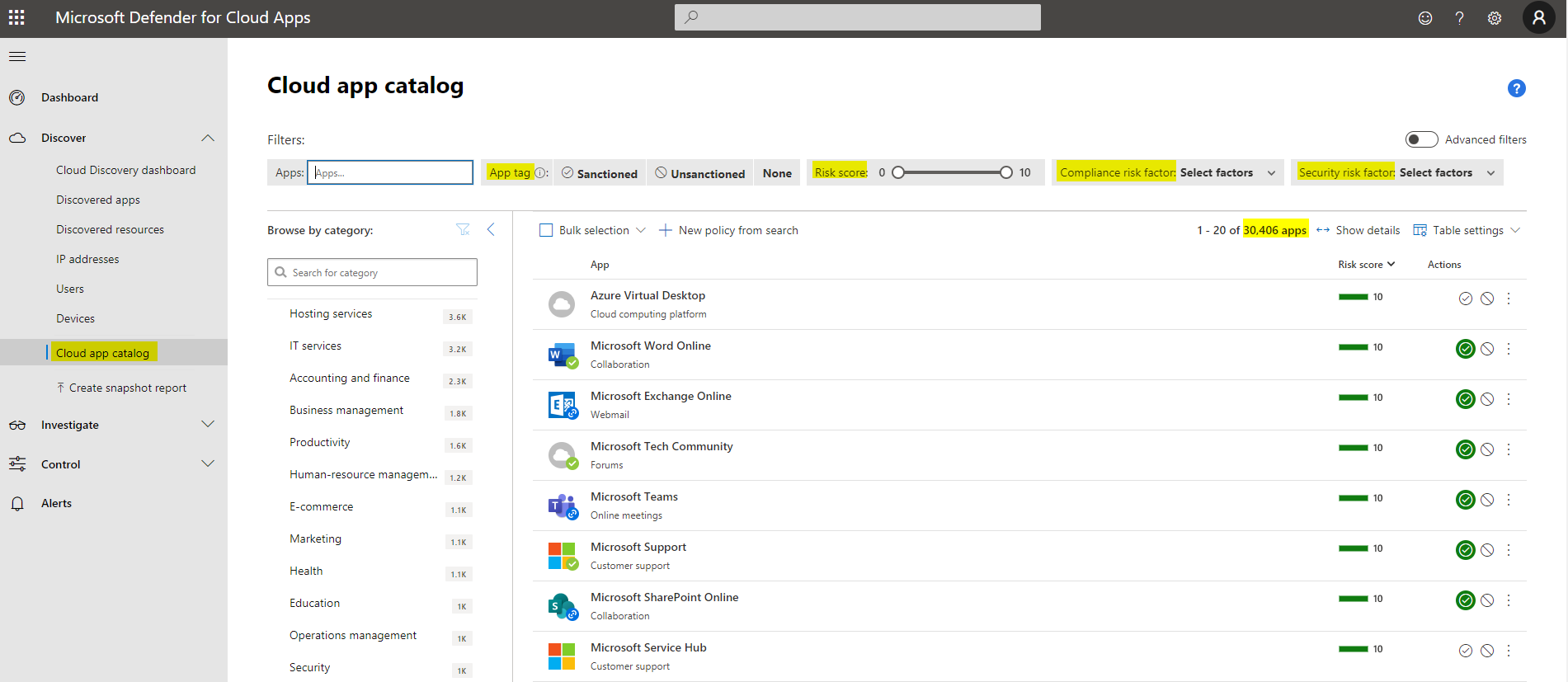
Cloud App catalog
Microsofts own database of discovered apps in the web has over 30'000 entries. (March 2022) They are added on the go.
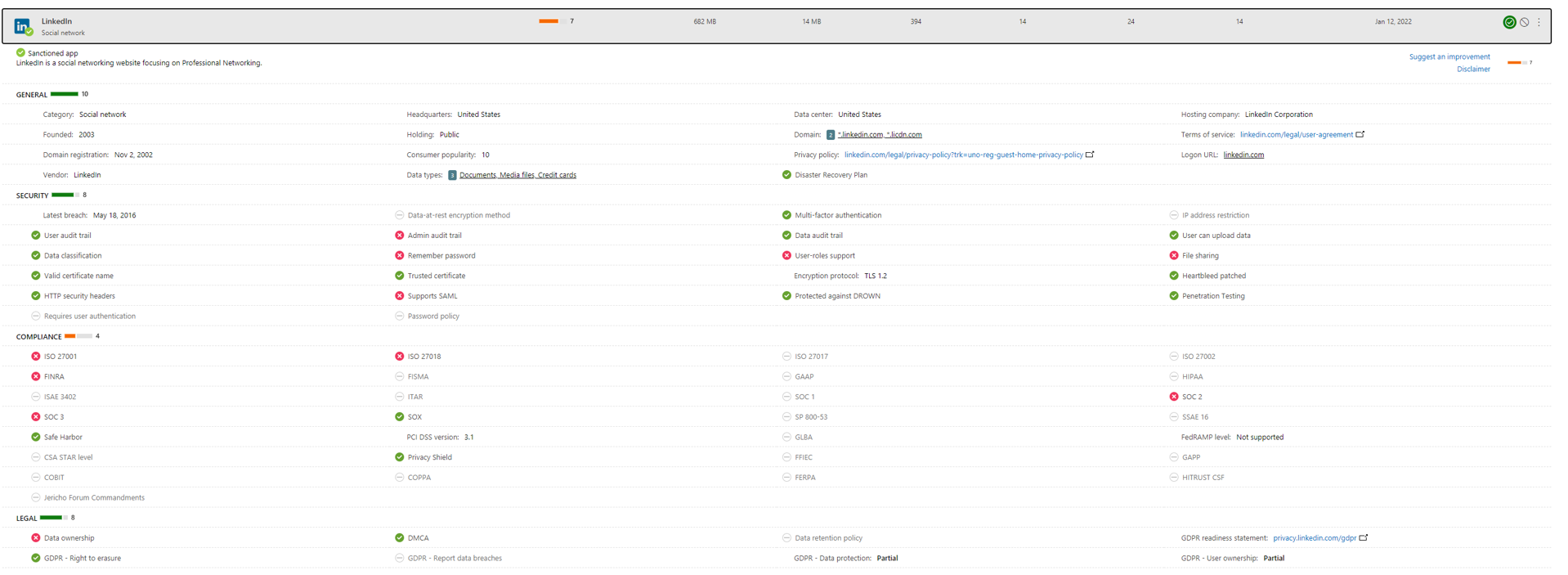
Each app (example LinkedIn) has a lot of information assigned, such as general information, security related data and governance standards. As you can see, there is a lot of useful information that an ordinary consumer might never have known.
How to make it work
You may ask yourself what to do with this data. Usually in later step policies are enforced to strictly define which attributes of a cloud app are relevant or even required before accessing an app. Score metrics can be configured to individual preferences and importances. Furthermore session controls work with Conditional Access.
App tags
Apps can be tagged as:
- Sanctioned - app is generally allowed and accessible
- Unsanctioned - app is generally not allowed and might be not accessible
- Monitored - app is under special observation, user receives a corresponding notification, that the access to this app is monitored
- Individual tag - individual, for utilization in own policies
App risks score
Each cloud app is rated by Microsoft by an individual risk score to:
- Scores from 0 (worst, harmful) up to 10 (best, harmless)
- App scores can be used to identify unwanted or malicious apps
- Score metrics can be configured to own concerns, but Microsoft raises data and provides default score metrics
- Block access to apps under a certain score (with Defender for Endpoint integration)
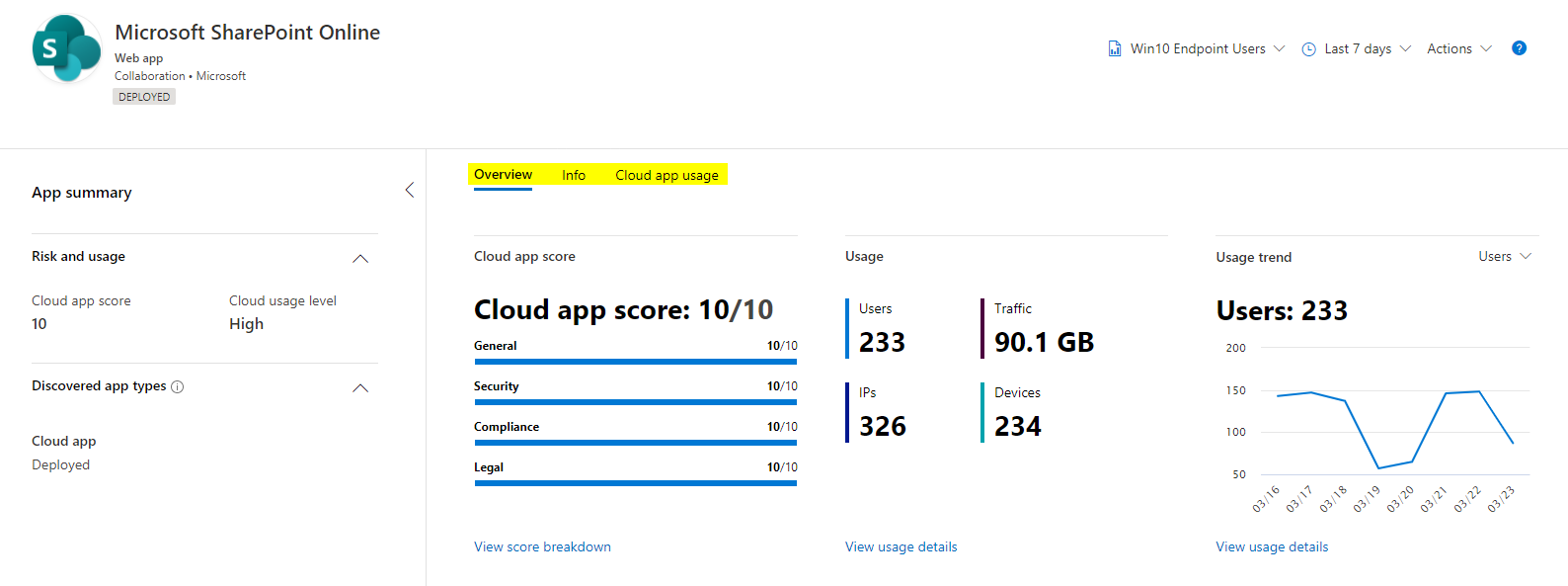
Discover a cloud app
If we take a look at an example, we can see an overview of the app with information about users, devices, IPs and traffic.
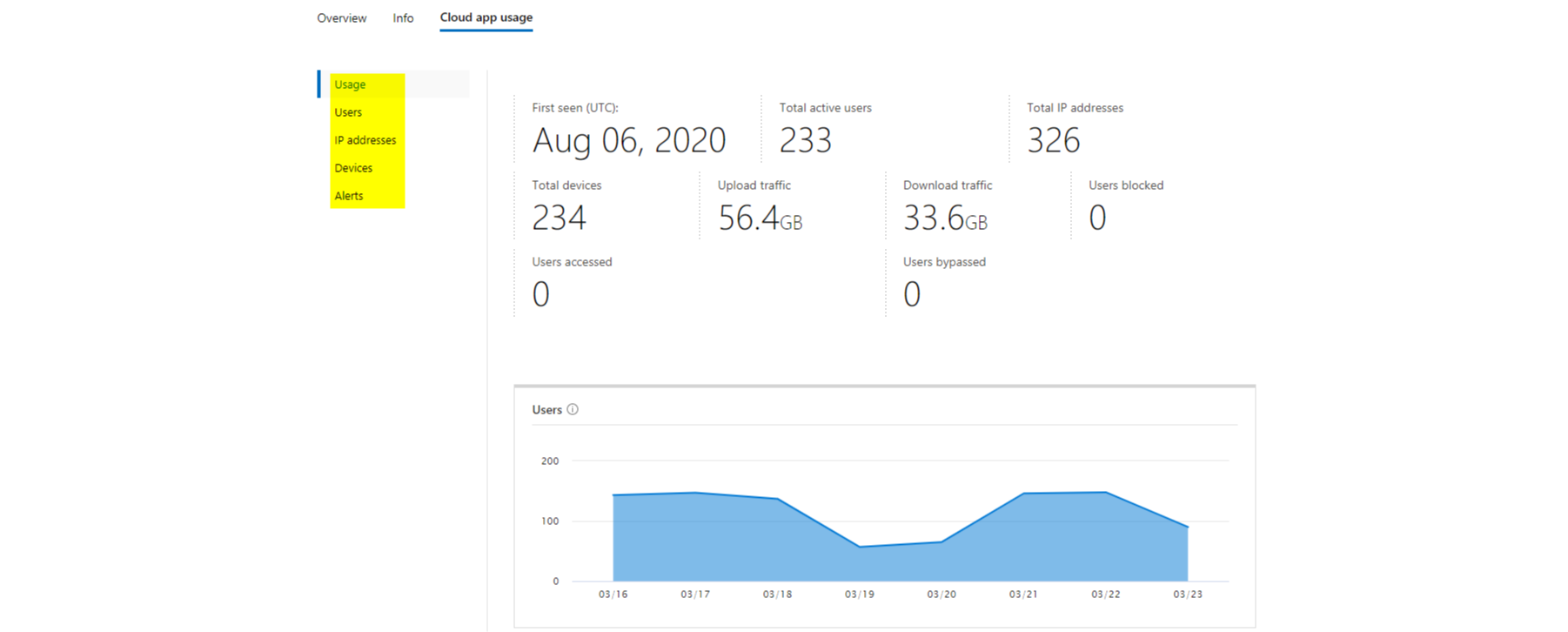
The usage is always displayed in a chart over time and has some extra information. This should help you to understand your environment and the behavior of users. Especially traffic of down- and uploads are crucial.
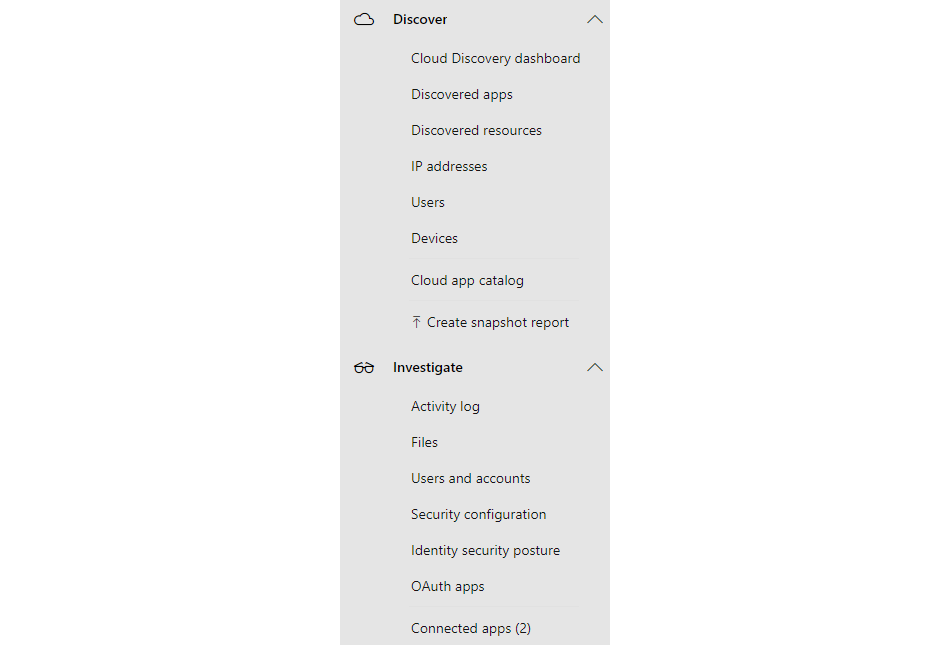
Discover and investigate
Over the whole platform of Defender for Cloud Apps, discovery and investigation tasks are summoned here:
How to get started
- Understand the product
- Get corresponding licenses
- Perform a cloud discovery
- Analyze data and behavior
- Create a concept of
- Baseline/templated Policies
- Individual enforcements (own Polcies)
- Operational guide
- Activate Policies
- Respond to actions (identity & access management SecOps)
Deployment considerations at a glance
- The Internet offers a huge and broad attack surface, interaction from users can not be governed -> Shadow IT
- New apps are added on the go, without manual IT action
- Operational costs are relatively low
- Cloud access security broker (CASB) with a major App catalog rated in security and compliance terms
- Inform & communicate about the influence and power of this tool
- Take a look at the discovered apps and their scores
- Operations are very intuitive through real-time Alerts
- Information for identity events is available to investigate and correlate
- Implement a process to sanction low-scored apps
- Defender Suite integration is seamless and data from Defender for Cloud Apps are a must have
If you want to learn more about it, please read: A tour through Defender for Cloud Apps
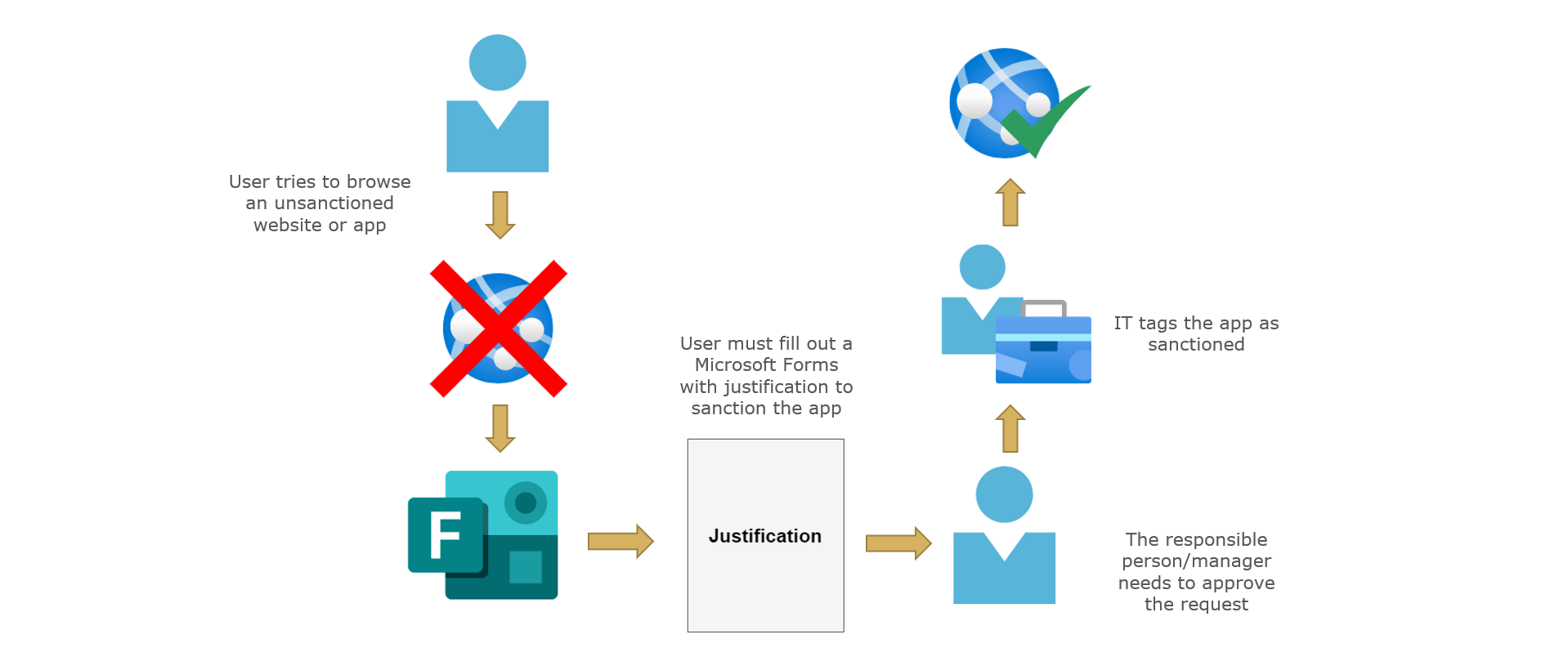
Tip: Process to (re)sanction apps
If the policies are strictly enforced plus access blocked through Defender for Endpoint you should have a concept ready, which describes the process of (re)sanctioning applications.
I would consider providing a Microsoft forms that requests the background of using an app or website with a justification. Then a security manager should evaluate the request and approve or decline it.