Transition to modern Endpoint Management
This is an updated post, here you will find information about:
- Endpoint Management design (legacy vs. modern)
- Reasons for Hybrid or Cloud-only
- Configuration challenges and approaches
- Security aspects
This post is intended to give an engineering overview on the journey to Modern Endpoint Management with Microsoft Intune. I want to share my technical experience when we talk about these topics.
Depending on your experience or role, it might be useful to check out one of my other posts about endpoint management:
- Completely new to Intune? A touch on Intune
- Want to dig deeper and see whats possible? What you need to know about Intune
Hybrid or Cloud-only?
These are common questions that come up in a discussion about hybrid or cloud-only. The italic sentences are a common modern/cloud-only attempt.
- Deployment/Imaging
- Does the image need to be customized or can we use the pre-installed of the IHV? Mostly, the pre-installed OS can be used during the Autopilot process, as critical updates wil be installed directly..
- How are the clients deployed? For corporate owned devices, register the device hashes in your tenant and deploy the devices through Intune/Autopilot.
- Management and network dependency
- Where and how can the clients be managed?
- How much effort can you put into operations? (especially updating)
- How dependent are you on the network for line-of-sight to domain hosting workloads? Workloads move to the cloud, although line of business (LOB) apps may still exist and need to be available externally. Consider Azure AD Application Proxy
- Is the network your main security perimeter? In the modern world, identity is the main security perimeter.
- Greenfield approach, how fast can you go?
- What is your OS and apps updating strategy?
- Where are the bottlenecks of a fast deployment of updates in your environment?
- Do the end-users and the IT cope with the "new" schedule?
- Security
- What are your security approaches, which standards do you want to stay compliant to? Use the Microsoft Security baselines (described below). Consider advanced Defender Security products.
- How much security systems are implemented and how do they actually communicate to benefit the security posture? In my opinion: go for Microsoft security products only, the correlation and foundation on productivity products is on a very high level.
Workloads and reasons for hybrid
- Active Directory computer object
- Group Policy Objects (GPOs)
- Application management
- "Legacy" Device management like SCCM/Configuration Manager
- Network dependency
Cloud-only
- The modern way
- Mobile Device Management (MDM) with Intune
- Autopilot deployment
- Bring your own device (BYOD) and Mobile Application Management (MAM)
- The backbone to all other Microsoft cloud services
Configuration management in Intune
Overview of profiles
| Topic | Profiles | Use |
|---|---|---|
| Enrollment | Deployment profile | Define the join type (Hybrid or Azure AD only) and enrollment settings |
| Enrollment status pages | OOBE - configure the device setup configuration progress | |
| Configuration | Configuration profiles | Described below |
| Scripts | PowerShell scripts to run on endpoints | |
| Proactive remediation scripts | PowerShell script package that detects something on and endpoint and, if necessary, runs a remediation script | |
| Security | Endpoint Security + Baselines | Described below |
| Compliance | Compliance policies | Define a set of rules and settings that endpoints must meet |
| Updates | Update rings | Define Windows Update for Business rings |
| Targeted feature/quality updates | Target a specific update |
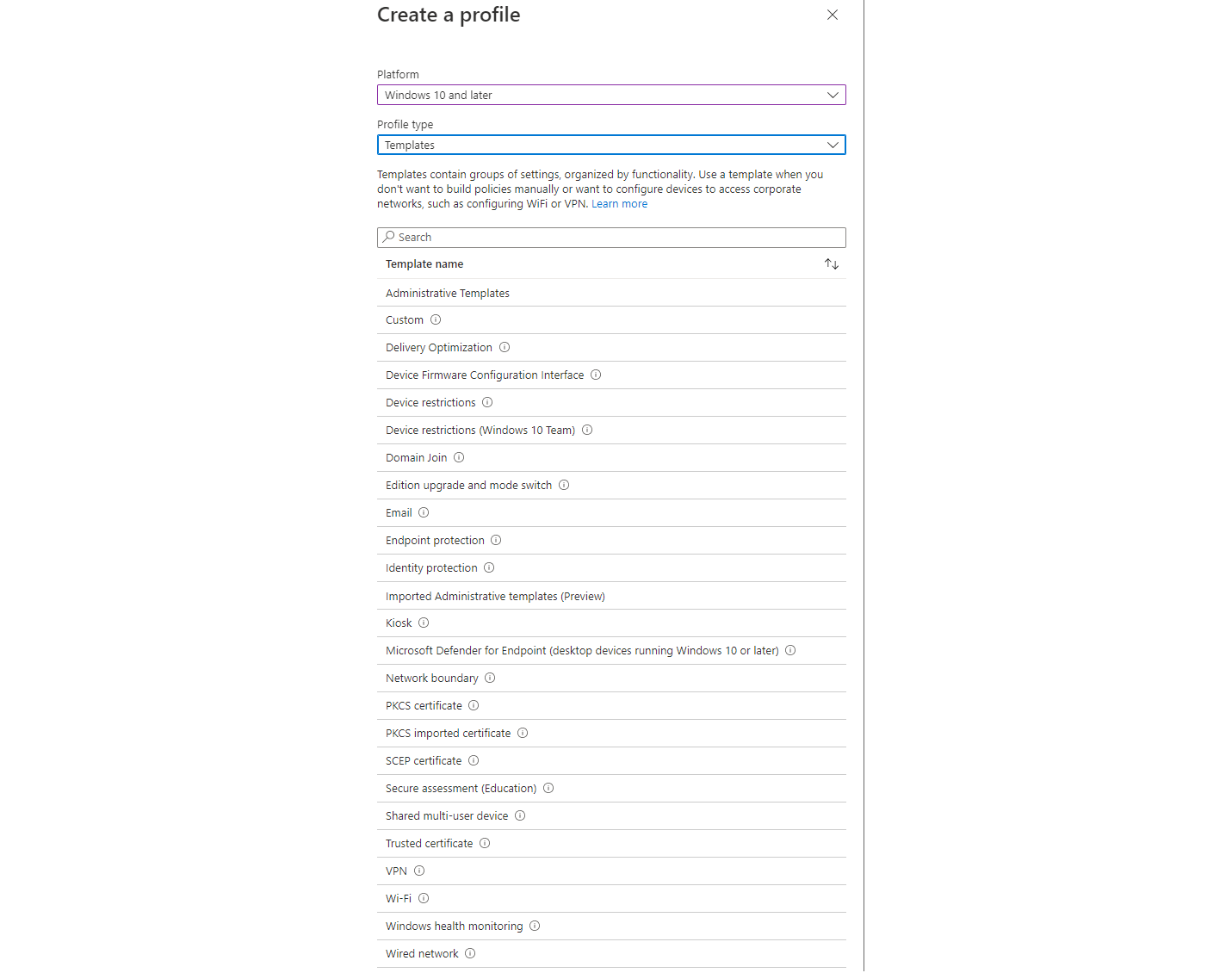
Configuration profiles
This is an excerpt of the templates offered by configuration profiles. Though, the modern attempt is to prefer settings catalog.
How to configure settings
This is your Prio 1: Build your base set of profiles that represent an absolute standard client (deployment + security baselines + default compliance + few configuration profiles + a fast updating ring) I would give you this tips:
- Settings catalog is the recommended way for configuration profiles
- Keep it simple! You don't need to configure anything - there is no benefit.
- Security Baselines from Microsoft (more about it in the Security chapter)
- Update rings usually come in the following rings:
- First / Insider - for the IT department or DEV only
- Fast / Pilot - use a subset of business owners to test new features
- Broad / Company - deployment to the whole company
Configuration types
When we talk about configuration capabilities in Intune, under the hood it is mostly:
- CSP - Configuration Service Providers are an interface to read, set, modify, or delete configuration settings on the device. All the configurations settings will dock to these CSPs.
- OMA-URI - path to a CSP. This is especially useful, when a setting is not depicted in the settings catalog in Intune.
In the end, the most configurations are registry settings that could also be manipulated through PowerShell scripts, particularly proactive remediation.
Common technical challenges
- Apps
- Cloud only
- Deploy simple application packages with: Win32 content prep tool
- A little more advanced: PSADT
- Connector with the Microsoft Store
- On-premises
- Application workload in Configuration manager: If you have a high volume of applications living in SCCM, consider to stick with the installation of ConfigMgr Agent on the devices until you have shifted all apps to Intune
- Cloud only
- Drive mapping > Intune Drive Mapping Generator by Nicola Suter
- Driver management > consider OEM tools (e.g. Lenovo System Update) or include drivers through Windows Update
- Printer management > consider Universal Print
- VPN > this leads to the discussion for which workloads VPN is still required. Usually any line of business apps that reside in the corporate network. But generally a modern attempt is move to Cloud SaaS apps or leverage Azure virtual desktop or Windows 365.
- Certificates
- On-premises deployment: PKI (requires healthy certificate authority) (more described below)
- Cloud-only: SCEPman as cloud CA
- Remote Support > view an overview of Comparing remote support solutions
- Logs > view my blog post on Log analytics: the basics
- Third party app management/updating > consider Patch my PC or Chocolatey
- Corporate owned single use (COSU) devices > view my blog post on Intune - a reference to Kiosk/shared PC mode
- Tracking Windows Updates: Implement WUfB reports. Espcially the Update Compliance Dashboard from MSEndpointMgr
- Product activation (Windows/Office)
- Subscription (Windows E3 license) based activation in cloud-only environments
- Active Directory based activation/KMS in a on-premises domain
Security aspects
Design topics
Authentication with Windows Hello for Business
Leverage WHfB to get rid of passwords on devices and rise security. View my blog post:

Certificate deployment with SCEP/NDES
Identity verification through certificates can be achieved with NDES and SCEP or PKCS:

LAPS
The Local Administrator Password Solution is a familiar Microsoft product which is responsible for managing and backing up the password of the local administrator account to (Azure) Active Directory.

Endpoint Security
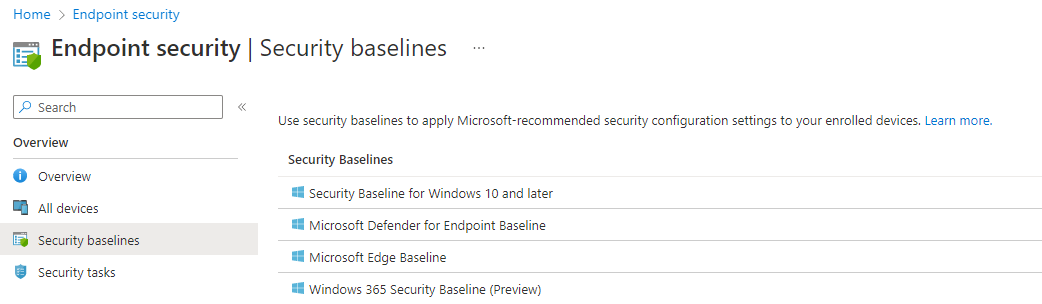
Security Baselines: endpoint hardening
In Intune there are predefined Security baselines for: Windows 10 and later, Defender for Endpoint, Edge and Windows 365. These are based from the Microsoft Security Compliance toolkit where you can find more information. Best practices:
- Implement Security baselines on all devices, which includes:
- Antivirus - Defender AV
- Disk encryption - Bitlocker
- Firewall - securing network connections
- Endpoint detection and response (EDR) - advanced security features
- Attack surface reduction - system hardening
- Account protection - account settings
- Device compliance - check device state if they meet security requirements
- Use the supplied excel spreadsheet, which lists all security settings for the corresponding OS version
- Every adaption to a baseline must be approved by the security responsible (CISO) and must be documented and justified
Microsoft Defender Antivirus + Defender for Endpoint (EDR/XDR)
Defender Antivirus is your included base protection on any Windows system. Although the monitoring and reporting capabilities are limited in Endpoint Manager.
Endpoint and Extended detection and response is covered by Defender for Endpoint. For advanced enterprise security, this is a must. This requires E5 Security step-up licenses.
Microsoft Defender full protection stack
If you are considering Defender for Endpoint, it is imperative that you consider the entire Defender security stack to take the full holistic approach of Microsoft. This includes protecting: endpoints, apps, data and identities and correlation between this spheres. Learn about Microsoft 365 Cloud Security correlation.


