Launching an attack simulation training
The idea
Most enterprises use email systems to communicate with internal colleagues, other companies or customers. The exchange of information represents a potential security concern, as adversaries could use it to attack end users. Technical measures do not always provide sufficient protection, so competence and awareness in security is required as the last point of defense. To train this ability, Microsoft offers the attack simulation training to simulate an attack attempt, discover the impact and behavior and schedule trainings.
The first protection perimeter
As already described in my Defender for Office blog post office, including messaging and Exchange offers a huge attack surface, allowing attackers to attempt for end users. Common attack techniques include:
- Phishing - legitimate-looking messages to extract information or lead to a forged website where credentials are asked or further user actions are forced - MITRE ATT&CK T1566
- Malware attachments - that run code to fetch system information, approach arbitrary code or damage system and application files
This is usually the first interaction between the attacker and the victim. After the opponent has initial access to the system, he can then proceed with further malicious actions and lateral movement.
Although all messages are usually scanned by a security intelligence, it may happen that a false-positive message was delivered to the user's mailbox. This may be to technical failures, zero-day attack pattern or a sophisticated message that does not appear as dangerous.
The product: Defender for Office 365 with attack simulation training
Defender for Office 365 has multiple security layers and includes an internal attack simulation training.
The attack simulation training allows to run campaigns of common attack techniques. The intention is to collect real world behavior analysis on how your employee's/your organization handles these types of mails. Subsequently awareness trainings can be initialized.
This feature requires Defender for Office 365 Plan 2 license.
So when we talk about Defender for Office 365 security concepts, I would mention the following goals on each side:
The attackers goals
- Steal a victims identity and gain access
- Compromise a system with harmful contents and code
- Get initial access for lateral movement (to privileged accounts etc.)
- Lead a victim to a malicious website or resource
- Spread misleading or harmful reputational information
The IT goals
- Protect the mail system (for example with Defender for Office 365)
- Detect, investigate and respond to suspicious events
- Maintain the security posture and be prepared for future threat landscape development
- Rise the awareness and help end users understand their importance for enterprise security
Always try to protect all links in the chain, including the end user.
How to launch an attack simulation
Lets navigate to the Microsoft 365 Defender center, to attack simulation training.
Prerequisites: Settings & End-user notifications
There are a few preferences, such as:
- Repeat offender threshold - amount of simulations in which a user was compromised, to set a flag on that user
- Simulations excluded from reporting
- Global notifications (default simulation notification, default positive reinforcement notification, default training assignment notification, default training reminder notification) - view preview and set language
- Tenant notifications - custom notification with own contents
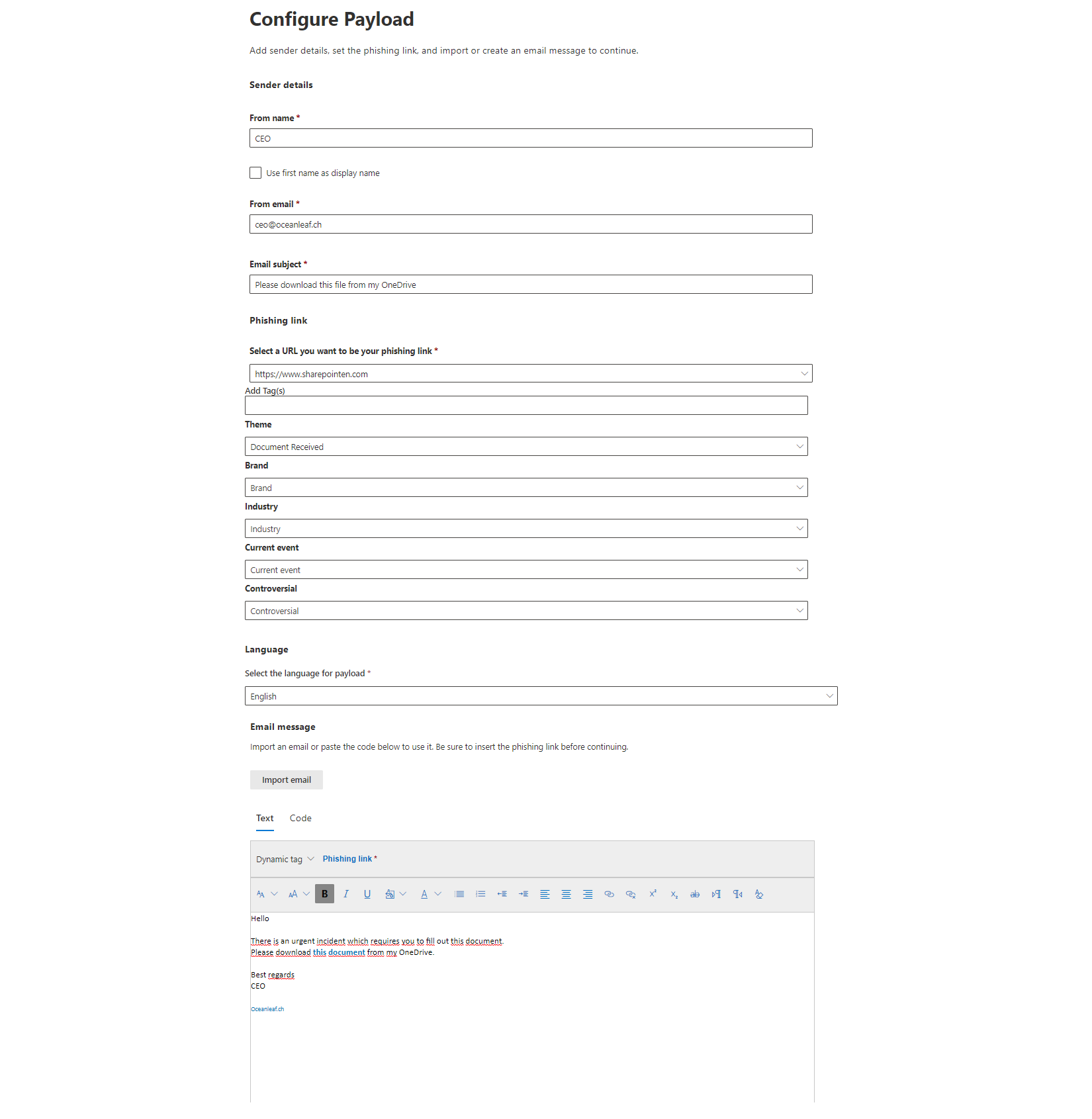
Payloads
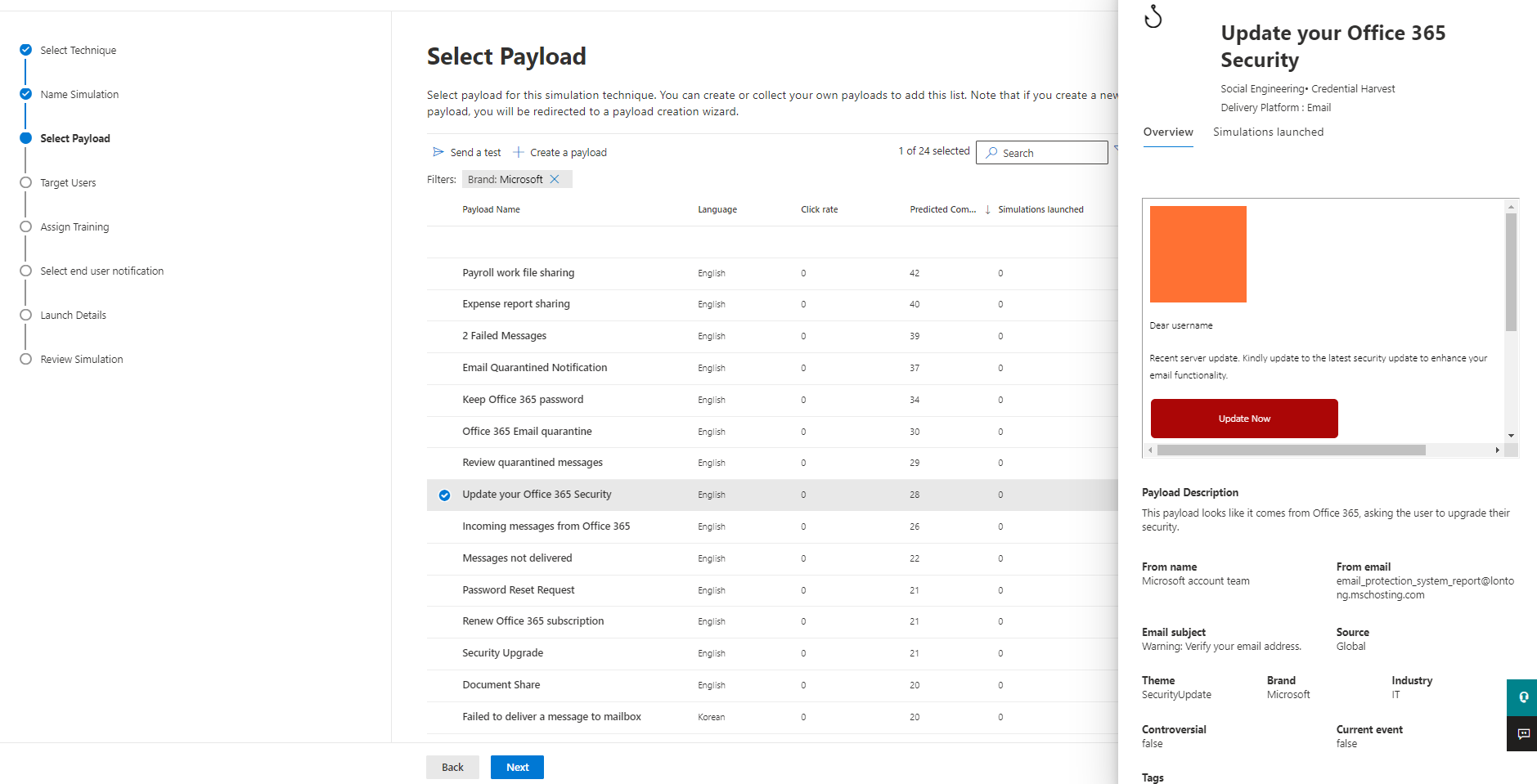
The payloads consist of over 200 Microsoft templated phishing emails and webpages in different types, languages, attack techniques, complexities, content themes, brand imitations, industries and if the should base on a current event or be controversial.
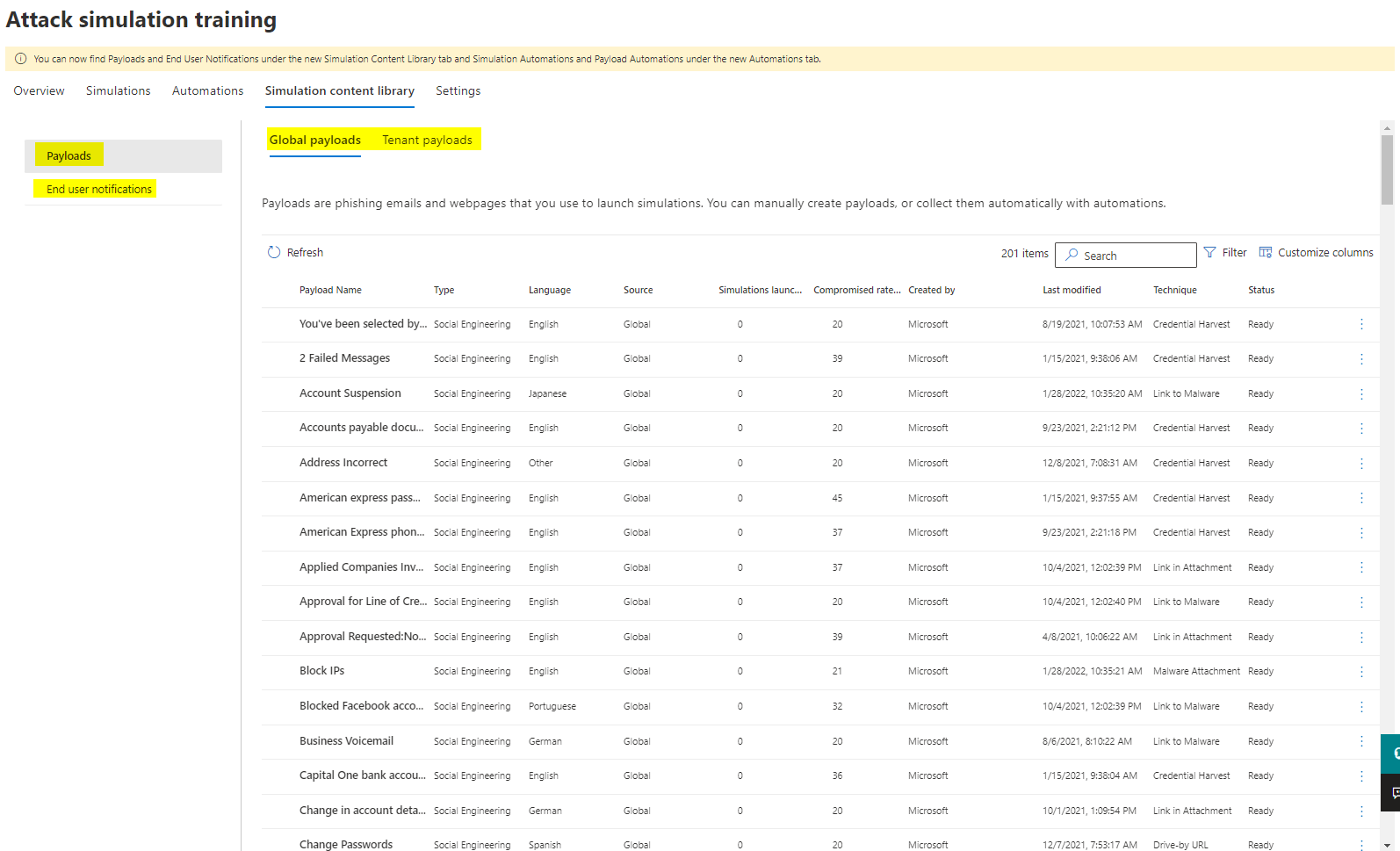
Create a custom payload
Custom, tenant payloads can be created through Email or Microsoft Teams. After the attack technique is selected, the payload can be fully customized. You can fake the senders information and write a custom message and replace the links or attachment with simulated malicious contents.
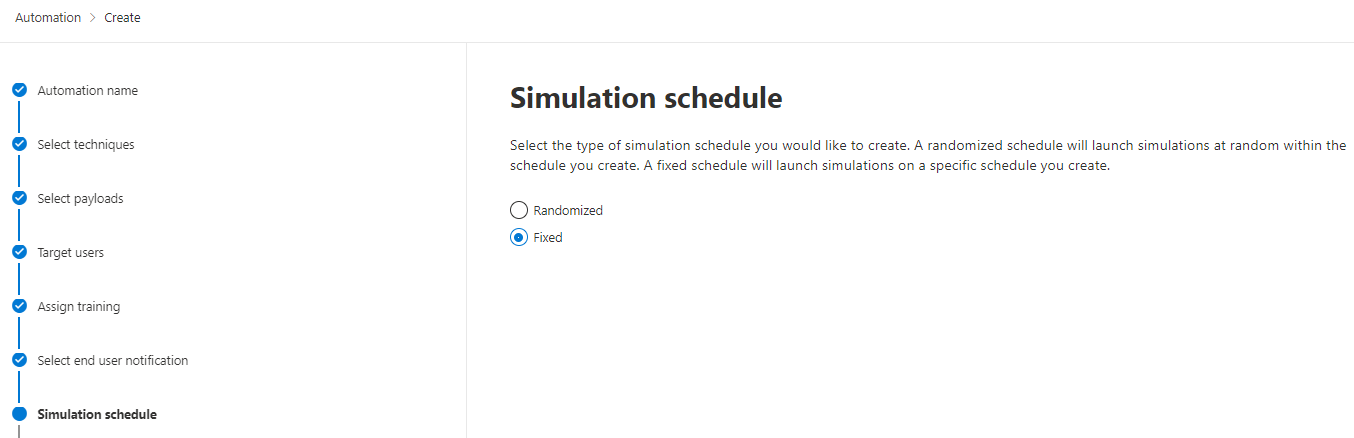
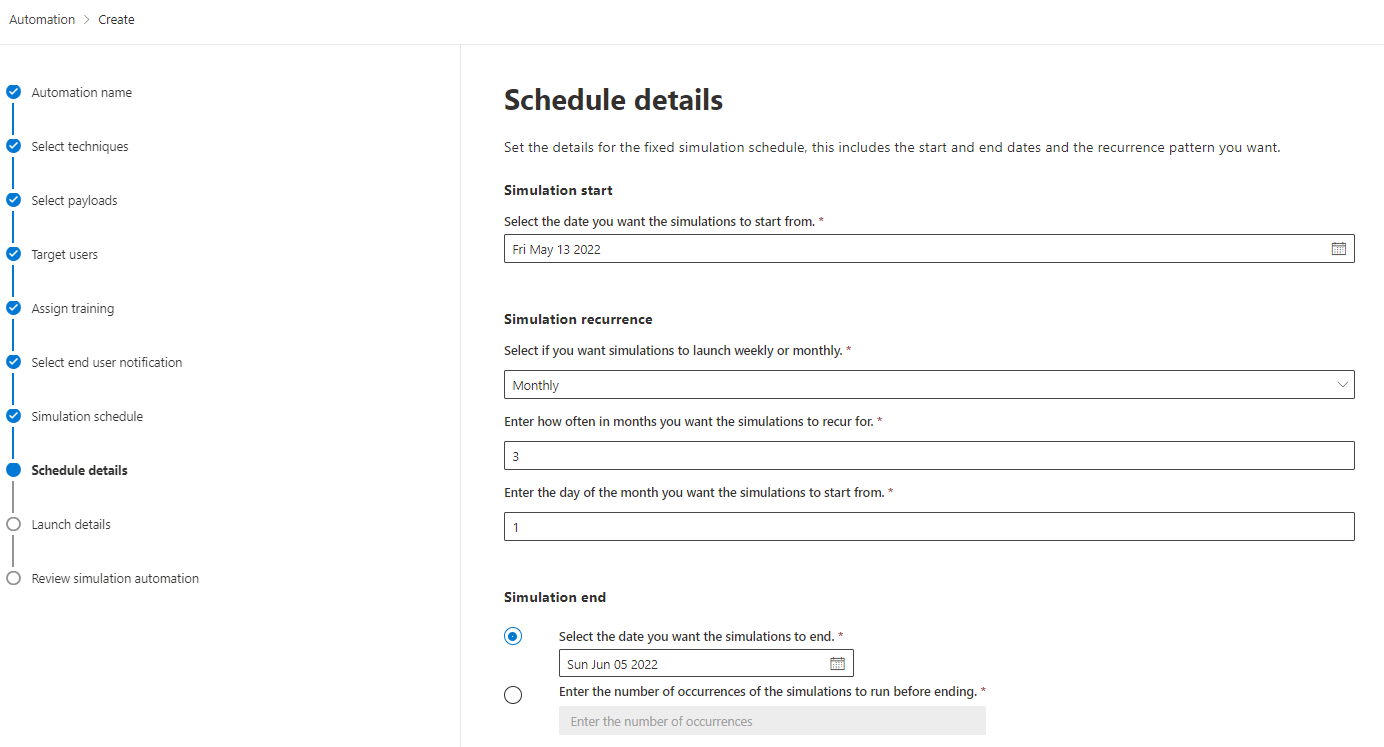
Simulation automations
If you want to have regular, scheduled and automated attack simulation trainings, simulation automations is what you are looking for. There you can:
- Select multiple techniques
- Choose a scope of payloads or randomize between all available
- Randomize the start time and set the occurrences within a timespan
This helps you with security consistency and awareness for employees who have been with your organization for a while, as well as those who are new and not as familiar with email security. Through the randomized parameters it is even an automation cycle, that doesn't really require IT maintenance or care.
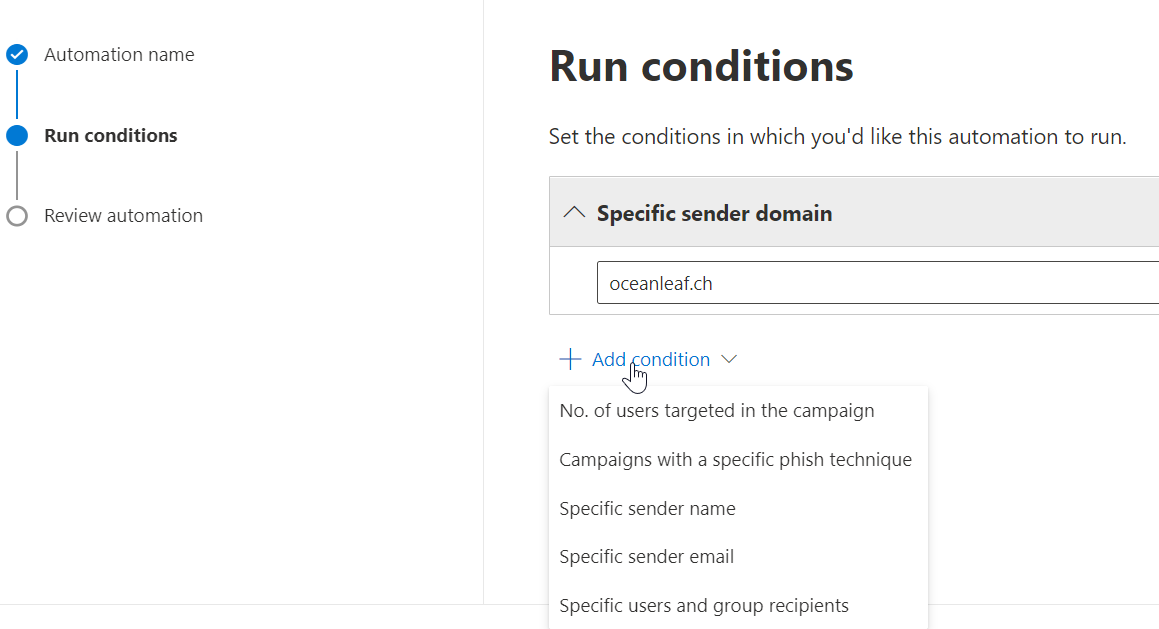
Payload automations
Payload automations are a contemporary attempt to collect true-positive real-world phishing messages, targeted to your organization. In order to collect such information, you need to set certain conditions to find (suspicious) messages.
Simulations
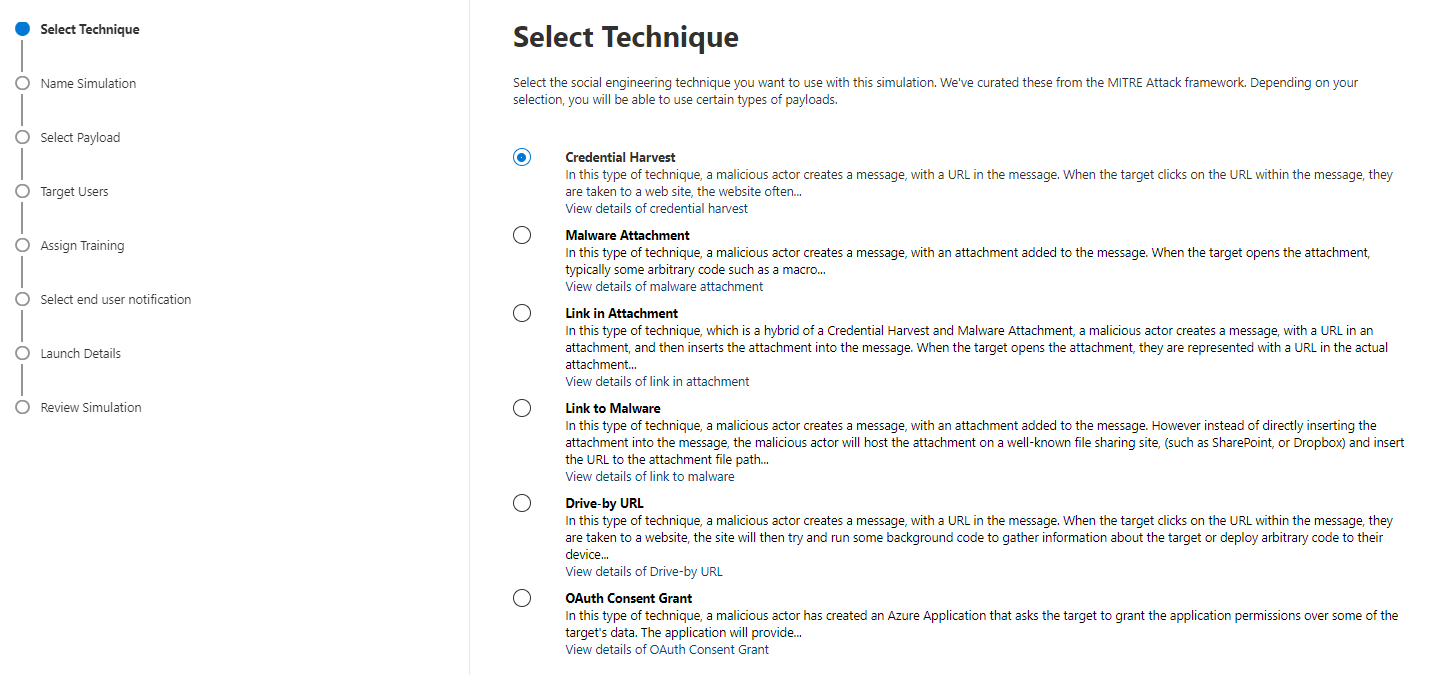
The simulation starts with the attack technique which make use of, or combined the following tactics:
- Link in message, that leads to a forged login page or malware
- Attachment with malware
- OAuth consent (more details)
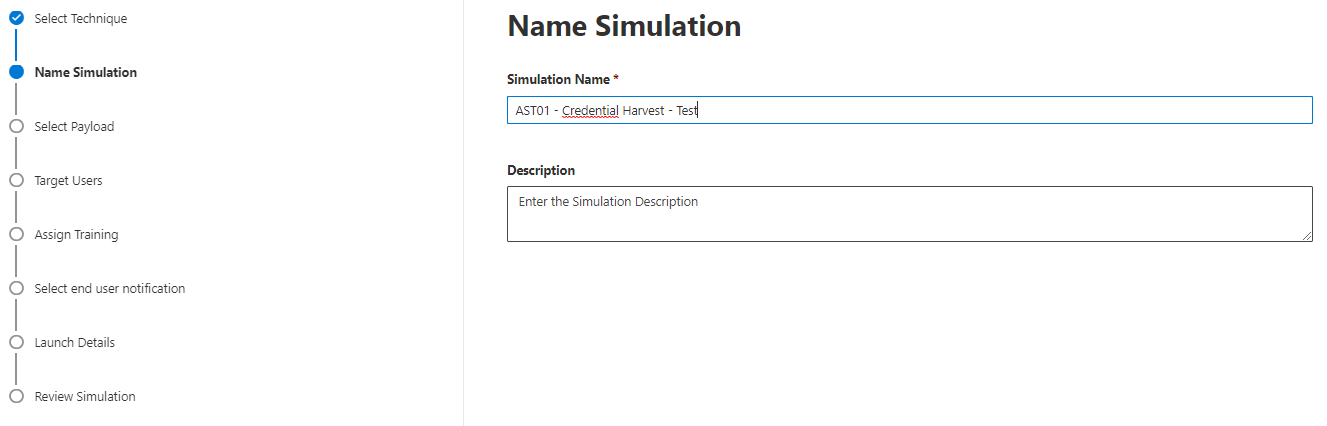
The simulation must be named:
A global or tenant payload can be selected next.
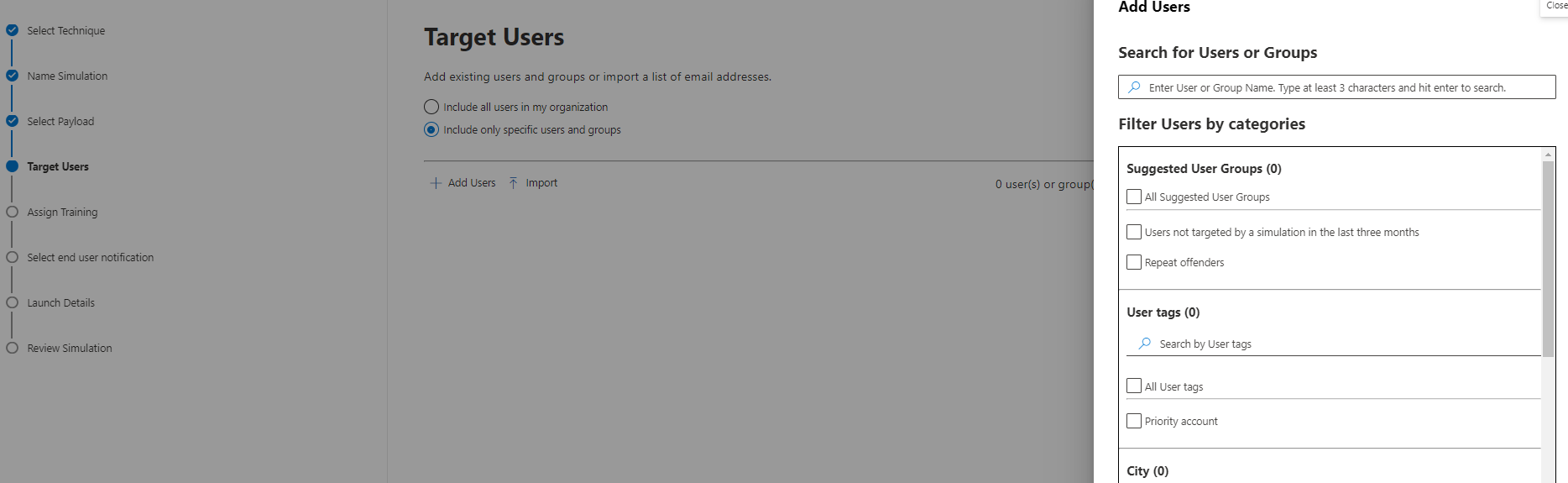
Then your target users must be specified. There are some good filters, based on user attributes such as location, title or department available.
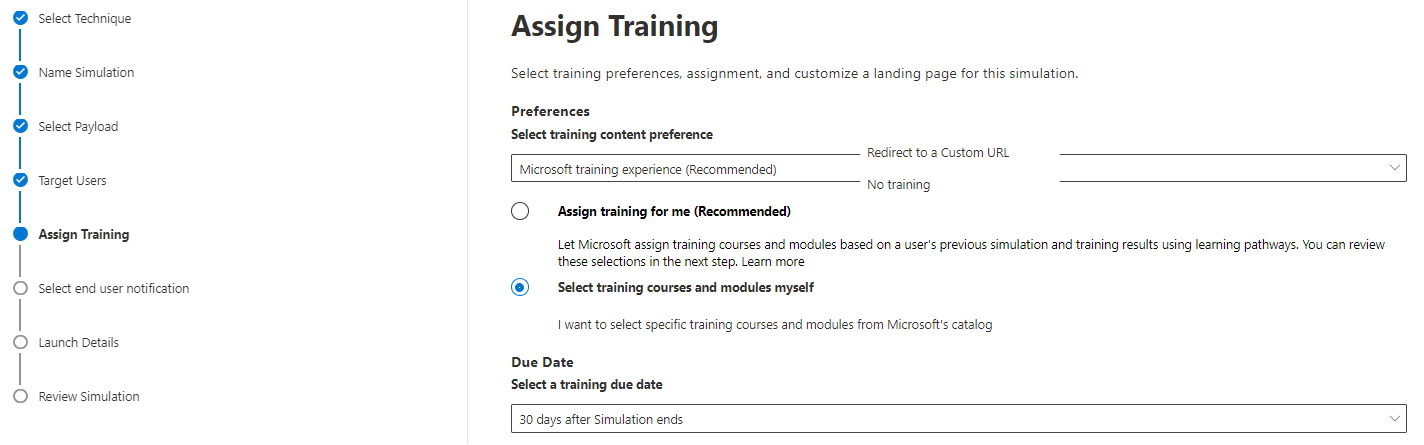
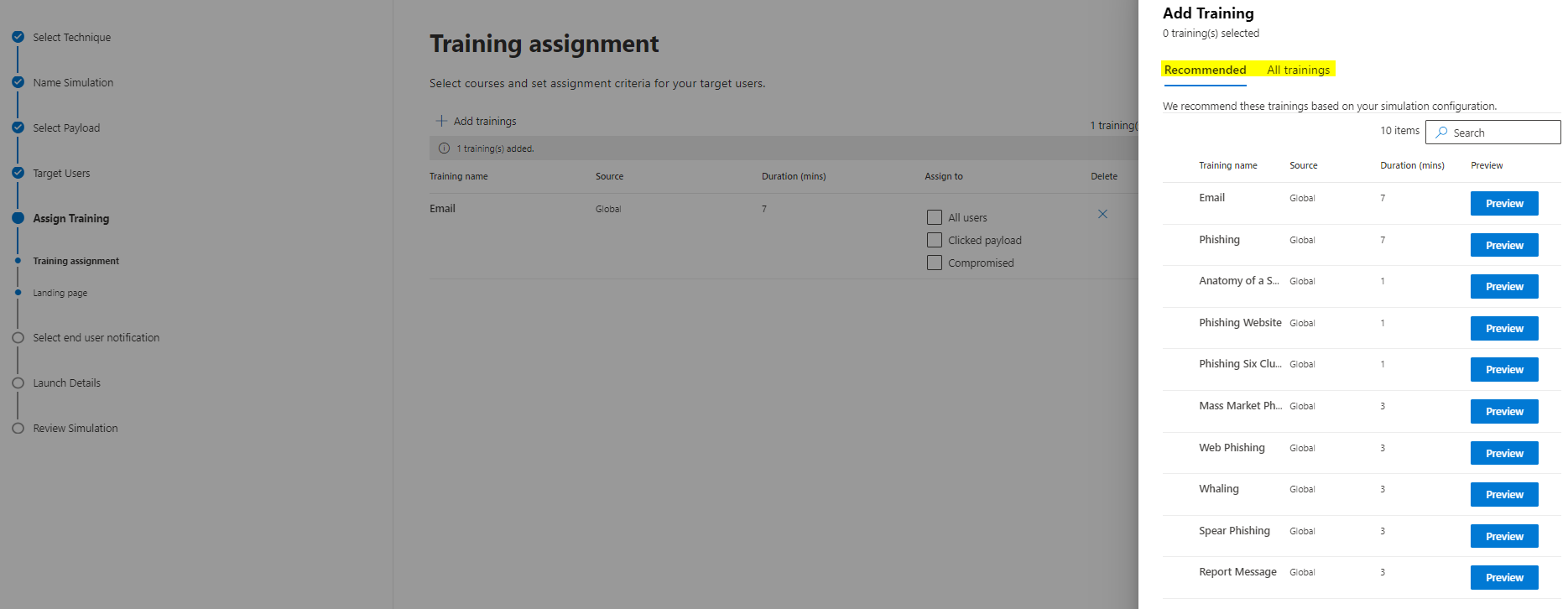
Now select a training variant: Microsoft (recommended training or custom choice), custom URL platform or no training. A due date is also to set here.
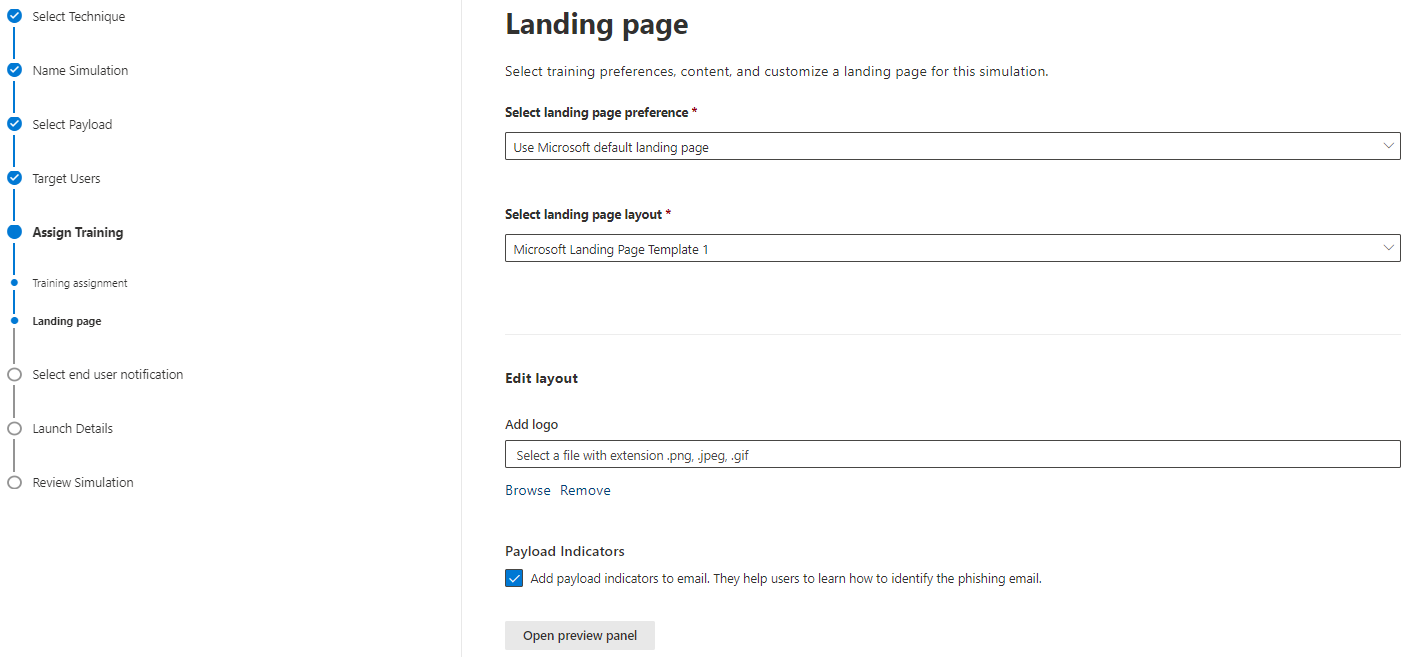
The landing page is shown, when a user was successfully phished. Either select Microsoft's template or create your custom. The indicators of the message can also be shown on this page. I would definitely activate this option.
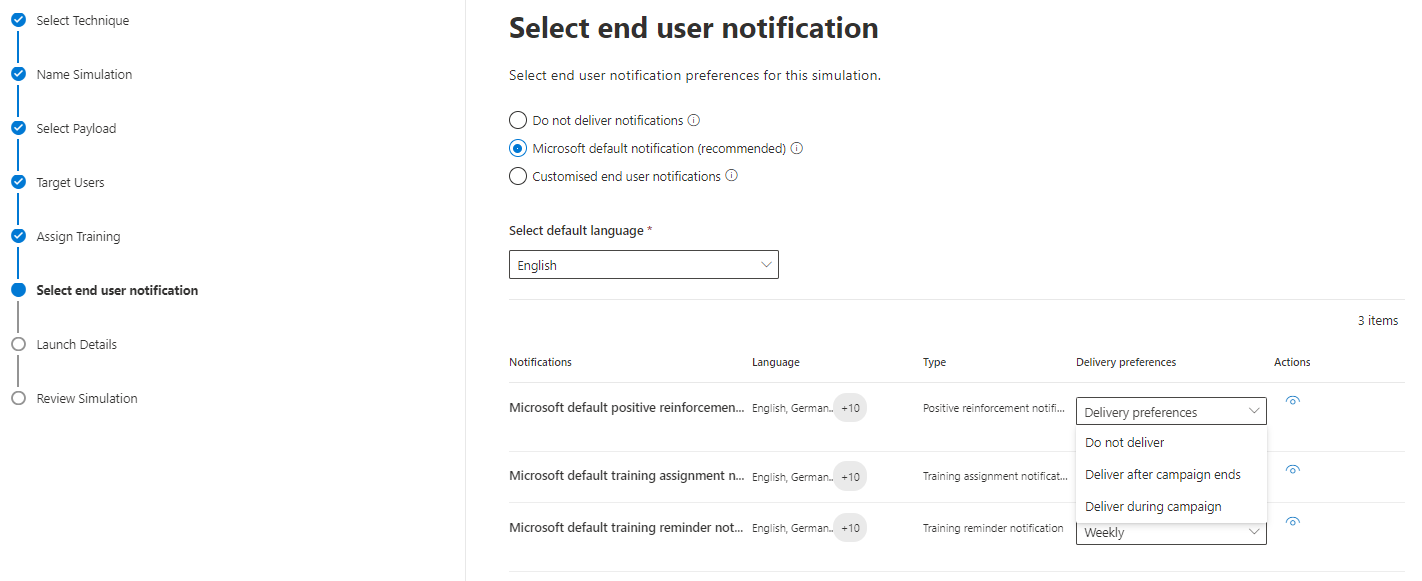
The end user notification includes:
- Microsoft default positive reinforcement notification (if a user reported the attack simulation message as phish)
- Microsoft default training assignment notification (initial training assignment)
- Microsoft default training reminder notification (reminder to the training)
- Customized end user notifications
- Do not deliver notifications
Before you launch the simulation, you can set the start to a different time/date, including awareness of different time zones.
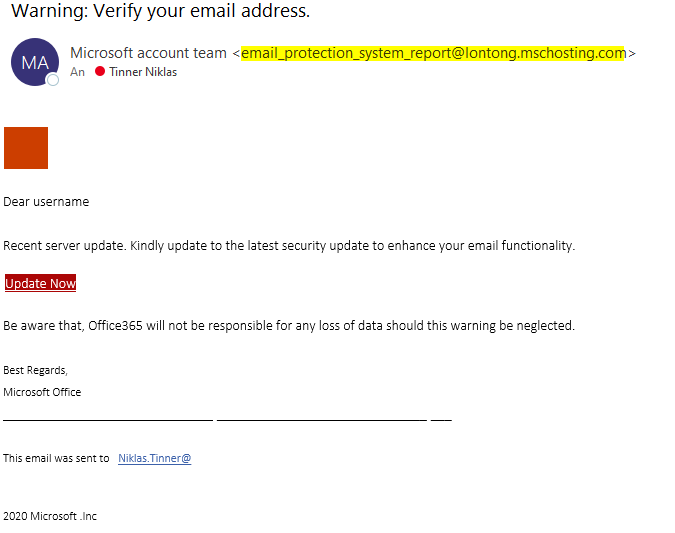
End user view - how to get phished
Let's assume you are target of a attack simulation training and receive a mail that contains malicious contents. Depending on the payload, various indicators should at least alert or warn the user. This one wants the user to click on the embedded link.
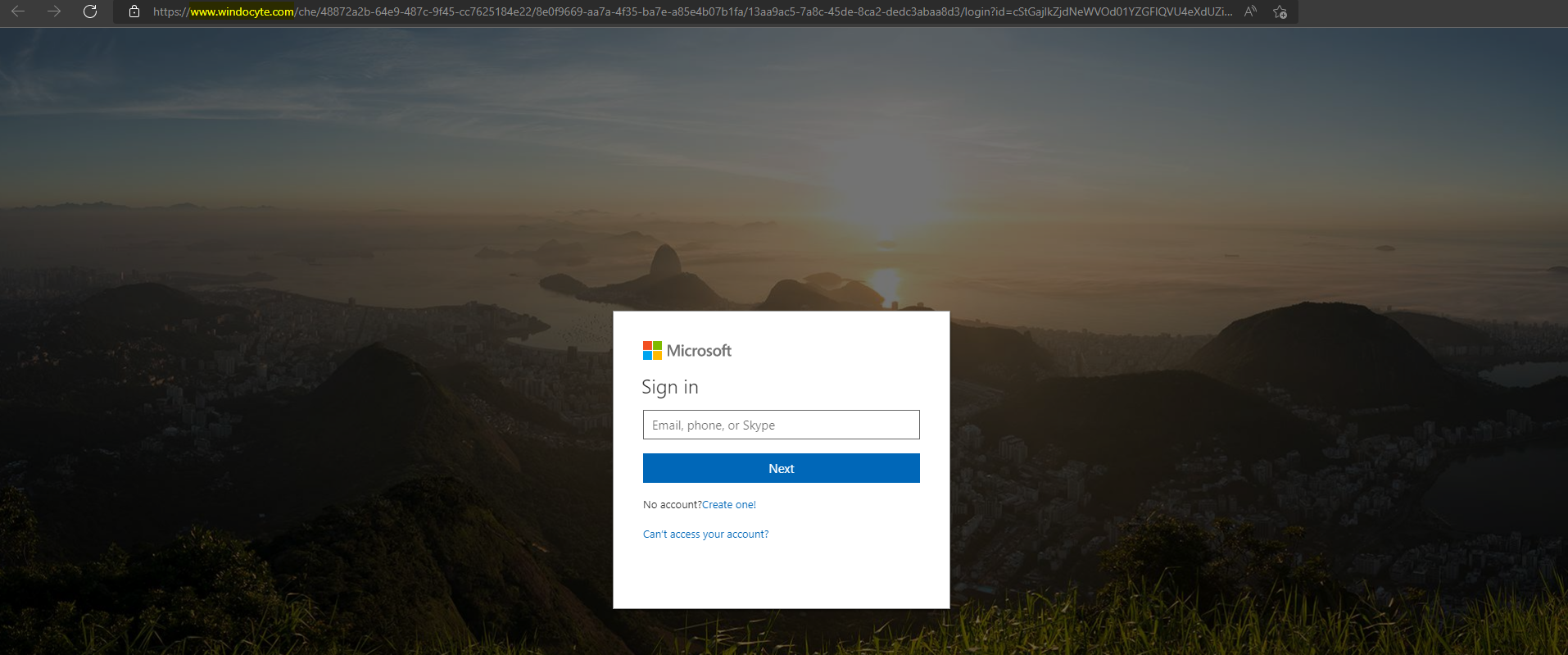
The link opens a forged Microsoft sign-in page. Here it should be pretty clear, that this is not an official domain managed by Microsoft.
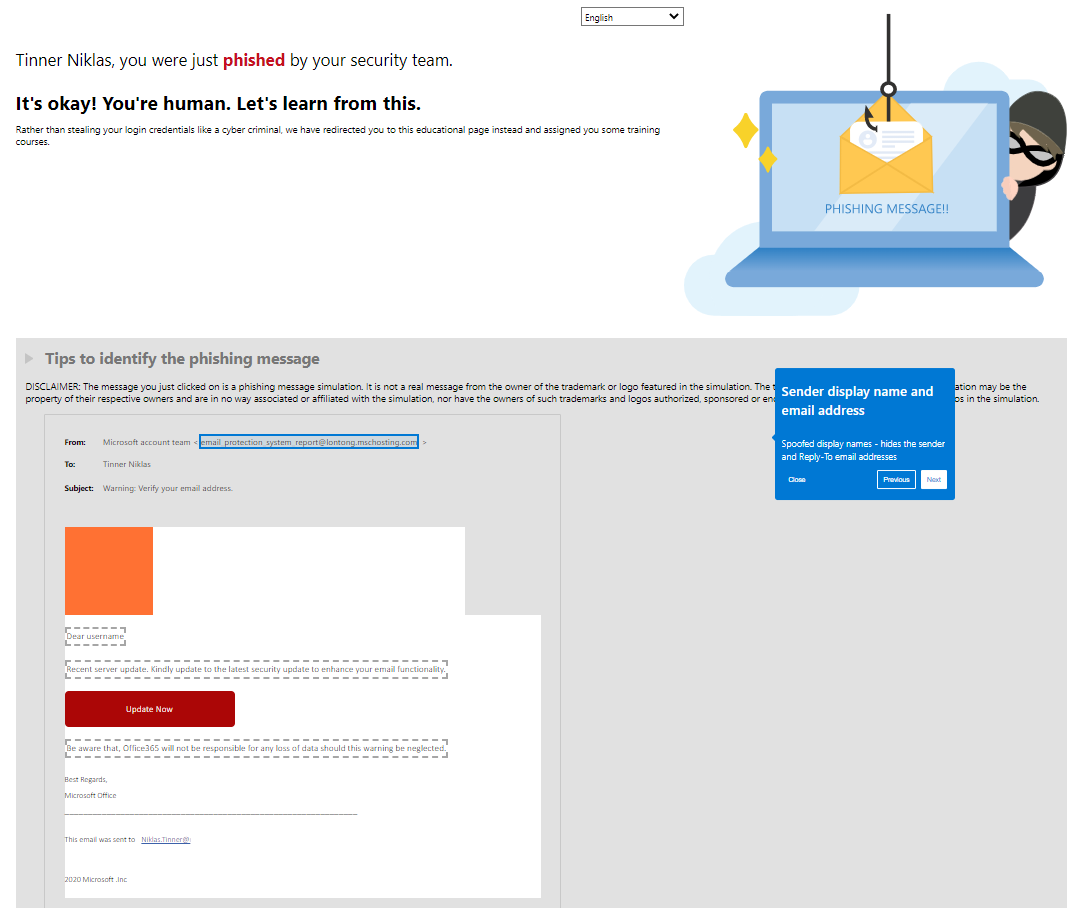
After you would enter any credentials (correct or incorrect), you get forwarded to a landing page where it states that you got phished by your security team. Within here, the user is also enlightened with the indicators of his message incident. The training can be accessed right here, or through a mail that reminds you friendly with a link.
Trainings for end users
Depending on the simulation, different end user trainings can be terminated. Usually it is a short video (English audio and custom subtitles) that will simply explain some concepts of mail security with multiple choice questions.
I think these trainings are great because they are natively integrated, are well designed to enlighten end users, don't need to much time and can be tracked by the IT department on their fulfillment status.
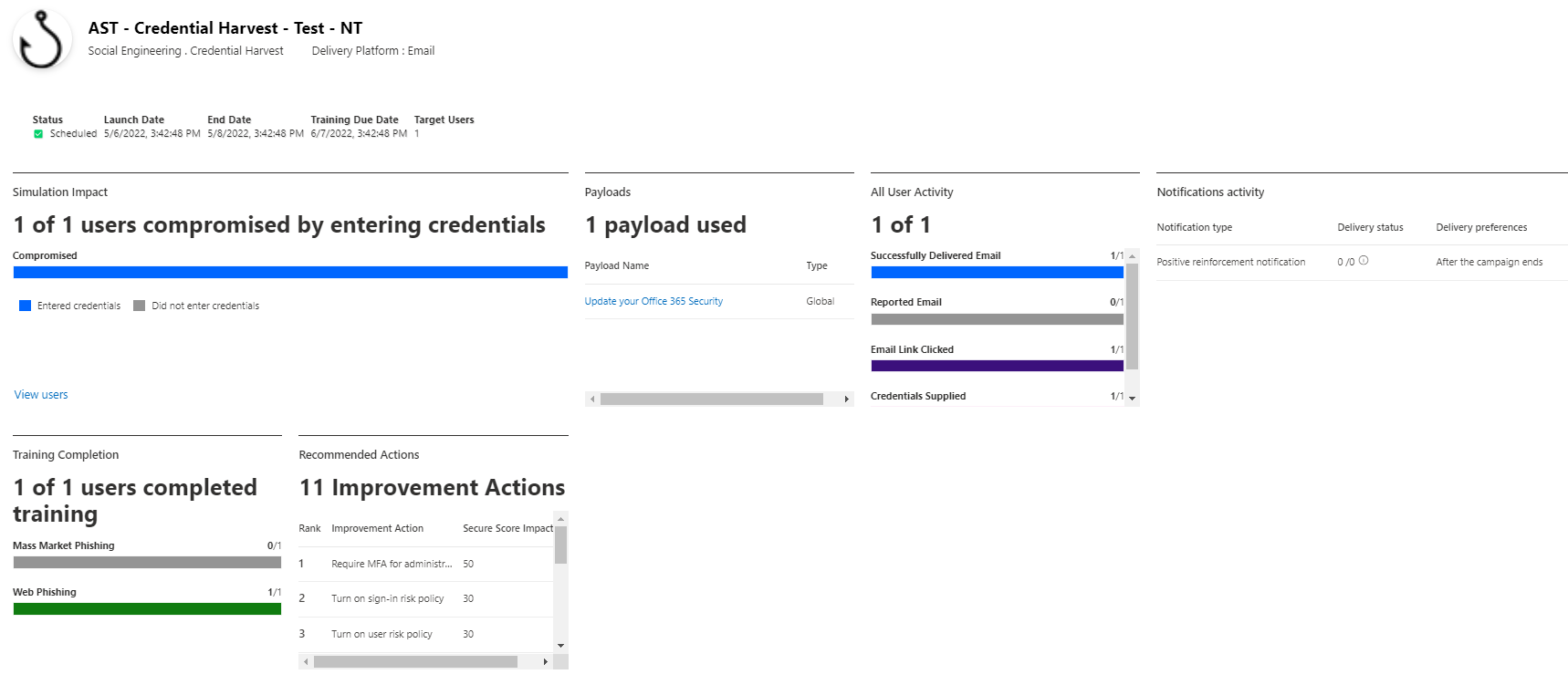
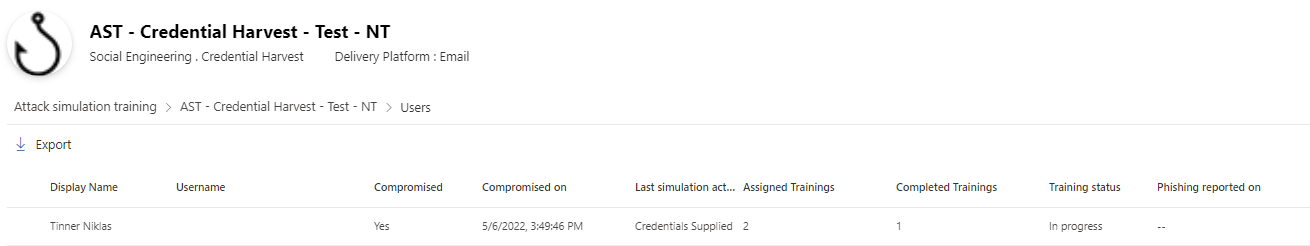
Summary report
The simulation will generate an output report to the attack simulation training overview. Simulation impact and insight to user activities, notifications are part of the overview. Trainings can be tracked on their status and improvement actions are proposed to mitigate the potential vulnerabilities.