Intune RBAC permissions
Introduction
Intune role-based access control allows administrators to control the level of access to the Intune portal and its resources.
It works by assigning roles to users or groups of users. Each role defines a set of permissions throughout Intune or device management such as Device configuration, remote tasks, security baselines, app management and so on. Usually you can give read or write access.
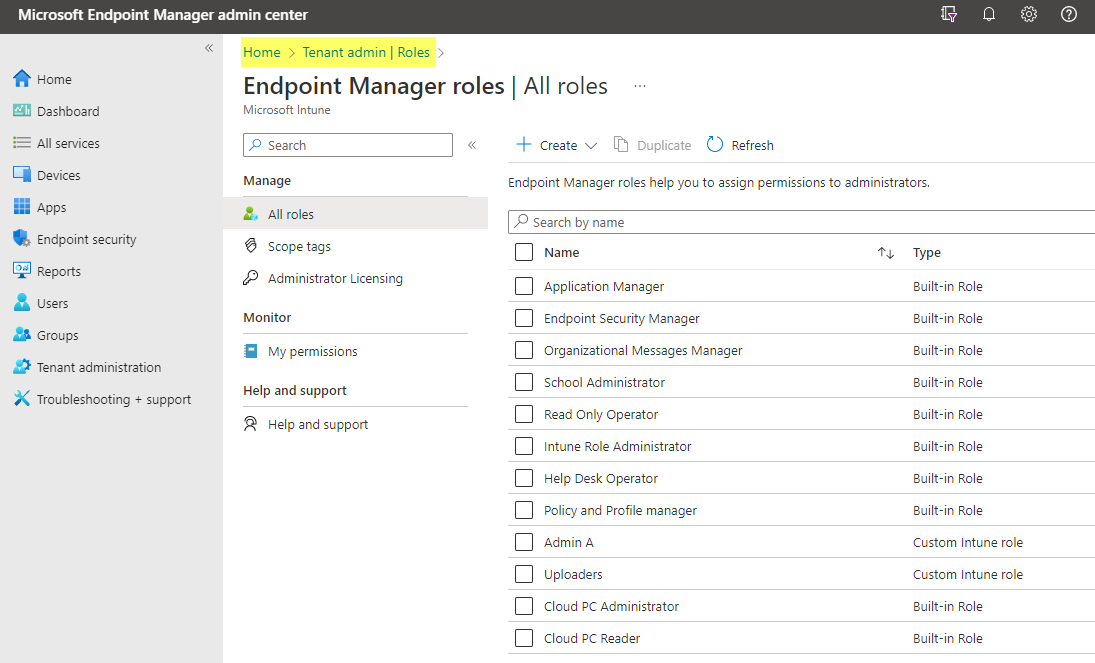
In Intune we can find multiple custom roles under Tenant administration>roles:
By default you can see the Intune built-in roles that are equal in all tenants, but you can create own roles and configure the permissions as you want.
This post only covers Intune RBAC permissions with some concepts and recommendations.
Role source
It is important to understand the difference of the role sources for permissions in Azure AD and Intune. These are not the same roles and are not available or to be assigned vice versa.
- Entra/Azure AD — all Azure AD roles that are intended for all Microsoft 365 cloud services, primarily productivity and collaboration. (Azure resources Identity and Access (IAM) excluded.) See reference
- Intune — product/Intune specific roles that are only available and useable in the Endpoint Manager admin center. See reference
Azure Active Directory roles with Intune access
Some Azure AD roles also have permissions in Intune, this table shows an overview:
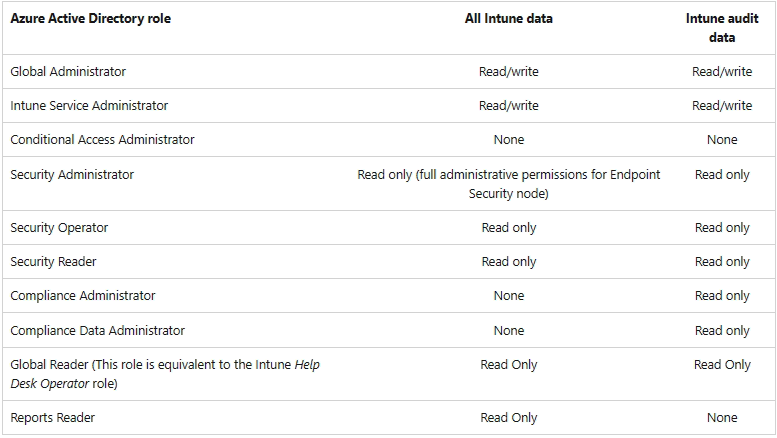
Source
Migrate roles
If you plan to migrate roles and redefine access, you may walk through these key steps and phases:
Assessment
- Assess the currently assigned users for:
- Intune administrator
- Azure AD joined device local administrator
- (Other roles mentioned above too, but these primarily)
- Check if there are any Intune RBAC roles assigned
- Check if any custom roles exist and try to find out their use
- How does the current Intune operations look like? Who does what?
Sidenote: Is it desired to enable Azure AD roles with privileged identity management (PIM)?
Concept
5. Define a concept of Intune operations (see chapter below). Here you need to clarify the following questions:
- What jobs need to be done in Intune and what are the job roles? (e.g.: Intune full admin, help desk, security admin)
- Which Intune and Azure AD roles fit to the job roles?
- (If the built-in roles do not satisfy your needs, create a custom role)
- It is important that you have a clear process on how to claim and remove the future roles, think of the lifecycle here (access reviews on the groups)
- If an employee is newly assigned for Intune operations or changes position
- Consider leveraging PIM
Change
7. Before you want to make the change you should ensure that the roles have the needed permissions for the everyday work - so make a proof of concept and assign one of the new roles to a user and let him verify the permissions
8. Assign all new roles to the users/groups, based on the concept
9. Remove old roles from the users
Operation
10. Users will have the new roles assigned and can perform actions based on their permission set. If some permissions are missing, consider to adjust the roles.
11. (Users may be required to enable their roles with PIM)
Role overview concept
My advice is to define a concept of your Intune operations and which admins need to perform which actions. My recommendation would look something like the following:
| Role | Role source | Description | Members |
|---|---|---|---|
| Intune administrator | AAD | This role can manage all aspects for Intune | Endpoint core team/admins |
| Security administrator | AAD | This role can manage the Endpoint Security node of Intune and has read-only permissions to the rest | Security officers |
| Azure AD joined device local administrator | Intune | Any member of this role is automatically added as local administrator on all Azure AD joined devices of the tenant | None |
| Application administrator | Intune | Can manage mobile and managed applications, can read device information and can view device configuration profiles. | App packaging employees |
| Read Only Operator | Intune | This role can view all data in Intune but make no manipulations | None |
| Help Desk Operator | Intune | Can perform remote tasks on users and devices and can assign applications or policies to users or devices. | Help desk staff |
Governance in Intune
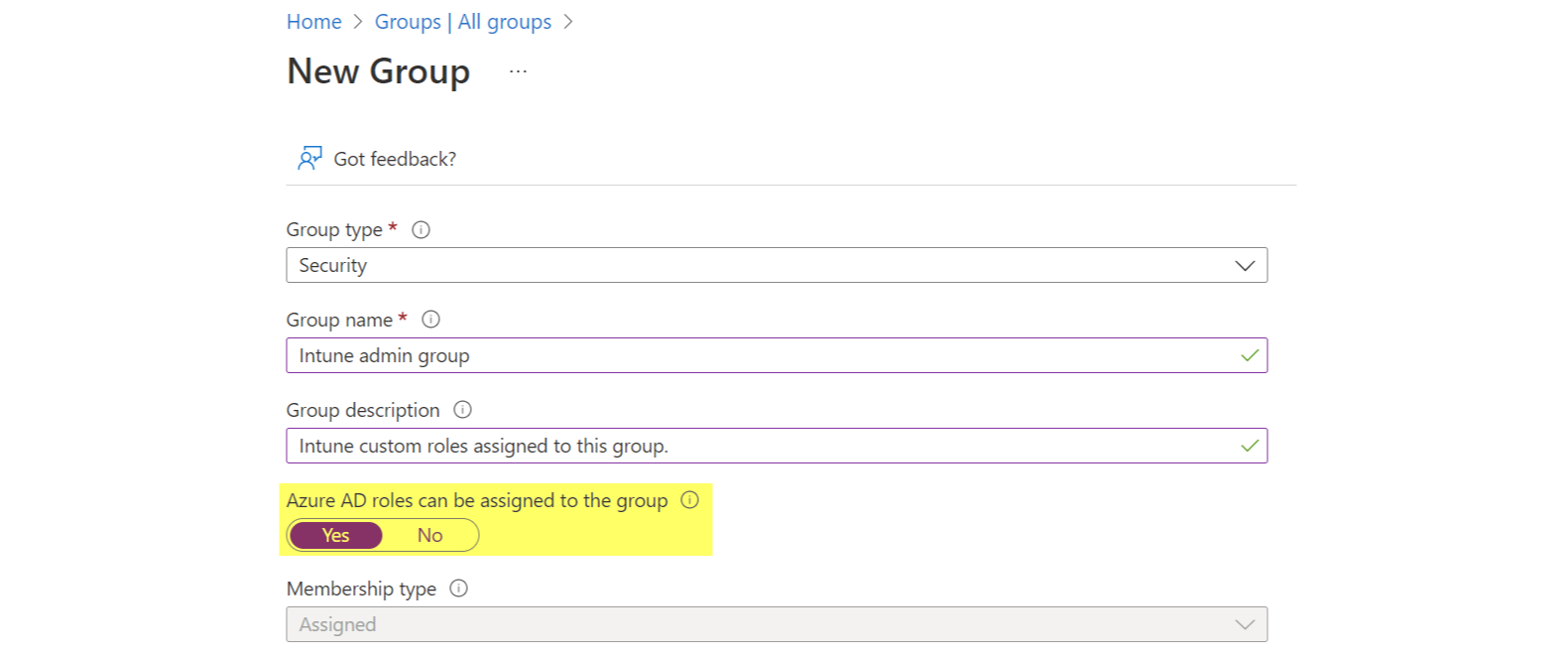
- Intune roles (custom) - general role-based access control (RBAC) to grant different users different permissions. Custom roles can be created to define individual permissions.
- Scope Tags - granularly control access to a subset of Intune objects. (In large Intune environments this helps to restrict access to e.g.: a department or location of the company) Recommended post on this topic
- Multi Admin Approval Public Preview - feature that allows a request/approval process for Intune objects. This is a dual control mechanism.
- Privileged Identity management - identity and access security feature (requires AAD P2) to provide Azure AD roles to identities with several controls.
- Privileged Access Groups Preview to manage Azure AD groups, where for example Intune custom roles can be assigned to, with similar functionalities of privileged identity management (PIM).
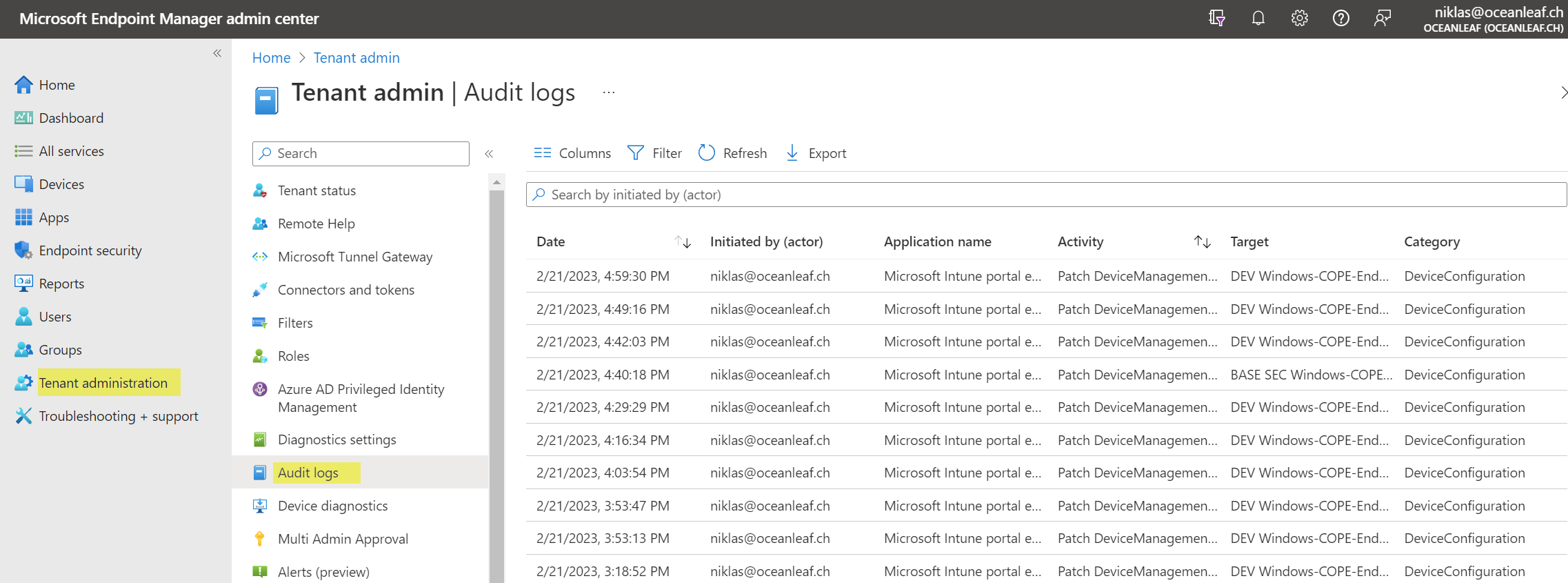
Auditing
In Intune all audit data is available under Tenant administration>Audit logs. Data is retained for 365 days by default. (Adjusting the filter is needed) With this, it is possible to determine who has performed which actions and which tasks. You may also consider to forward Intune platform data to a Log Analytics Workspace or my Intune change tracking workbook.