Intune + macOS: why and how to get started
Introduction
Uniting two worlds! 🌍 This post is a first holistic introduction into macOS management with Microsoft Intune. Learn about the key motivations and aspects of device management with a focus on security.
My ambition is to bring attention to the great Mac management experience in Intune and give you a summary of the technical considerations.
Why MacOS?
MacOS and Mac devices are a great platform to make individuals and employees productive! Regardless of the underlying operating system, it is about performance, design, app support and reliability that make one choose a Mac or another device. Historically, many IT departments (especially from a security origin) prohibited and restricted the use of Macs. Now we got a great support for this platform by Microsoft Intune and my advice is to rethink by this opportunity. It starts with a motivation for integrating Macs into corporate and IT infrastructure. Get inspired by:
- 👨💻 Microsoft promotes a day zero support strategy and investment in ongoing development for the Mac platform
- 🌐 Ensure security regardless of the OS
- 🔐 Reinforce platform security with baselines and onboard to Microsoft Defender for Endpoint
- 1️⃣ Single management portal, single management system, single support experience, same behavior - powered by the cloud = reducing total cost of ownership (TCO) and making the employees happy
- 😊 Choose your device by what you prefer
- 🚀 Support for more apps and great optimization, especially for creative work
- 📈 Be productive and more flexible, regardless of the OS
Cross-platform cloud-based endpoint management
Intune strives for cross-plattform support fully managed by the cloud. Now is the time to go for unified endpoint management provided by a single management platform. Integrate all OS, physical and virtual endpoints and treat them the same.
Learn more about Intune in this post:

Innovations
See the continuous investment of Microsoft into the macOS platform on this roadmap slides:
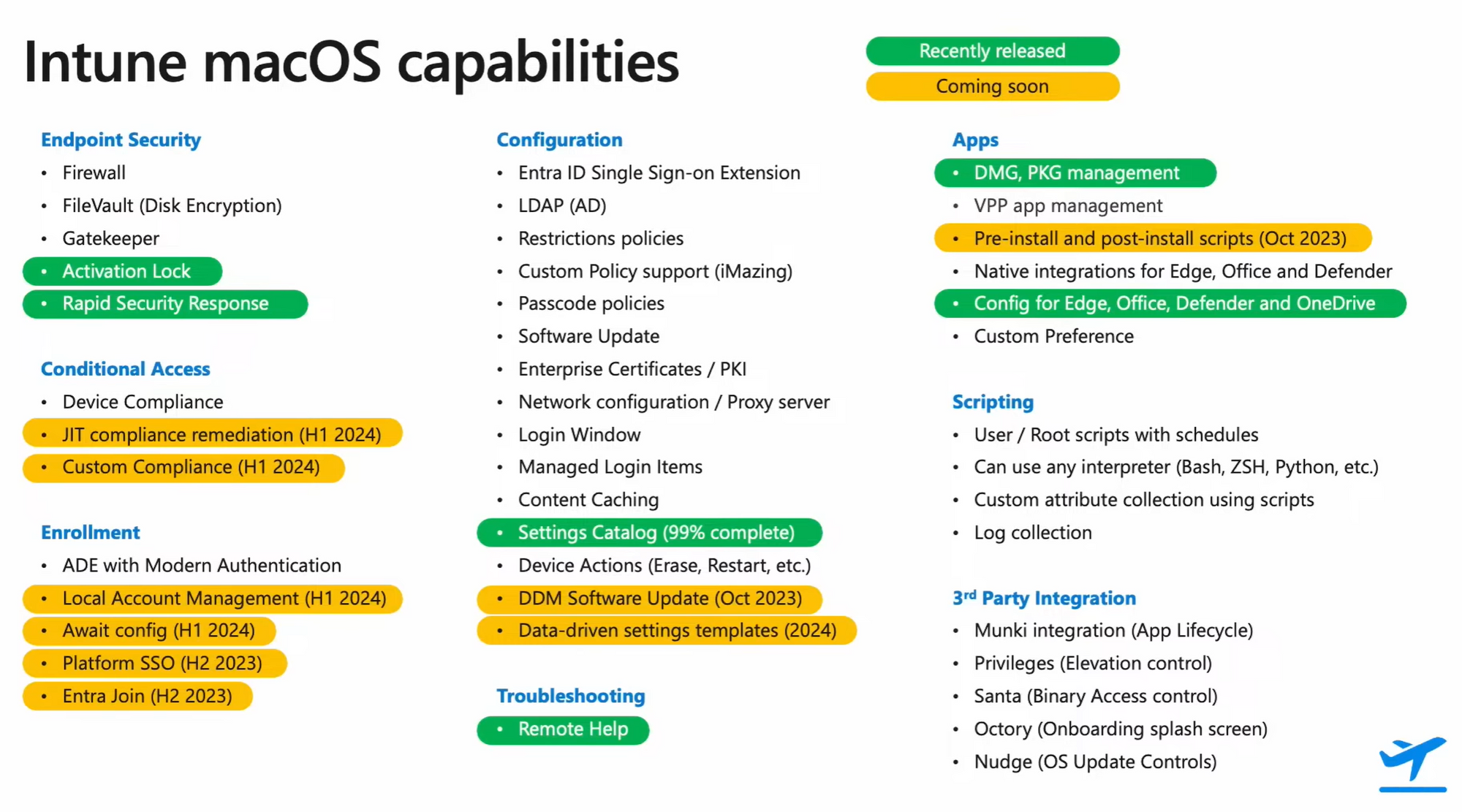
Source: Microsoft Technical Takeoff
Management
Multiple management planes get to work for Mac:
| Management system | Description |
|---|---|
| Microsoft Entra | Register your Mac for single sign on to apps on personal devices, corporate devices are registered |
| Intune | Apply profiles, policies, deploy apps and ensure security + remote actions |
| Defender for Endpoint | Onboarding to MDE for monitoring, remote actions or Defender endpoint security settings management |
Prerequisites
Before you start with your Mac + Intune journey, it is important that you make some considerations and have the technical parts ready.
Organizational/technical
- Approval by security responsible to use Macs for organizational use
- Define your Mac management strategy
- Which devices are supported? personal/corporate
- Which identities are used? no Apple ID, personal Apple ID, managed Apple ID
- Choose user accounts + single-sign on (SSO) type: Enterprise SSO plug-in/platform SSO
- Define macOS policies, compliance and security requirements
- Plan project initiative
Technical
- Intune tenant + appropriate licenses
- Intune enrollment prereqs
- MDM authority
- Enrollment restrictions
- Intune admin role
- Apple Push Notification service Certificate (APNs) integrated to Intune (⚠️ must be renewed anually)
- Optional but recommended: Apple Business or School Manager instance
- Don't forget to adjust potential Conditional Access policies that target the macOS platform
Endpoint management on Mac
Learn about all core endpoint management topics on Mac. This includes configuration aspects to manipulate the system, apply design changes and adjust the behavior. Inspired by macOS platform guide
Enrollment
Your Mac must be enrolled to Intune for organizational use and so that policies can apply, compliance can be requested and apps installed. There are two common ways to achieve this, depending on the device ownership:
-
Bring your Own Device (BYOD)
To be chosen for a personal device, onboarding through Company Portal app installation and subsequent onboarding process through user- ✅ No need to register the Mac, no Apple Busines Manager required
- 📈 User can get productive right away on his personal device with just a few steps
- ❗️ Mac is not linked to your organization, a wipe removes all management aspects and the Mac can be setup again without any restrictions
- 🕵️ Mac is managed by the organization, policies can apply, compliance fulfilled and personal data can still be saved on the Mac (there is no corp data only wipe, except retiring the device from management)
-
Corporate-owned Device
The Mac bought by the org is recommended to be added to the Apple Business Manager, so it is permanently linked to the organization. Other options include manual processes done by IT administrators.- 🍎 Apple Automated Device Enrollment (ADE) - recommended
- Mac is permanentely linked to the org
- Enrollment starts at first boot up with a customized setup experience (Macs Out-of-the-box experience)
- ↙️ Direct Enrollment
- Transfer the enrollment profile to a Mac over a USB connection from a devices that runs Apple configurator
- Use the Apple Configurator App for iOS to onboard devices to ABM manually (recommended)
- 🆔 Add corporate identifier IMEI, serial to Intune
- On enrollment process, the devices automatically gets corporate-owned
- 🍎 Apple Automated Device Enrollment (ADE) - recommended
In terms of privacy, there are some differents between personal and corporate ownership, although this can be changed anytime in the Intune console on the device object.
Settings
Configuration aspects for macOS are familiar with in Intune since we also use configuration profiles, primarily settings catalog, but also templates. Take a look at this resource There is support for: Device features, restriction, Endpoint protection, Extensions, certificates (PKCS & SCEP), Preference files, Software updates, VPN and Network.
Apple also promotes DDM - Declarative Device Management, which is an improved protocol for device management. We can expect more and more settings through this new method. It brings a desired state concept, more autonomy and increase of performance and scalability. Read more
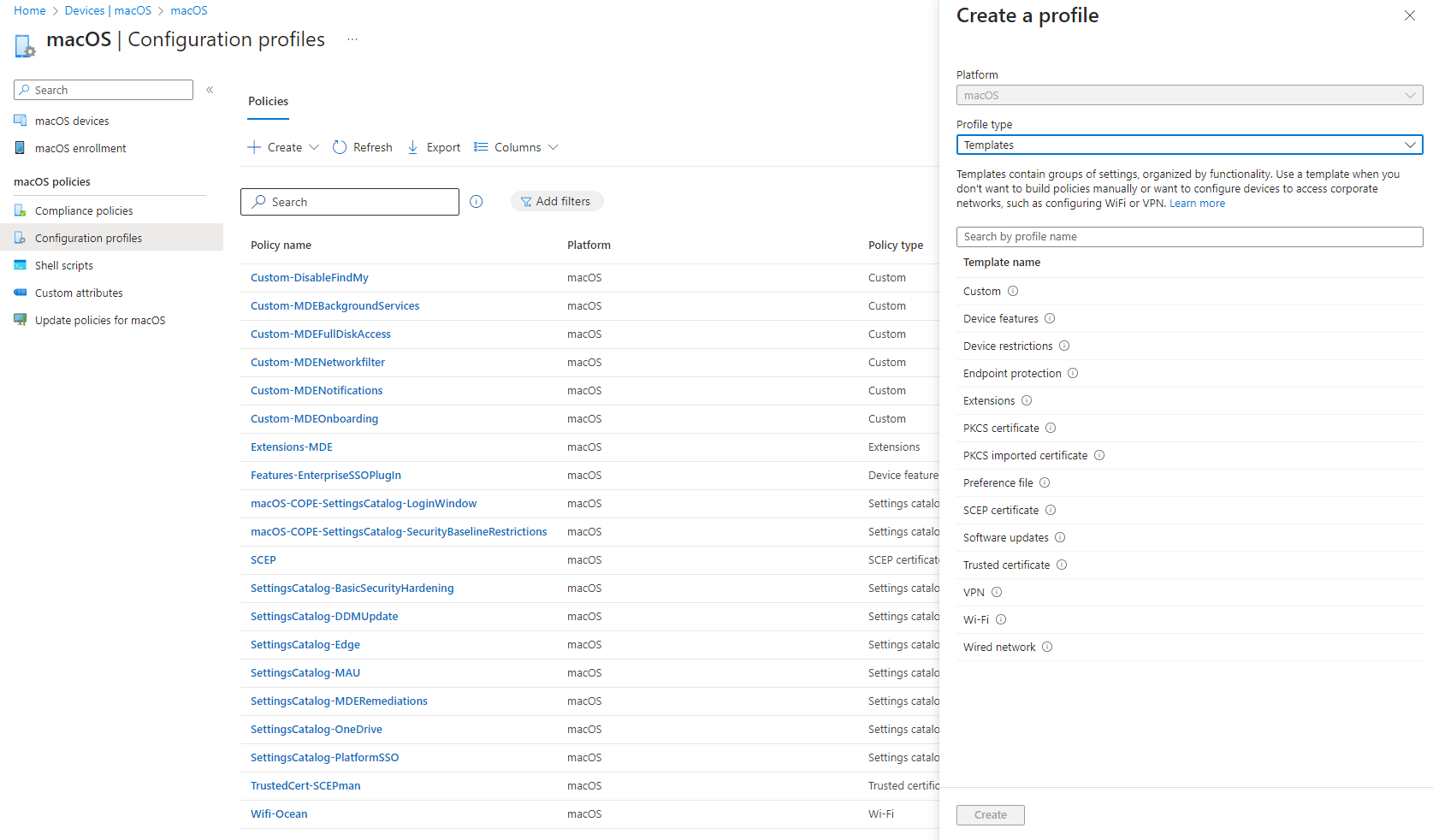
Shell scripts
Additionally we have Shell scripts (comparable to Platfrom scripts of Windows) and a specialty called Custom attributes. Again based on Shell scripts we can retrieve device specifc values of attributes such as the count of BatteryCycles or Defender status. Here you can find a lot(!) of samples:
Custom attributes
Custom attributes are shell scripts that read out a system value in a string, integer or date. This is practical for custom inventory data or retrieving a status on the system.
Remote actions
Remote actions are familiar, to remotely control the Mac's that are enrolled to Intune. Depending, whether the device is personal or corporate, you have more options available:
- Retire - removes management and org data
- Wipe - removes all content
- Delete - delete from Intune, cut management connection
- Remote lock - lock the Mac
- Sync - sync device with Intune policies, scripts and apps and provide healt & status update to Intune
- Restart / Shut down
- Disable activation lock - disables the activation lock (feature that every Mac uses to contact Apple servers to check if it was locked)
- Rotate FileVault recovery key
- Rename device (corporate only)
- New remote assistance session
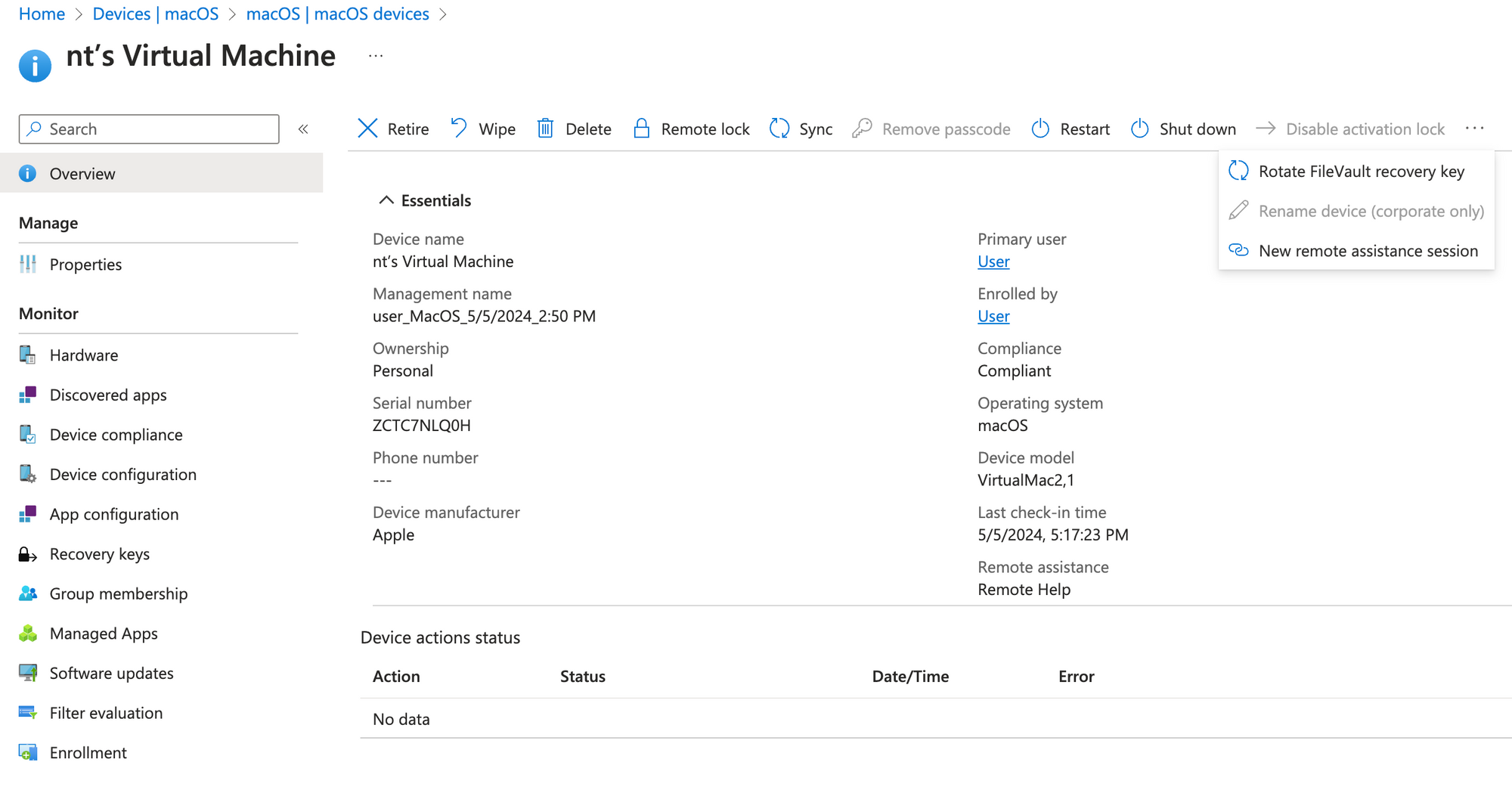
Security
Security is an essential part when opting in to Mac management. Without proper security controls in place, corporate data could be exfiltrated from the platform.
Mac security
Learn about Apple Platform Security on macOS. System security is comparable to other OS, but other services and features come to play. I have put some key topics together from Apple:
- Hardware security
Secure Enclave - The Secure Enclave is a dedicated secure subsystem integrated into Apple systems on chip (SoCs), Memory Protection Engine, Secure Storage, AES Engine, Public Key Accelerator, Face ID and Touch ID - System security
Secure Boot, Signed system volume, FileVault, Secure software updates, OS Kernel and system integrity protection, Direct memory access protection - Encryption and Data protection
Passcodes and passwords, Keybags, Sealed key protection, FileVault, Access control lists - App security
Mandatory code signing, Sandboxing, Gatekeeper, Notarization by Apple, XProtect - Services security
Apple ID and Managed Apple ID, Two-factor authentication, iCloud security, encryption - Network security
TLS, IPv6, VPN, Wi-fi, Bluetooth, ultra wideband, single sign-on, Airdrop, security, Firewall - Developer kit security
HomeKit, SiriKit, DriverKit, ReplayKit, ARKit security - Secure Device Management
Mobile Device Management, Apple configurator security
From the Guide
MacOS security frameworks for endpoint security
Security frameworks are a set of best practices, recommendations and guidance from security experts and official institues to ensure the system is hardened against common attacks, ensures that security weakspots are mitigated and give the consumer a safe platform to work on. These frameworks give a good starting point, when it comes to Intune configuration. Here is some advice:
- macOS Security Compliance Project
- Community hardening guide by Hubert Maslowski
- NCSC guidance
- CIS benchmarks
- STIG
⚠️ Please verify that the baseline is intended for the latest macOS version.
Intune configuration
There is a good community guide about macOS Security hardening with Microsoft Intune. The tools that you need are:
- Configuration profiles / settings catalog and mobileconfig files
- Endpoint security
- Antivirus: Defender
- Disk encryption: FileVault
- Firewall
Ensure that the settings you configure are also successfully applied and you can verify it on the system.
Defender for Endpoint
MacOS devices can be onboarded to Defender for Endpoint for proactive monitoring, inventory insights and remote actions for security response. Furthermore, Defender for Endpoint can provide security recommendations and addresses vulnerabilities.
- Defender for Endpoint must be installed as app and configured through policies for advanced access to the OS
- Defender for Endpoint onboarding happens without any user interaction and can be fully configured by the admin in Intune
- Defender for Endpoint licenses are required
- Defender for Endpoint provides monitoring and response actions on macOS
Read the implementation guide on onboarding Defender for Endpoint on Mac.
Identitiy
On macOS we know different identity deployment models that come with different single sign-on flows. There is:
- Enterprise SSO plug-in - provides an SSO experience within all apps on the system that use Entra as identity provider and are supported
- 🆕Platform SSO - full SSO experience that syncs the Entra account credentials with the local account, that is used for login to the Mac + capabilities from Enterprise SSO plug-in
Compliance
In terms of compliance we can also use the familiar principle of compliance policies in Intune. Compliance policies evaluate the system state to ensure the system follows the policies and meets the corporate requirements.
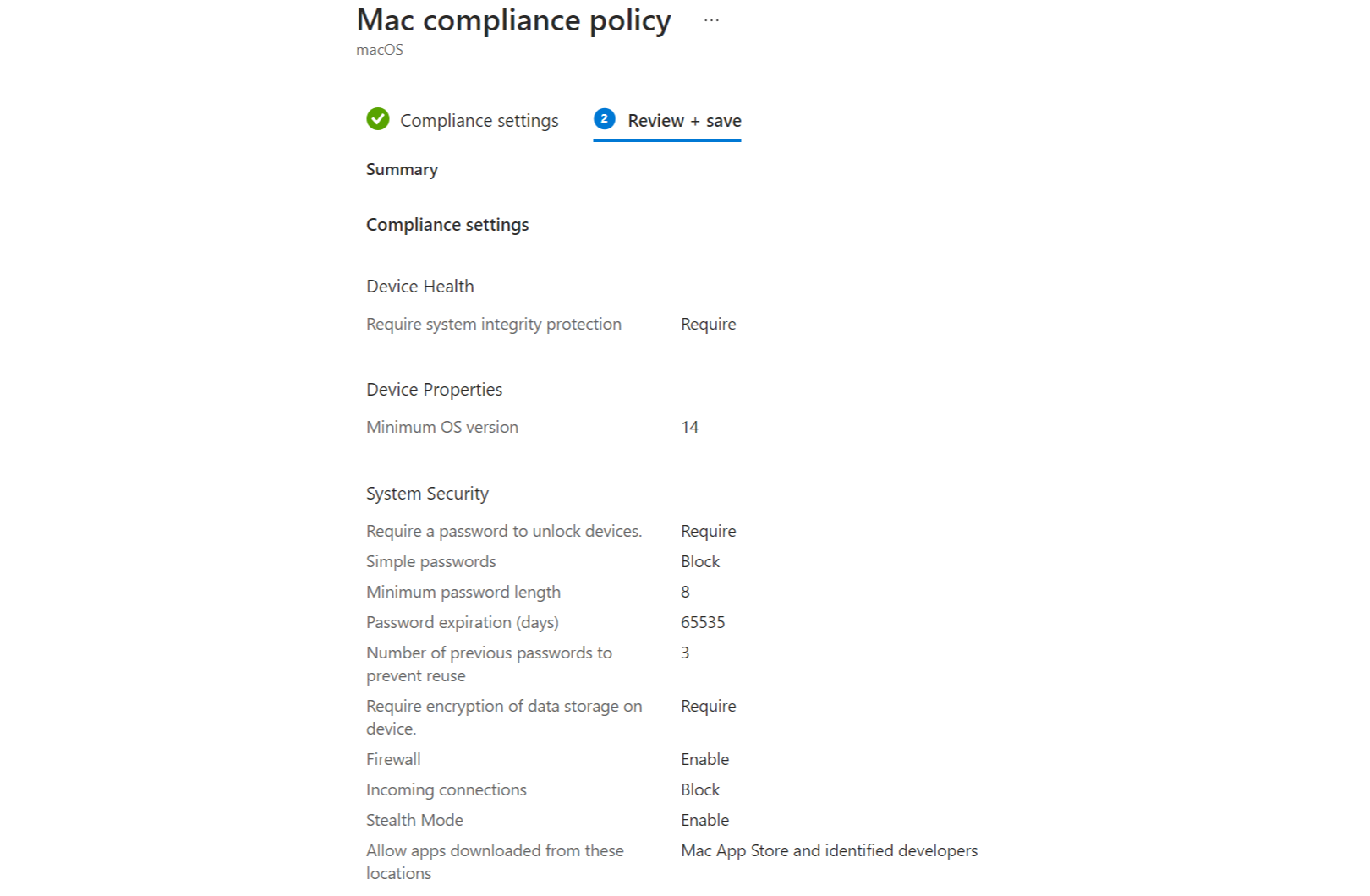
Apps
Apps are one of the primary reasons to go with macOS. Intune supports app management. Of course with Intune you can:
- Deploy apps from different repositories/stores
- Configure apps and monitor the status
- Provide apps as available from Company Portal
For an organizational perspective the motivation can be:
- Control apps for management or security reasons
- Provide the best user experience by installing the apps he needs to get productive
Types
There are different sources with different behaviors to get apps from:
- Built-in in Intune: Microsoft 365 Apps, Edge, Defender for Endpoint
- Web clip or link (just a shortcut to a URL)
- Apple Volume Purchase Program (VPP), requires Apple Business Manager - apps are 'aquired' there and synced to Intune
- macOS types
- DMG = Disk Image, basically just an application file
- PKG = Package, more configuration options (insatller behavior)
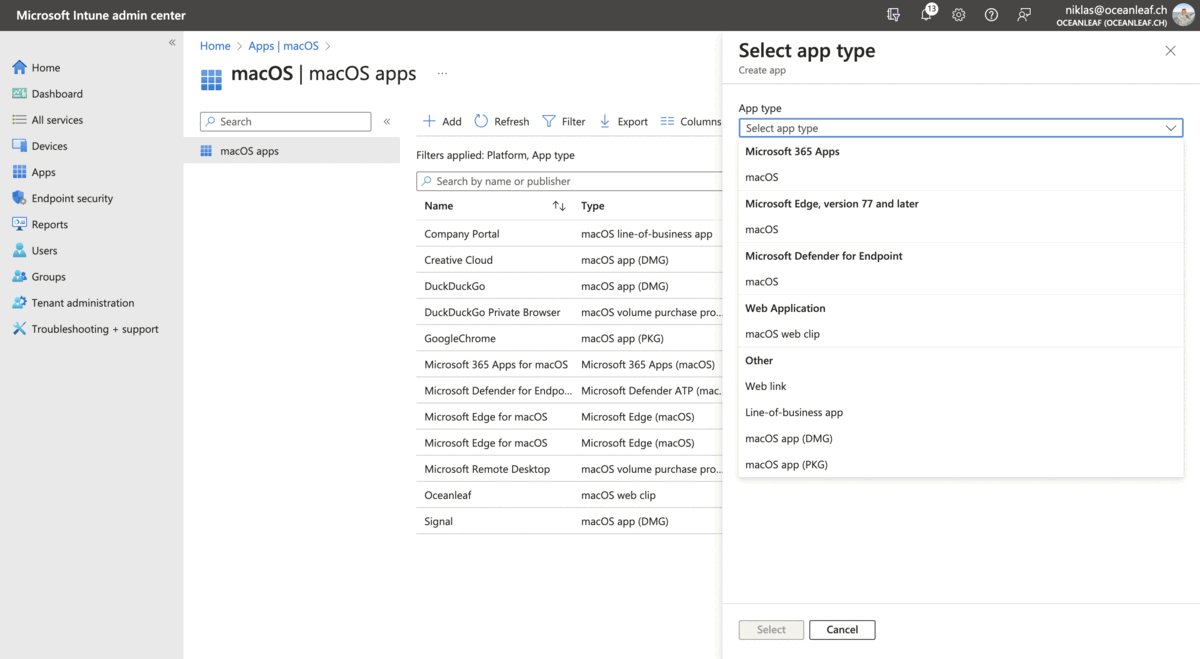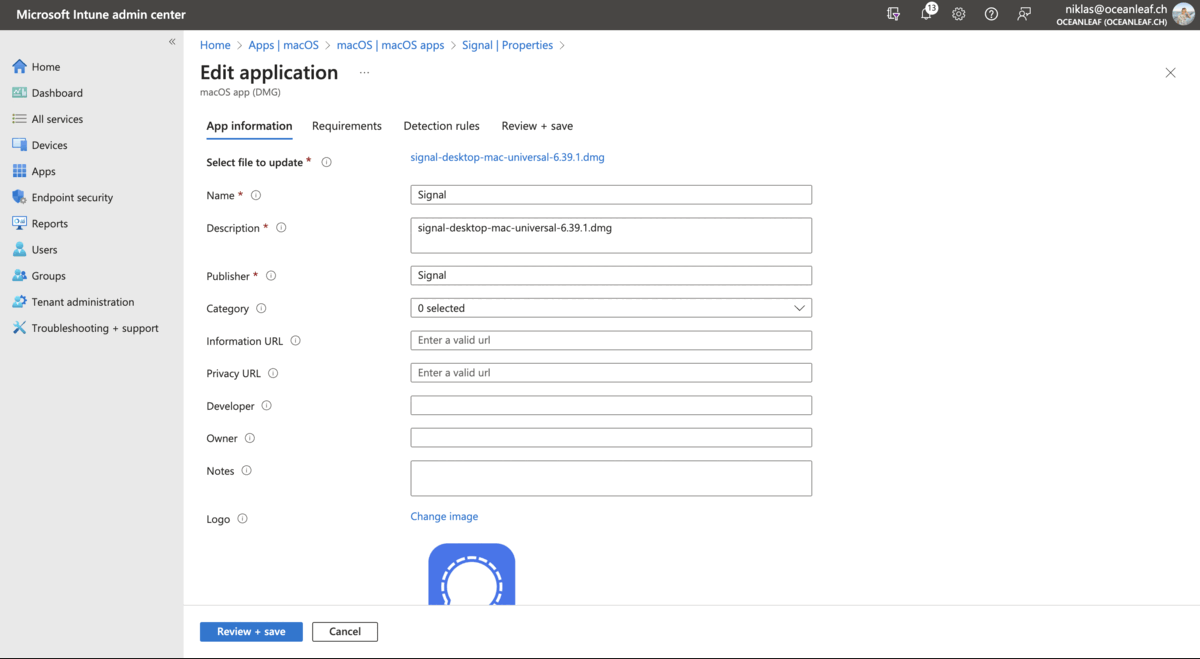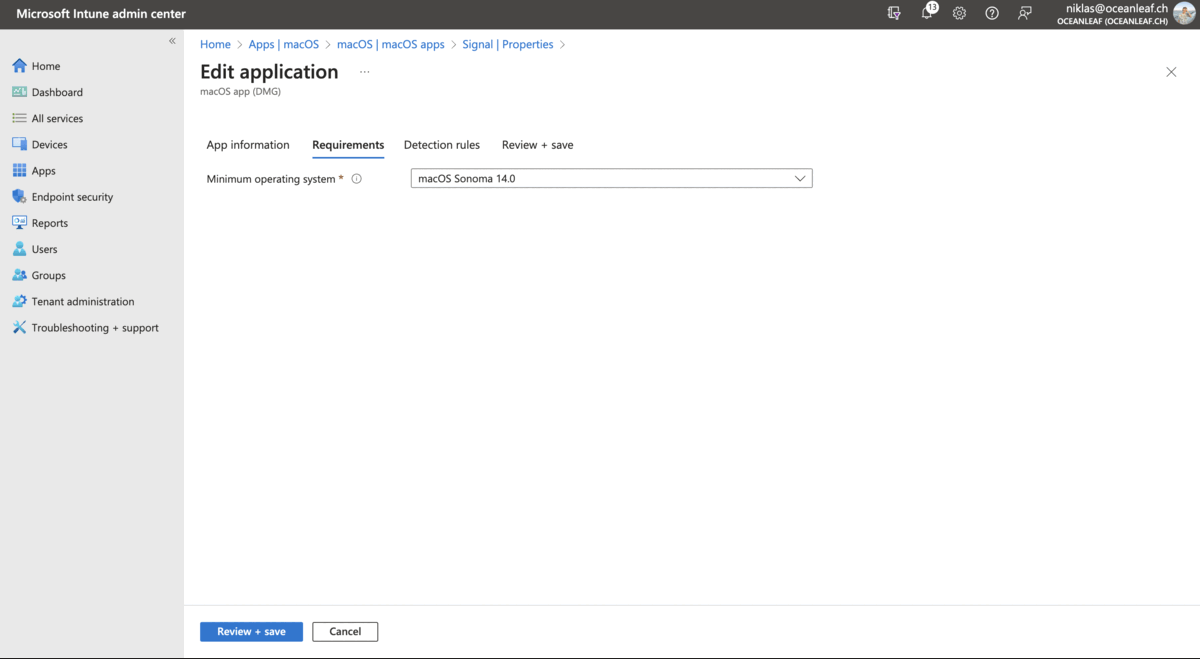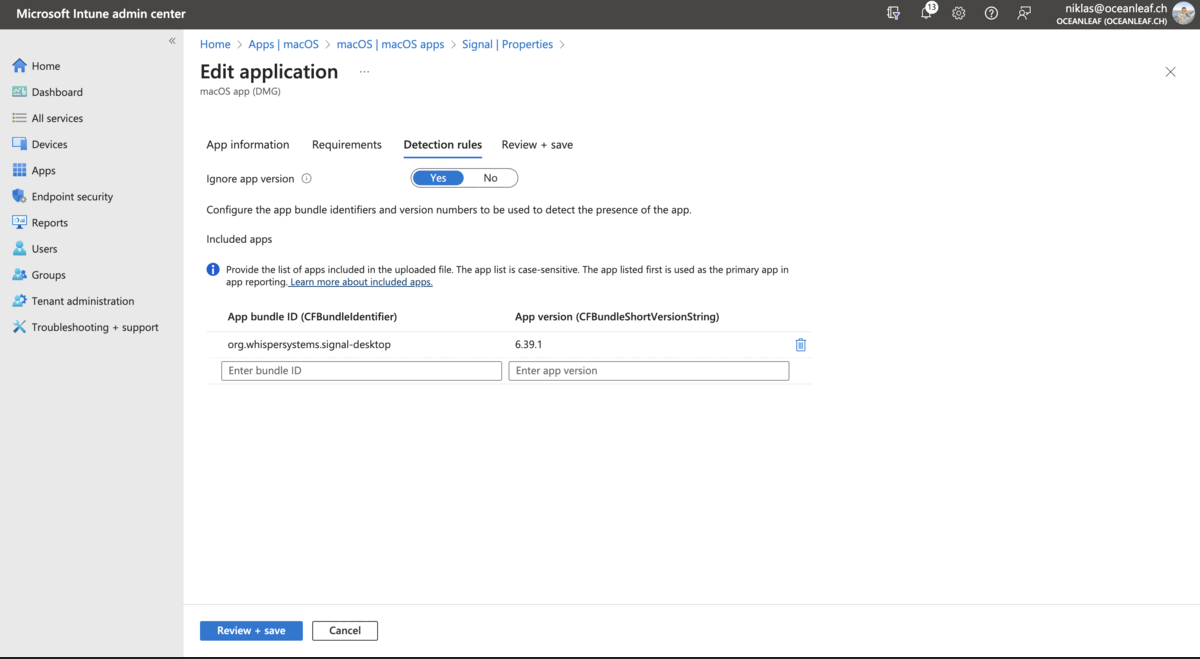
Also to recommend is again this GitHub repo. These apps are deployed as scripts and from my experience this is pretty reliable.

Resources
- macOS management with Microsoft Intune
- Community blog by Oliver Kieselbach
- Community blogs by Hubert Maslowski
- Session at Microsoft Technical Takeoff
- Microsoft Mac Admin Community



