Intune event based automation with alert rules
Introduction
In my last post I talked about Intune automation enlightenment with Azure Logic Apps. This time we will take a look on event based triggering to notify for alerting purposes or run Logic apps or other automation tools.
Components
- Azure Log Analytics Workspace provides the ability to store Intune audit data and query it with KQL.
- Azure alert rules enable us to bring in a logic to be triggered on an event.
- Azure action groups can notify individual recipients thorugh multiple channels or trigger other actions like Automation Runbooks, Azure Functions or Logic Apps etc.
Concept flow
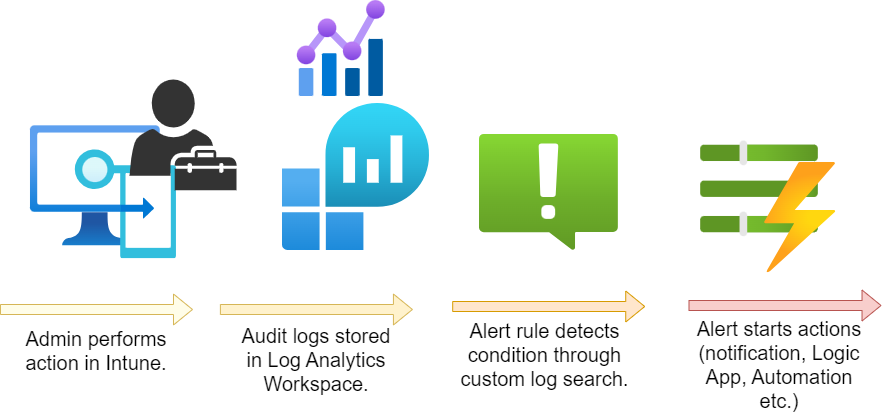
So this is a sample for a concept flow on how to use these features. Please note that this post only introduces the functionality and that there are a lot more use cases that may be more useful.
-
When an admin performs any action, that will create an Audit event. (Similar to all other events in Intune including data from OperationalLogs, DeviceComplianceOrg and Devices)
-
The Audit logs will be forwarded to a Log Analytics Workspace
-
The Alert rule is configured with a condition for custom log searches. This happens on a periodic basis. If the log search matches a custom defined threshold, the alert rule is triggered.
-
The action group makes a notification or starts other actions.
-
Optional: an Azure Logic App could take further actions.
Step-by-step instruction
Alert rule
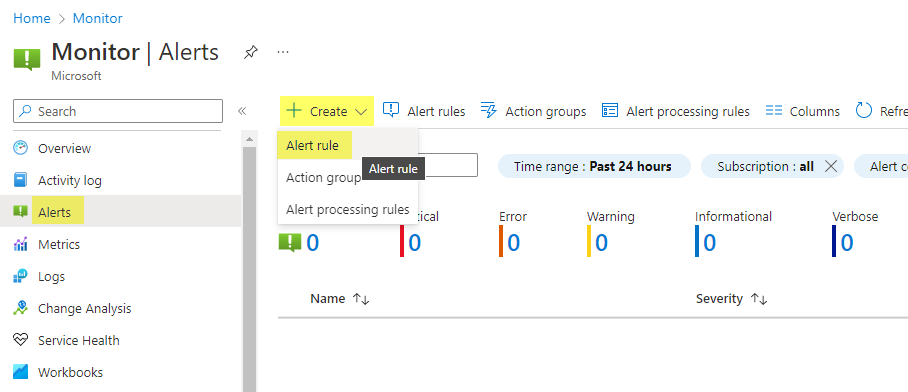
First of all navigate to Azure Monitor>Alerts and click on Create > Alert rule.
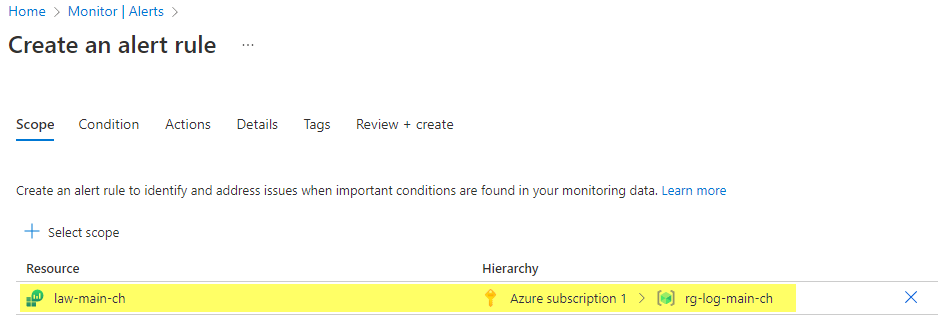
Select a scope -> this should be the resource path to your Log Analytics Workspace.
Add a condition > Custom log search. (there are already many predefined for other security related Azure activities)
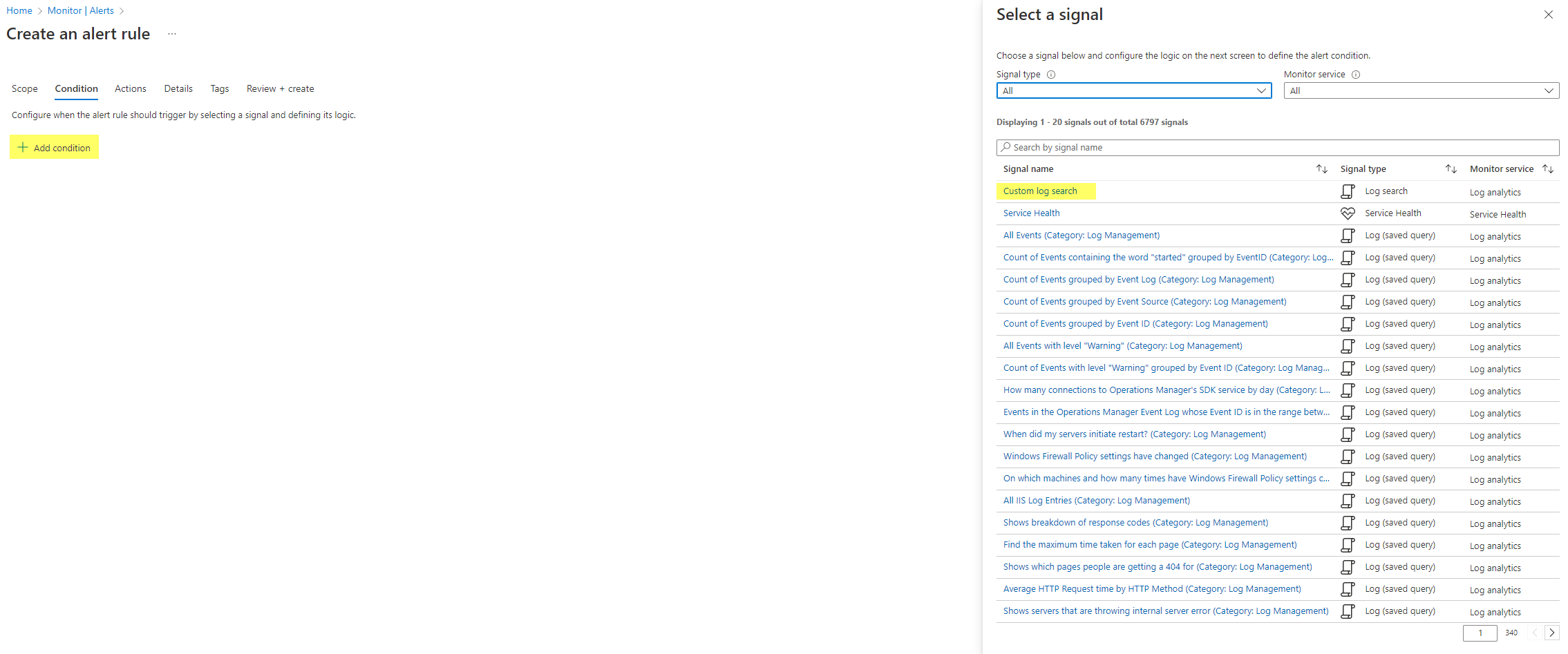
Next insert your custom KQL query that returns you the values or events that you need. I used an example to detect changes on Security baseline profiles.
IntuneAuditLogs
| where OperationName contains "Patch DeviceManagementIntent"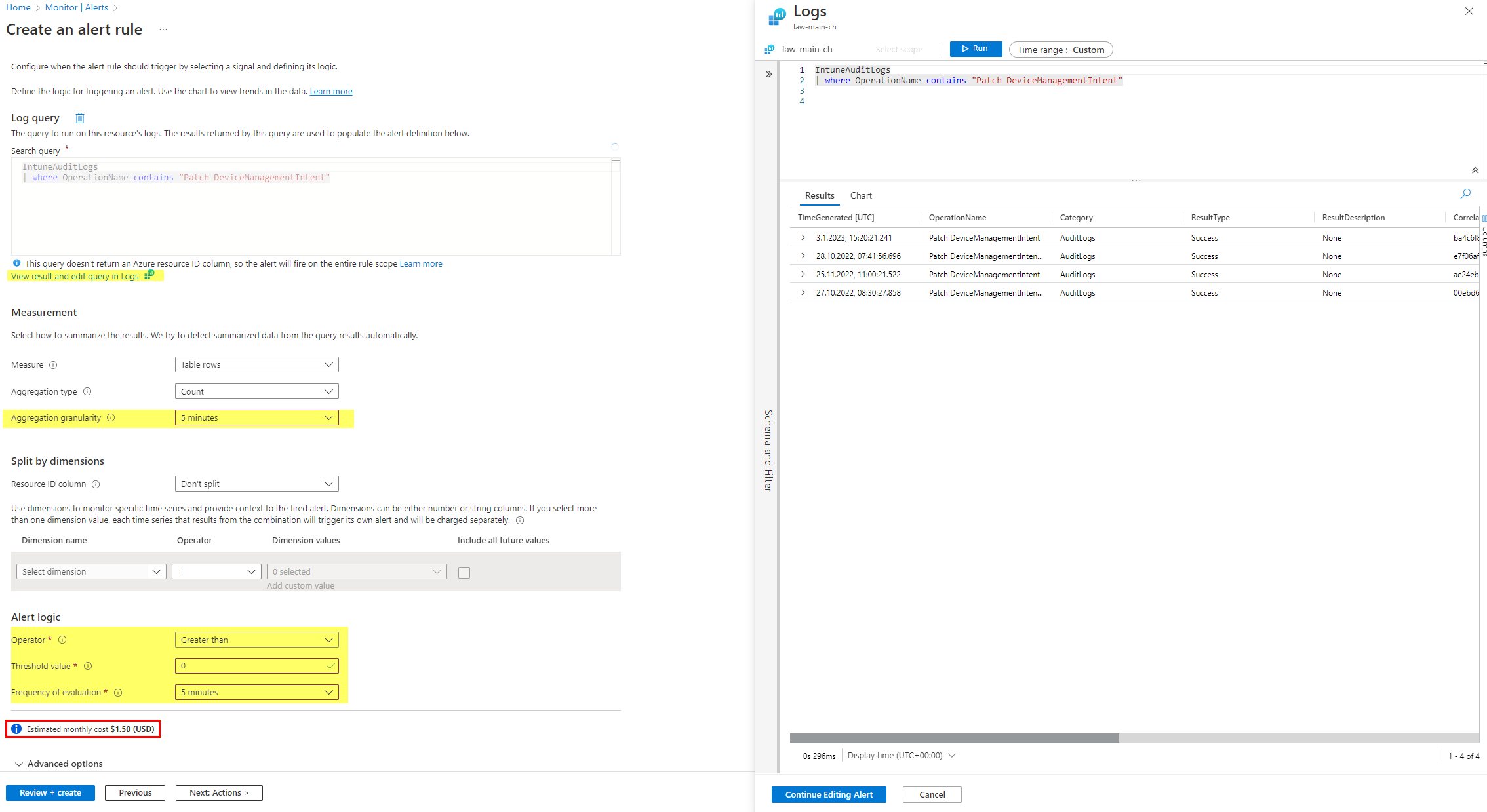
- Measurement
- Measure returned table rows or do a calculation on any numeric column, or simply put, the value
- Aggregation type is the measurement type (count, average, minimum, maximum)
- Aggregation granularity is the interval of which time the log results are used/groups (last xy minutes)
- Optional: Split dimensions allow to monitor for the same condition on multiple Azure resources
- Alert logic
- Operator is to compare with the threshold value
- Threshold value is the reference value
- Frequency of evaluation chooses how often the alert rule will be run
Then, the action group must be selected or alternatively can be created.
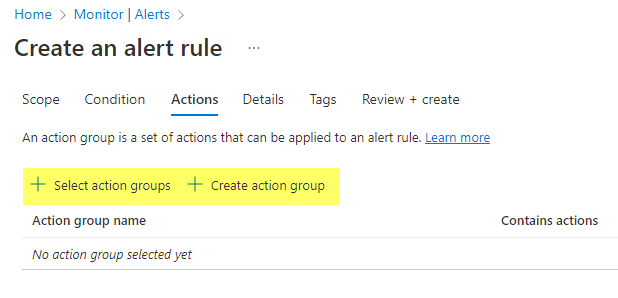
Simple action group
The action group creation is also straightforward. Basically it only has the use to define different notification recipients and to select action types that will be triggered.
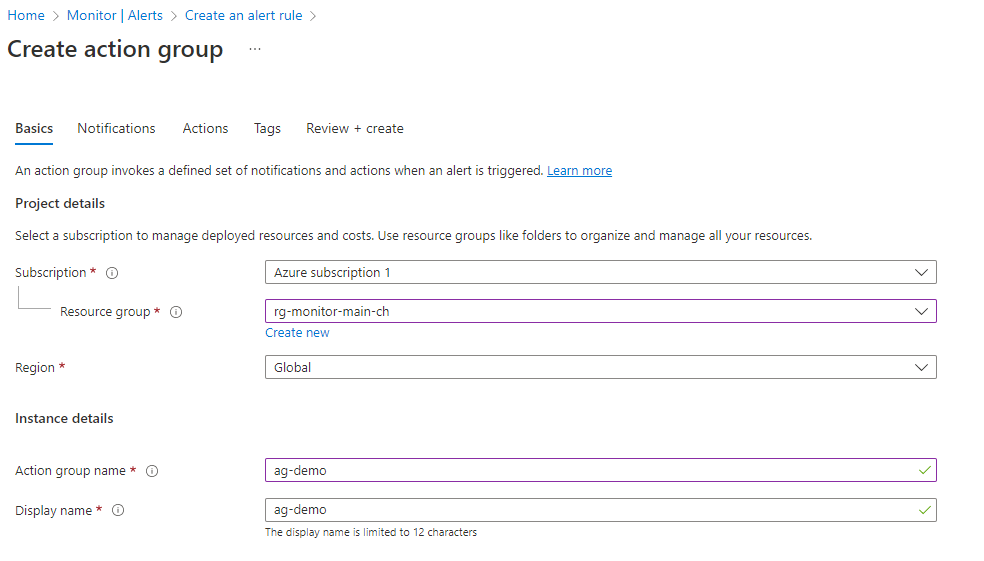
First up; the notifications, where we can choose if we want to notify the built-in Azure Resource Manager Role or notify own recipients.

Next, there are a set of action types - but you can also skip this. In the example below, I showcased a Logic App action.
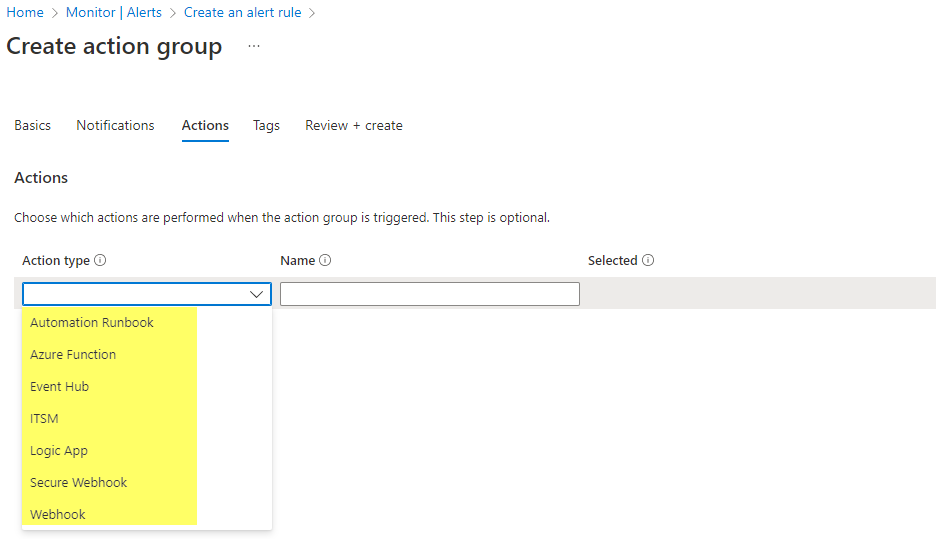
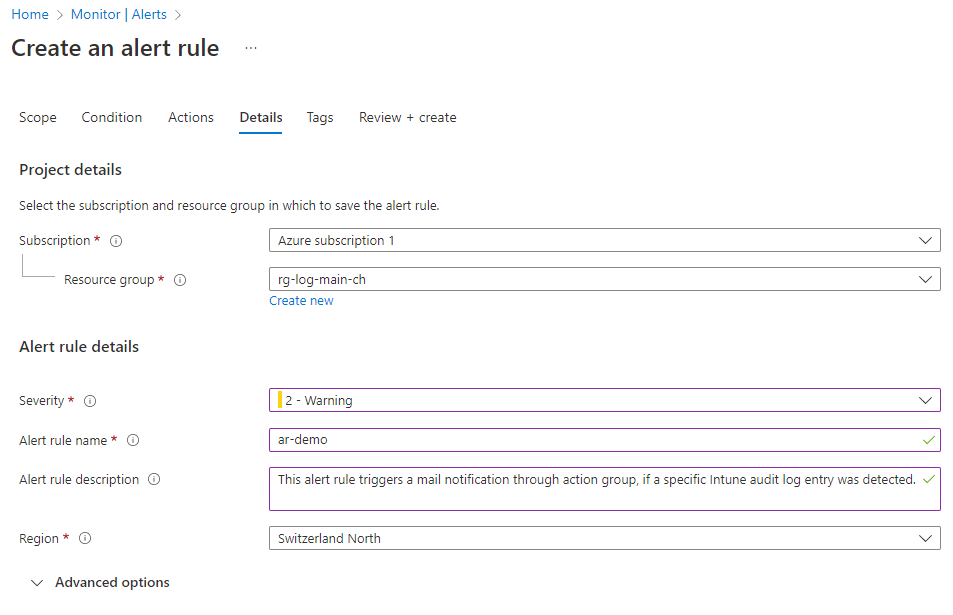
Last you need to enter some details and severity level to the alert rule.
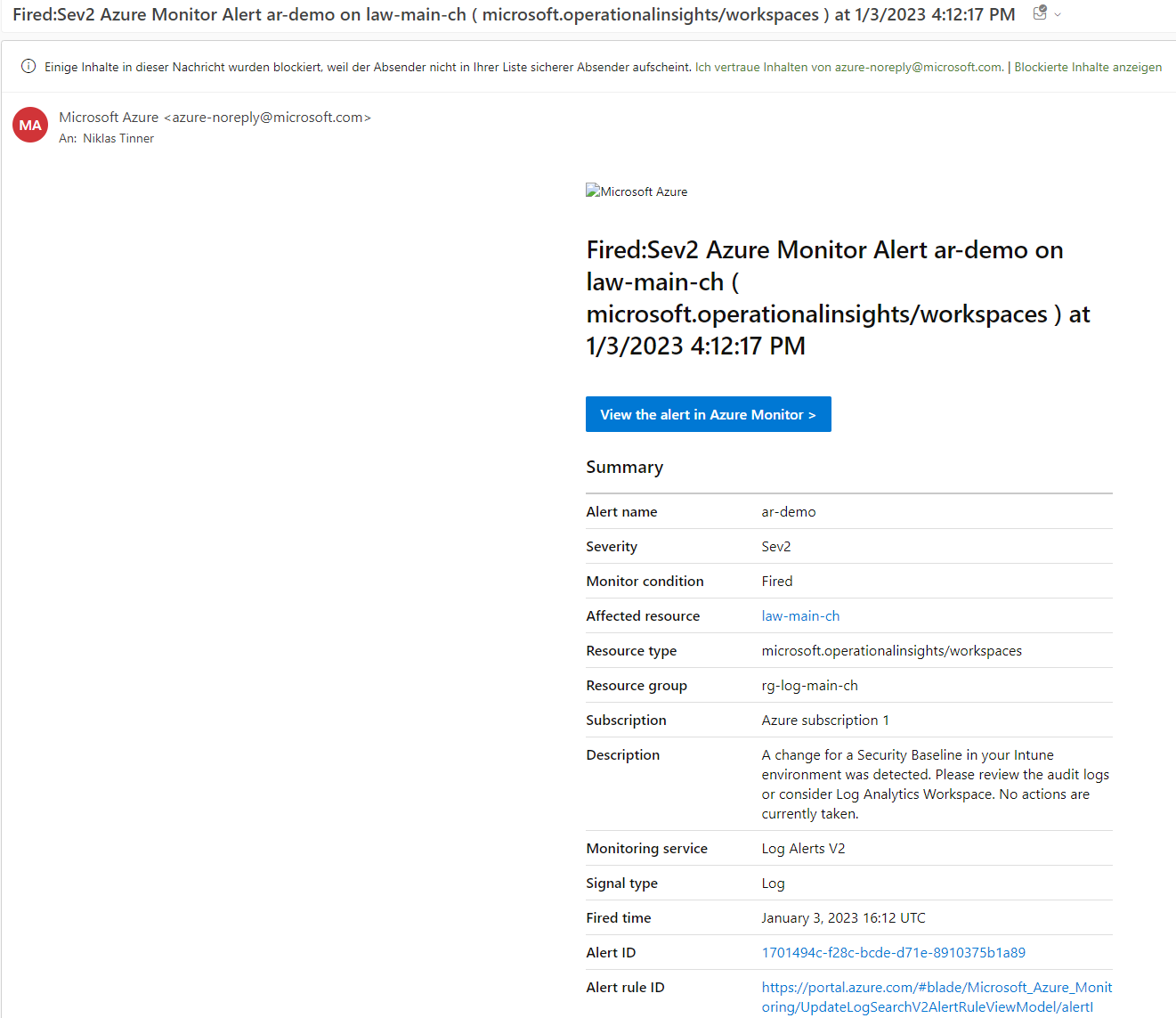
Result: mail notification
This resulted in the following email sent to me. I also customized the description of the alert rule to make it a little more understandable. Unfortunately you can't supply more information.
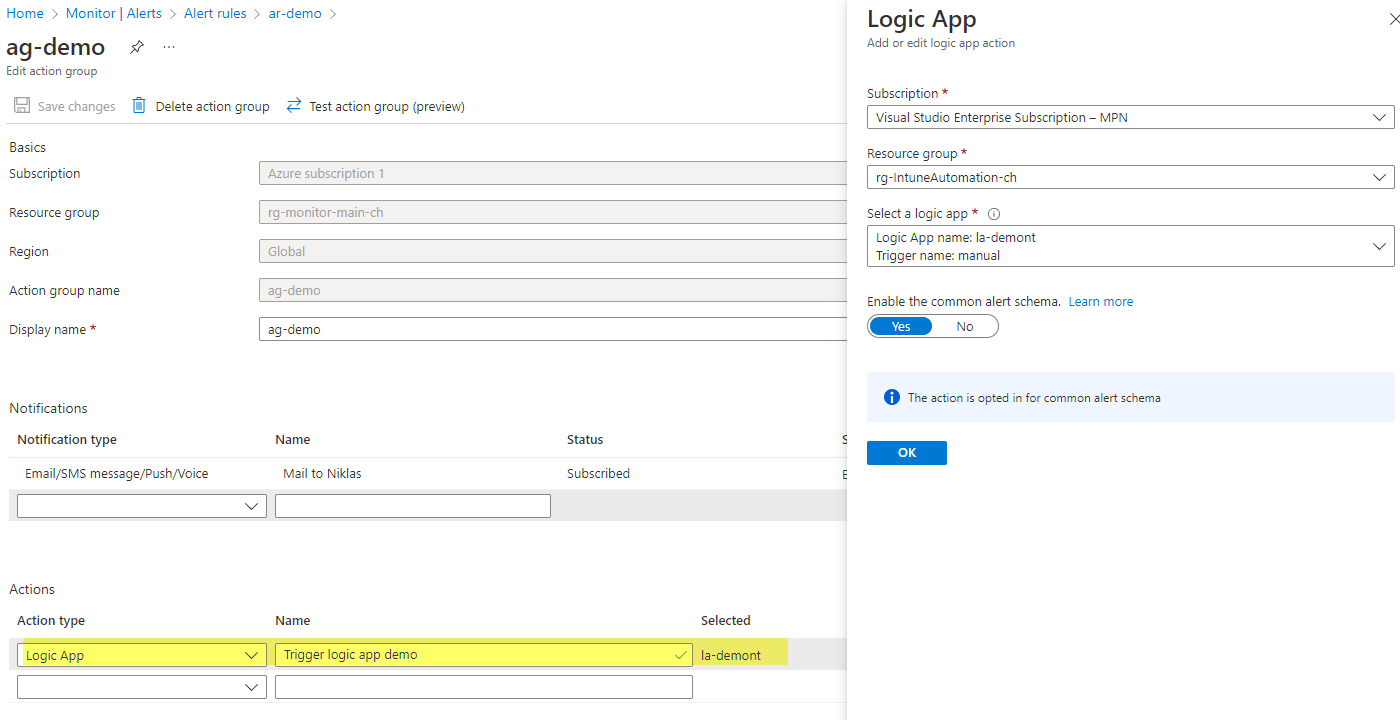
Logic app action trigger
In this example I will add a Logic App action to the action group. You only need to select the Azure subscription and desired Logic App - it will automatically resolve the webhook that will be hit up in the background.
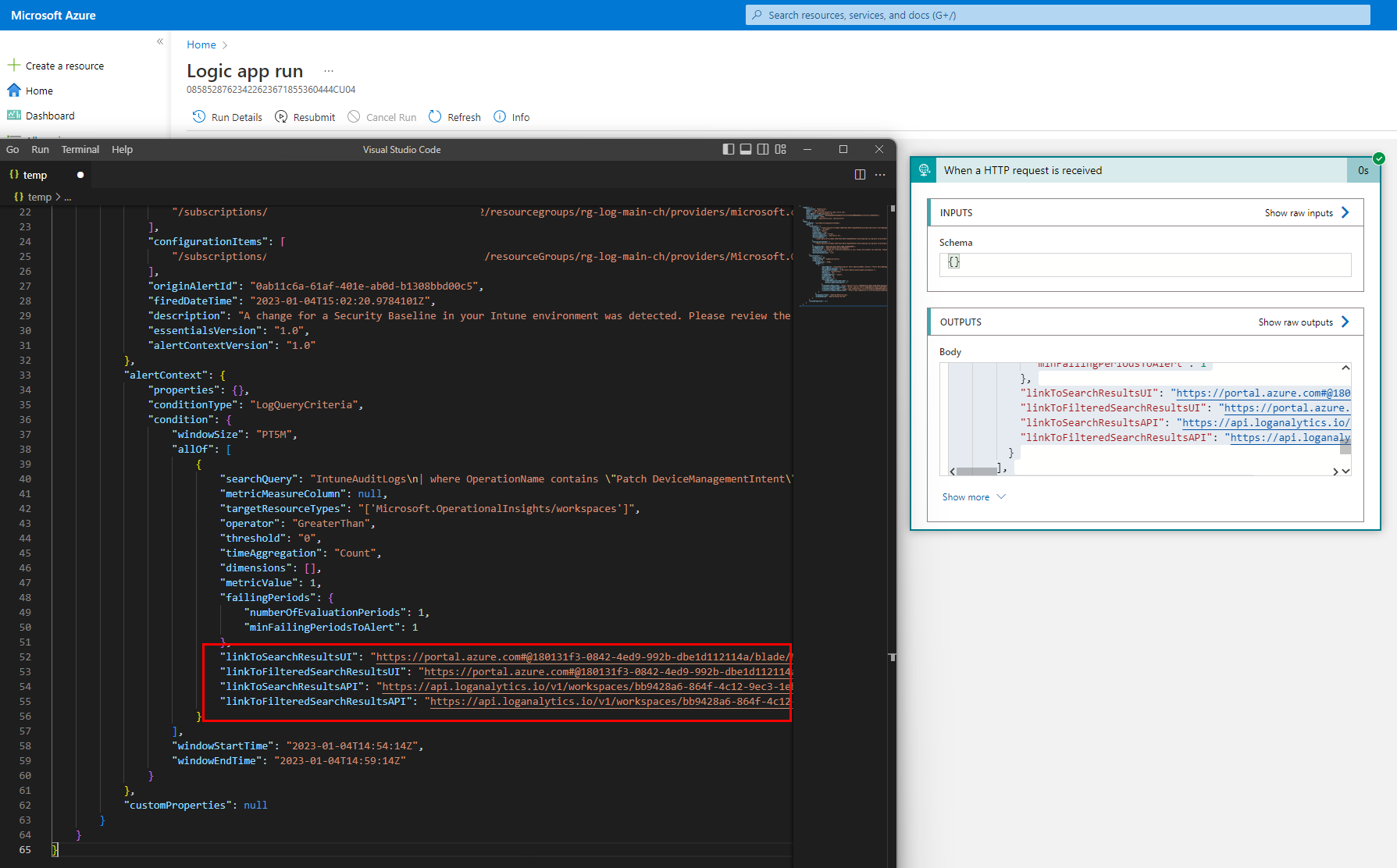
Result: webhook data
So if the action group was triggered, the Logic app run shows the webhook data. I think the most important ones are the link to the query, which might be used in further steps. (red lined)