Entra B2B & External ID Discovery
Introduction
Working with people outside of your organization, whether customers, partners or other companies, is part of the everyday business in a connected world. With Microsoft Entra, digital collaboration becomes secure and manageable. It helps to establish digital trust, lets teams share content, work together across company borders and stay protected while using SaaS apps from different vendors.
Microsoft Entra is Microsoft's cloud identity platform that powers identity and access management (IAM) for digital accounts inside or outside of your organization. It comes with lots of security features, including single-sign on (SSO), Conditional Access, Identity Governance (Lifecycle control), Tenant Trust, B2B Direct Connect and more. Microsoft Entra External ID enables external users to authenticate using their own identity provider while accessing resources in your tenant.
This article gives a clear overview of Microsoft Entra External ID by explaining the core features, real-world use cases and security considerations. At the end, there is also a ready-to-use community solution to help track and understand guest users in your tenant.
Entra External ID quickstart overview
Learn about the core principles to understand Entra External ID in this section.
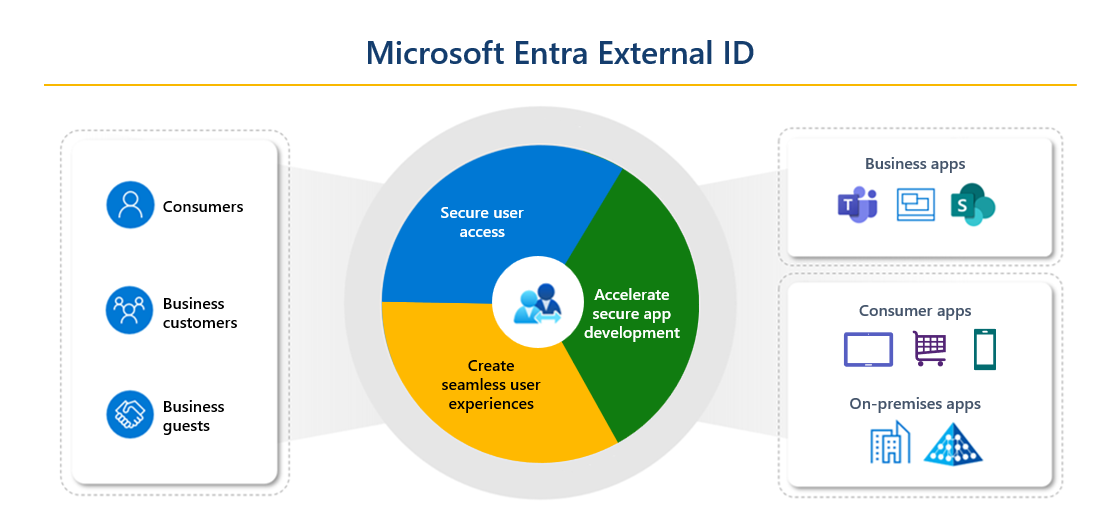
Use cases
Entra External ID consists of 2 primary use cases and differentiates in the feature capabilities, security considerations and target audience.
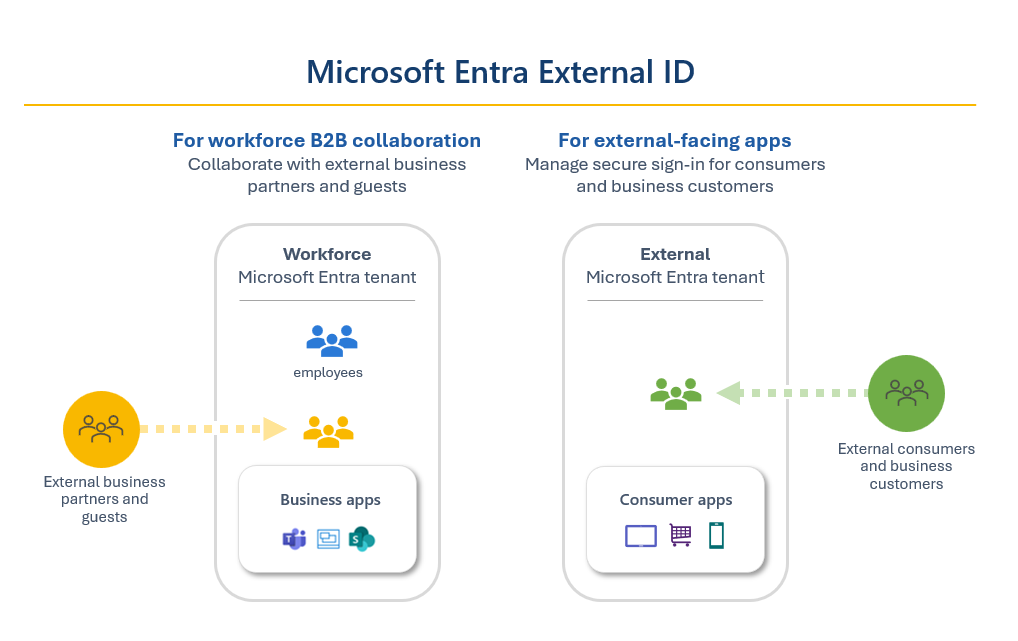
Workforce Tenants
Workforce Tenants are the familiar Microsoft Entra ID instances that manage your users, resources and applications. What makes it part of External ID is the ability to invite users from external, foreign Tenants, known as their home Tenant. Once the guest accepts the invitation, they get a digital identity in your resource Tenant and can authenticate using their existing credentials to access the resources you've shared.
- Single tenant, full identity security + governance
- B2B collaboration on enterprise apps (SaaS)
- Invite guests in other Entra tenants, Microsoft accounts (consumer) or other social identities
External Tenants
An external Tenant is dedicated to identity-related tasks for external users, typically consumers or business customers. It supports sign-up, authentication and access to apps and resources as part of a Customer Identity and Access Management (CIAM) scenario. Unlike a workforce Tenant, this environment is purpose-built for external audiences and is usually configured separately to keep customer and internal identity management cleanly isolated.
- B2C identity provider, separated tenant configuration
- Create new tenant in Azure subscription
- Integrate your custom apps and provide identity with external ID
- Self-service registration flow
| Workforce Tenants | External Tenants | |
|---|---|---|
| Description | Single Entra ID tenant to manage employees, apps and resources. Standard tenant, no additional setup needed. | Manage external identities and customers to your customer facing apps. (CIAM) Set up additional tenant for separation of identities and resources. |
| Primary use case and target audience | B2B Share and collaborate on business apps (mainly Microsoft 365 Suite) with external guests, partners, companies. | B2C (B2B) Provide an identity provider and integration to your custom apps for your customers. |
| User management | Same as in Entra ID - invite guest users and manage with Entra ID security stack features. | Create a new distinct tenant in an external configuration. |
| App access | Grant access to all (Enterprise) apps in your tenant, since users and guests are in the same directory. | Register only needed apps, separated from the workforce tenant. |
| Entra Security features | ID Protection, ID Governance, Self-service password reset, Conditional Access, Smart lockout, Custom banned passwords | Self-service password reset, Conditional Access, Smart lockout |
| Pricing | Monthly active users (MAU) billing model: https://learn.microsoft.com/en-us/entra/external-id/external-identities-pricing | Monthly active users (MAU) billing model or External ID pricing: https://azure.microsoft.com/en-us/pricing/details/microsoft-entra-external-id/ |
| Branding | Custom company branding and customization supported | Custom company branding and customization supported |
| Invitation of guests | Invitation mail, Self-service sign up | Self-service sign-up or by admin, internal user invitation |
See the full feature comparison
B2B collaboration
Let’s take a closer look at what most organizations will encounter in practice: B2B collaboration within their workforce Tenant. This scenario typically arises when a business wants to share Microsoft 365 workloads with external partners. Common use cases include:
- Inviting partners to internal Microsoft Teams channels for joint projects
- Granting access to SharePoint sites or shared OneDrive document libraries
- Allowing contractors to use internal apps via Entra ID SSO
- Giving suppliers limited access to internal project or planning tools
These scenarios benefit from Entra External ID by enabling secure, policy-driven access without the need to create separate accounts for each external user.
Best practices
- Configure external collaboration settings (Guest settings)
Ensure, you review your external collaboration settings in your tenant. These settings are responsible for: Guest user access in your tenant, Invitation restrictions, Self-service sign up flow, External user leave settings, Collaboration domain restrictions. Review existing entries for allowed/blocked domains.
Furthermore, have a look at the available identity providers, from which users can sign-up and authenticate to access resources using their external identities.
- Review cross-tenant access settings
Check your default cross-tenant access settings in Entra -> External Identities and compare to default values. Additionally, verify if custom organizations are added and configure with custom settings. These include both inbound and outbound:
- B2B collaboration (users and groups, applications): Users can invite external guests to access your resources (inbound) and if they can be invited by other orgs and tenants (outbound)
- B2B direct connect (users and groups, applications): Advanced scenarios for collaboration such as Teams shared channels
- Trust settings: Trust whether your Conditional Access policies trust the signals of MFA, compliant or hybrid joined device from a foreign tenant (inbound only)
- Tenant restrictions: Advanced controls for outbound authentication traffic, e.g.; block access to specific foreign tenants
- Plan and evaluate cross-tenant synchronization
Cross-tenant synchronization in Microsoft Entra enables organizations to automatically provision, update and remove users across multiple Entra ID Tenants, ideal for subsidiaries, mergers or multi-tenant strategies. Unlike traditional guest access, users are fully managed in the target Tenant and can access apps without invitation prompts, getting a "like-home" feeling. Admins define user scope and attribute mappings in the source Tenant, while maintaining control through Entra security features like Conditional Access and entitlement management. This streamlines collaboration and strengthens governance in complex, distributed environments.
Discovery Workbook
For a recent project, I was in the need for a solution to monitor & analyze guest account behavior in my tenant. A perfect use case for Entra ID Monitoring, with Log Analytics Workspace, Azure Workbooks and KQL. This combination allows us to discover logs from the identity provider and visualize through queries in Azure Workbooks. The Entra ID Guest Account Discovery Workbook provides:
- Real-time insights into guest sign-in activity with advanced log search and visualization tools.
- Enables flexible log analysis using the timerange variable for deeper investigation.
- Converts Tenant IDs into domain names for better identification of guest users.
- Improves guest user tracking, risk analysis, and anomaly detection.
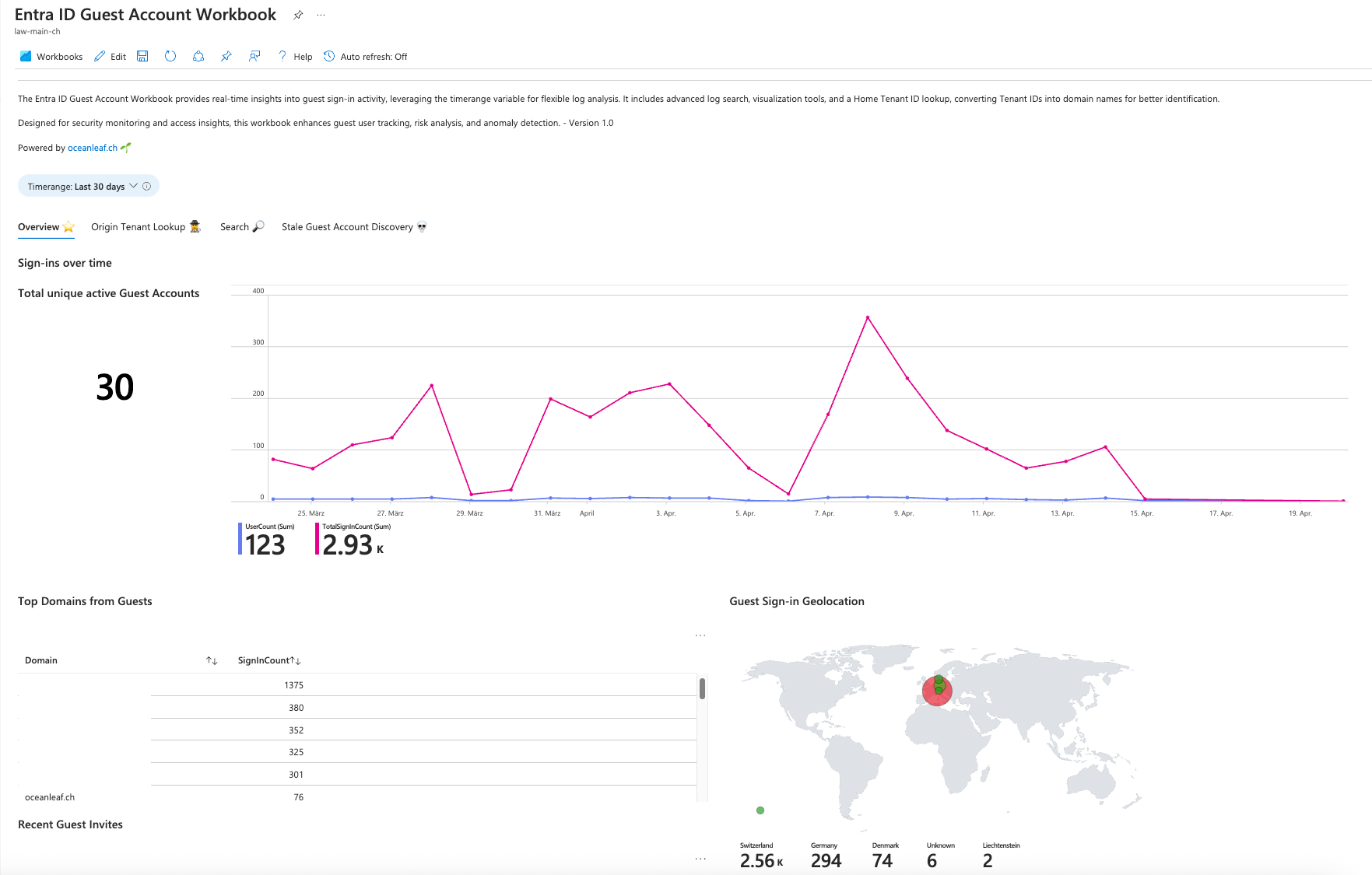
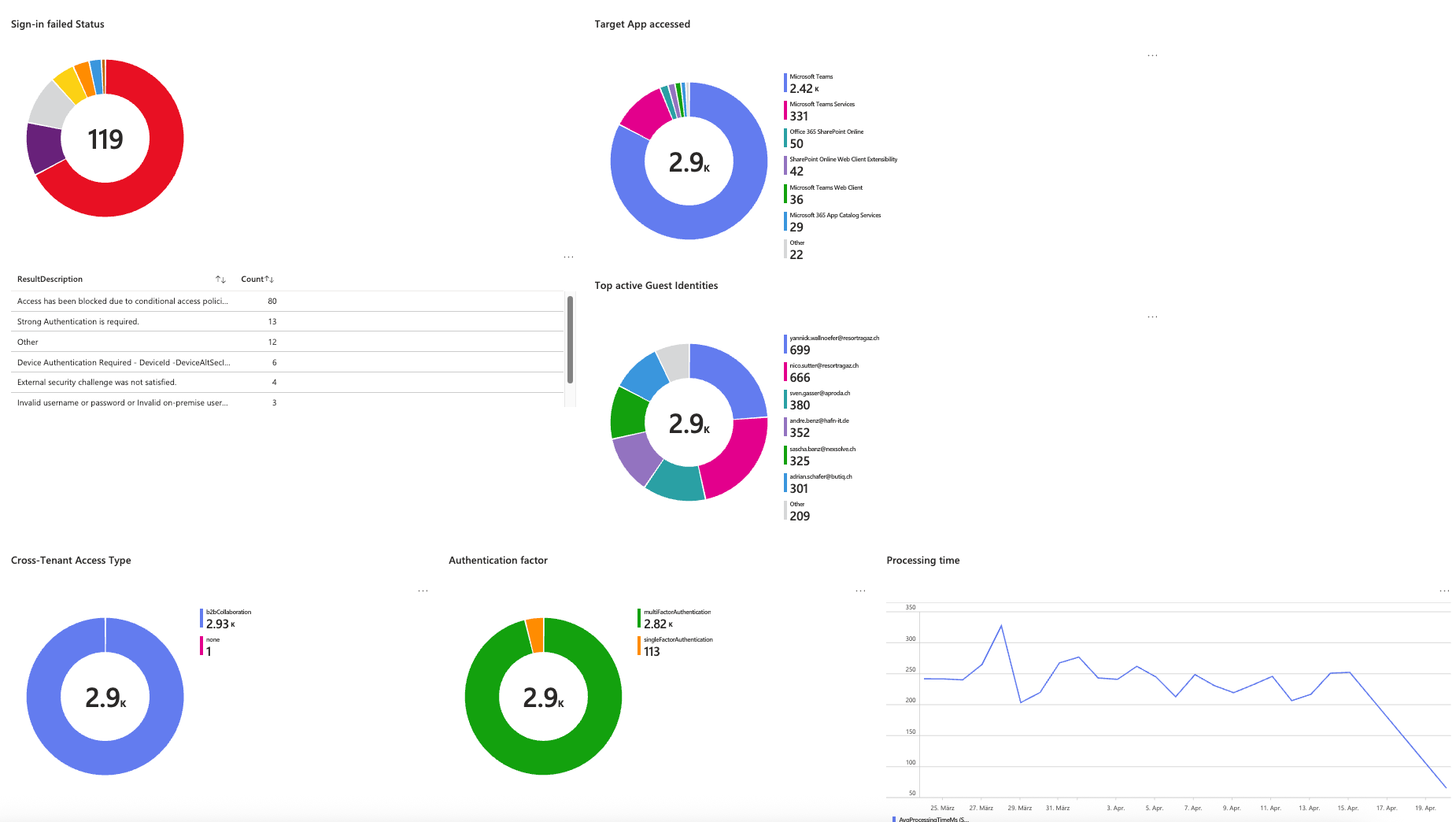
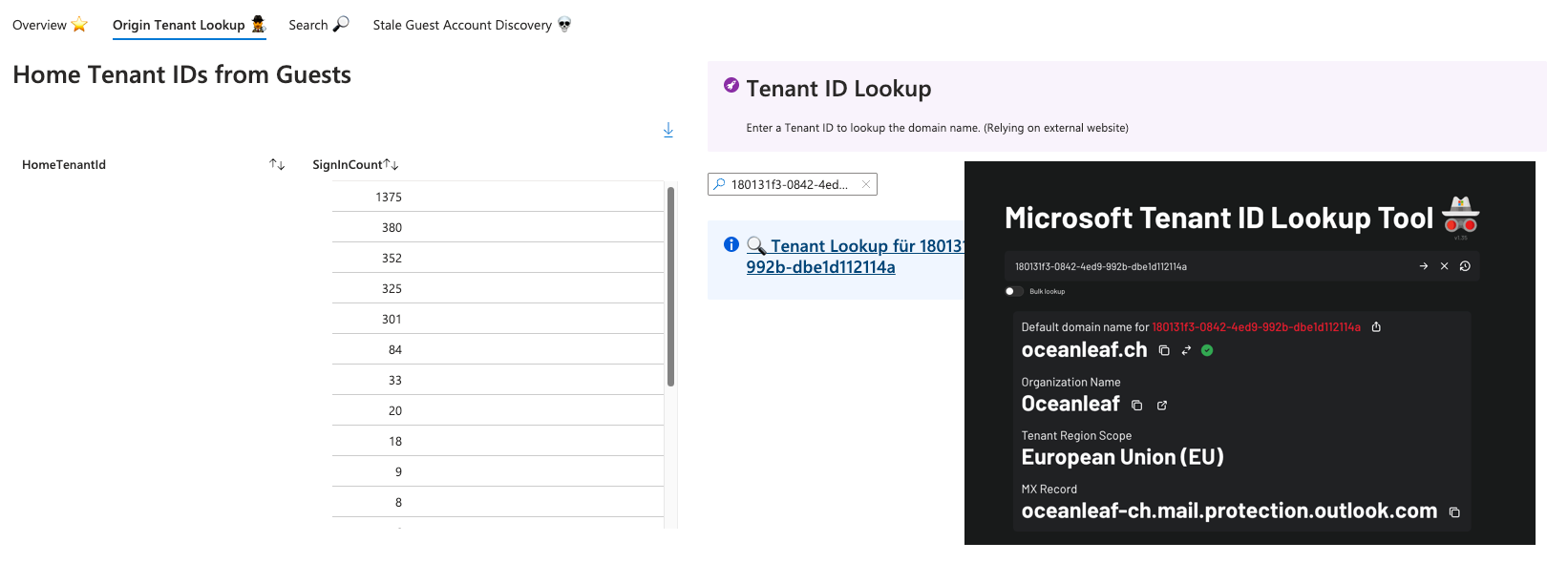
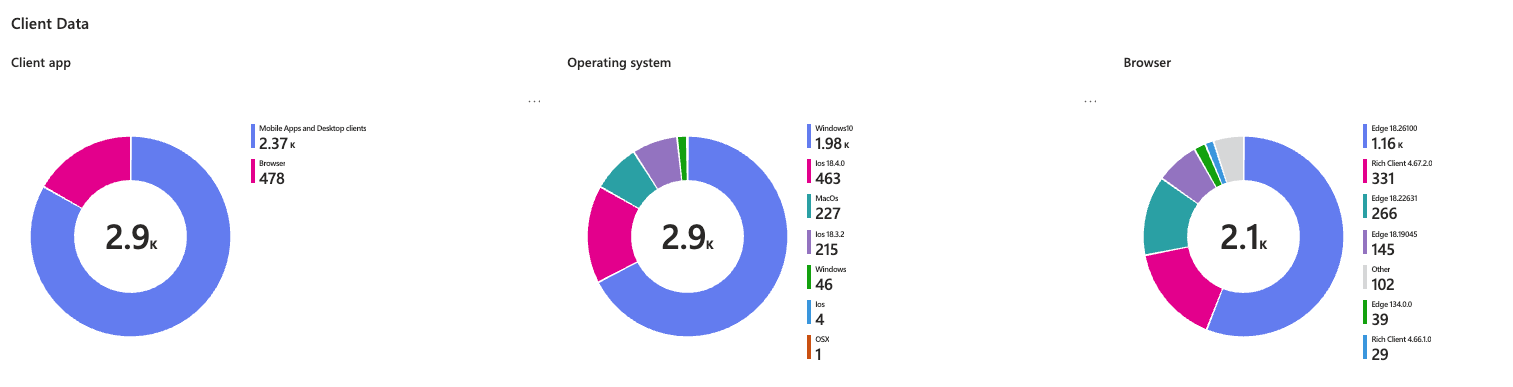
The Entra ID Guest Account Discovery Workbook consists of the following sections:
- Overview - General insights and visualizations for guest sign-ins.
- Origin Tenant Lookup - Identifies the home Tenant of guest accounts.
- Search - Provides advanced search options for guest account activities.
- Stale Guest Account Discovery - Detects inactive or stale guest accounts for better security monitoring.
Setup & configuration
I am providing this solution in my GitHub repository, read to import to your environment. Follow the steps in this video or down below:
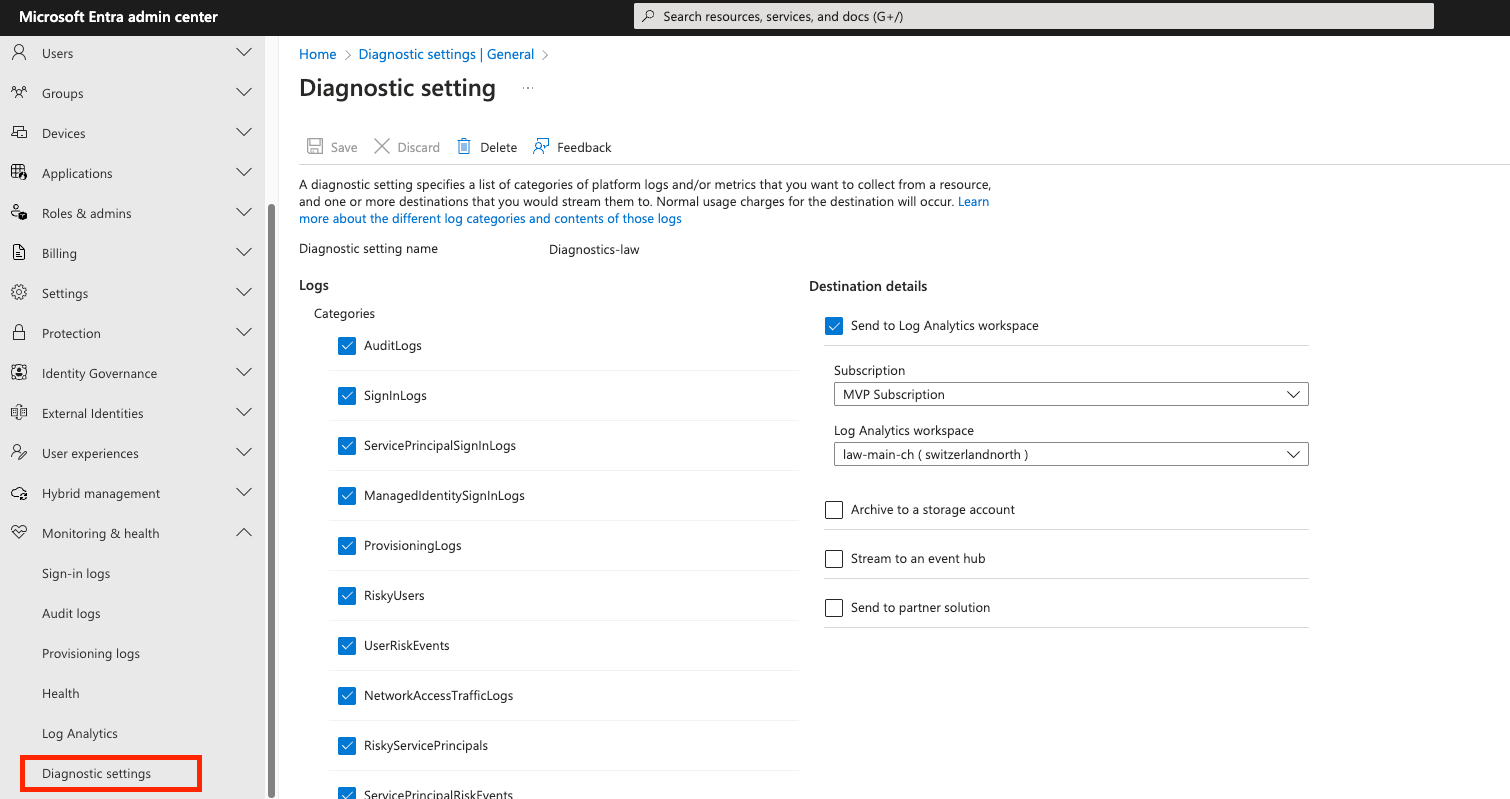
- Set up an Azure Log Analytics Workspace resource (including daily cap and data retention configuration!)
- Connect Entra ID diagnostics settings with that Log Analytics Workspace to instruct Entra to send logs to the workspace, so that we can query the data and use it in the workbook
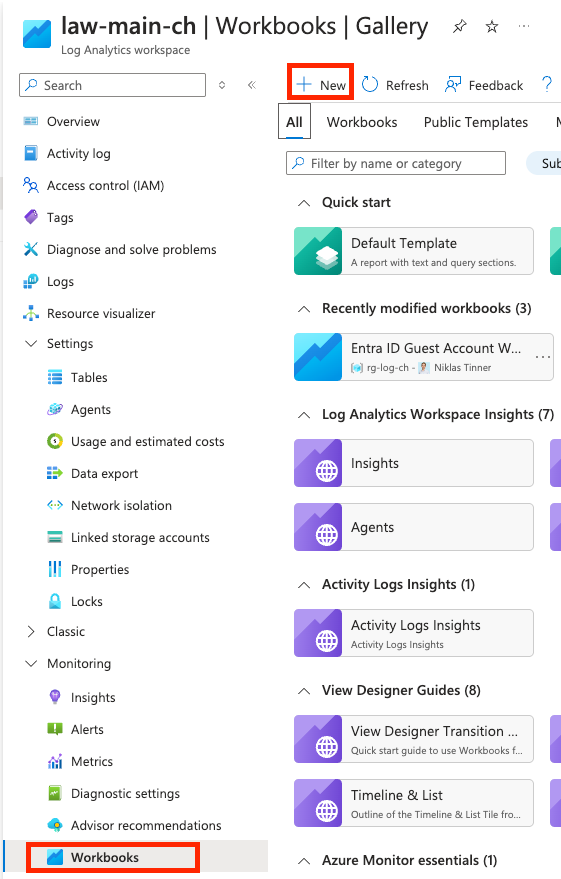
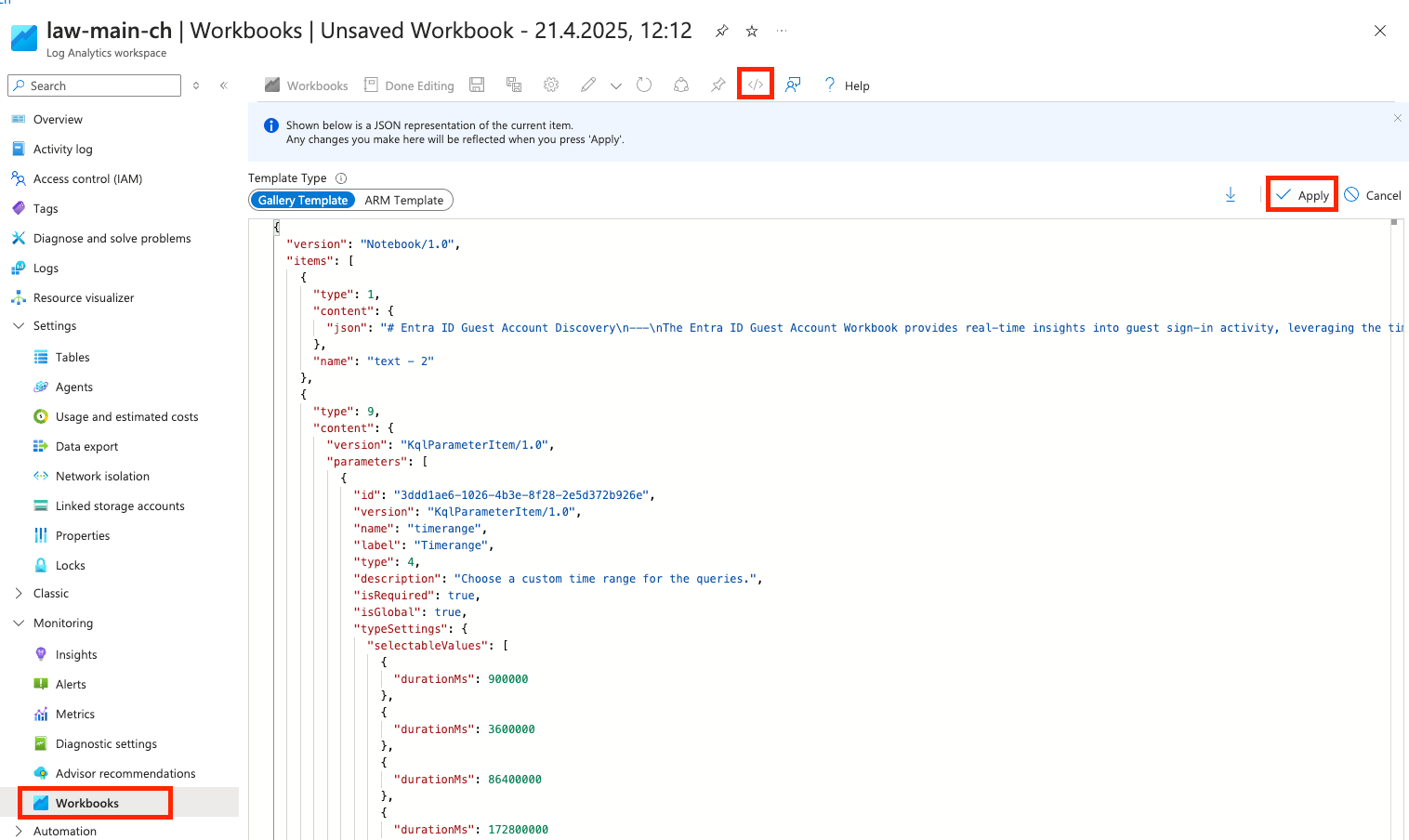
- Create a new Azure Workbook on the Log Analytics Workspace
- Import the workbook code from my GitHub repository template to your new workbook and save it
Powered by Oceanleaf


